Even with a certificate template for domain controllers that is supposedly simple to configure, there are a few things to keep in mind.
The certificate template should always start from the "Kerberos Authentication" certificate template.
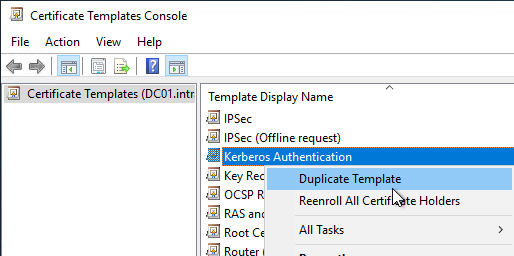
Only the Kerberos Authentcation certificate template contains the CT_FLAG_SUBJECT_ALT_REQUIRE_DOMAIN_DNS flag, which ensures that the domain name is entered in the Subject Alternative Name (SAN) extension of the issued certificate. See also article "Certificates for domain controllers do not contain the domain name in the Subject Alternative Name (SAN)„.
Certificate template configuration
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem and is available under a free license. It can downloaded via GitHub and can be used free of charge.
General" tab
A meaningful name is assigned to the certificate template in the "General" tab. A naming convention should be used here to simplify later administration.
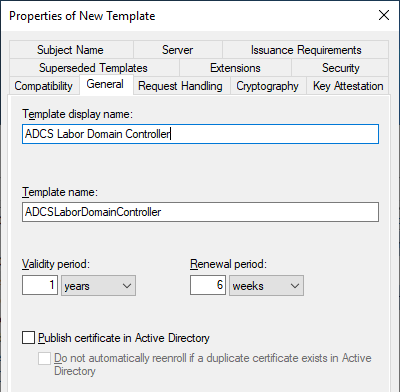
Cryptography" index card
The default settings can be left here. Even if elliptic curves via Key Storage Provider (KSP) can be used for the Active Directory domain services, this does not apply to the Active Directory Web Services (ADWS), which only support Cryptographic Service Provider.
It is therefore recommended to use the RSA algorithm with at least 3072 bit key length and to use a Cryptographic Service Provider.
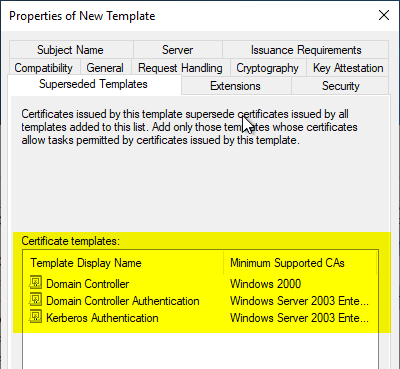
Superseded Templates Tab
The Superseded Templates tab is where all the default certificate templates for domain controllers are entered, as well as any custom previous certificate templates. The default certificate templates for domain controllers are:
- Domain controller
- Domain Controller Authentication
- Kerberos Authentication
See also article "Overview of the different generations of domain controller certificates„.
Extensions" tab
The "Application Policies" extension is being edited.
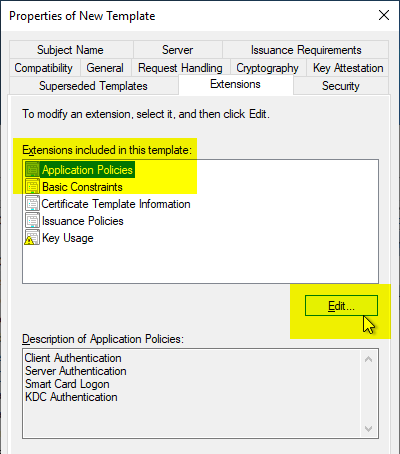
The following entries should always be removed:
- Client Authentication
- Smart Card Logon
Should it come to the issuance of forged domain controller certificates (e.g. through an NTLM relay attack or through Falsifying a corresponding account), the certificates cannot be used for a PKINIT logon on behalf of the domain controller (which could otherwise result in the Active Directory being compromised).
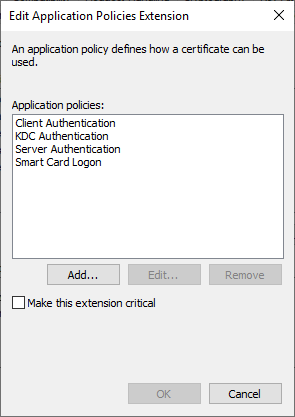
If you do not want to use PKINIT (also known as Smartcard Logon) across the enterprise, it is also recommended to remove the Extended Key Usage for "KDC" Authentication from the certificate template so that the domain controllers basically cannot process such logons.
If forged user certificates are issued (e.g. due to too extensive permissions on a certificate template, a insecurely configured certification authority or even their compromise), it is then not possible to log in with them (which could otherwise result in the Active Directory being compromised).
See also article "Attack vector on Active Directory directory service via smartcard logon mechanism„.
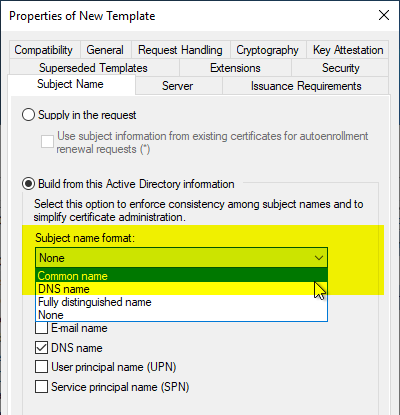
Subject Name" tab
The option is described in the article "About the "Build this from Active Directory information" option for certificate templates" described in more detail.
For compatibility reasons, it is recommended to set the "Subject Name" tab so that the subject of the issued certificates is filled with the server name of the domain controller ("Common Name" option).
By default, the subject will be empty, which is absolutely compliant with RFC 4514.
The client determines the type (e.g., DNS name or IP address) of the reference identity and performs a comparison between the reference identity and each subjectAltName value of the corresponding type until a match is produced.
RFC 4513 - Lightweight Directory Access Protocol (LDAP): Authentication Methods and Security Mechanisms
The server's identity may also be verified by comparing the reference identity to the Common Name (CN) [RFC4519] value in the leaf Relative Distinguished Name (RDN) of the subjectName field of the server's certificate. [...] Although the use of the Common Name value is existing practice, it is deprecated, and Certification Authorities are encouraged to provide subjectAltName values instead.
RFC 4513 - Lightweight Directory Access Protocol (LDAP): Authentication Methods and Security Mechanisms
However, applications that do not conform to this RFC (and such applications do exist in practice) will not be able to process the certificate.
If a subject is filled with the server name of the domain controller, and the application is compliant with RFC 4513, the subject is ignored anyway, so there is no disadvantage.
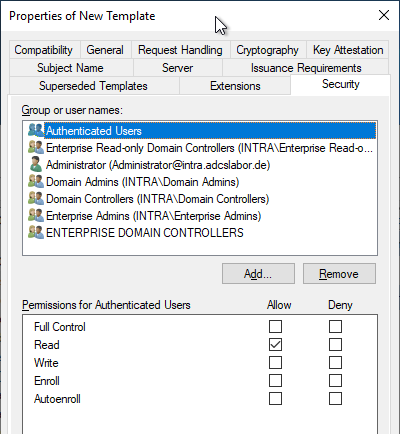
Security" tab
In the "Security" tab, it is important to ensure that only authorized persons can use the certificate template. edit can.
The rights for the certificate request can be taken from the underlying "Kerberos Authentication" certificate template.
Related links:
- Certificates for domain controllers do not contain the domain name in the Subject Alternative Name (SAN)
- Attack vector on Active Directory directory service via smartcard logon mechanism
- Overview of the different generations of domain controller certificates
- Changes to Certificate Issuance and Certificate-Based Logon to Active Directory with the May 10, 2022 Patch for Windows Server (KB5014754)
- Signing certificates bypassing the certification authority
- Active Directory forest compromised by EDITF_ATTRIBUTESUBJECTALTNAME2 flag
External sources
- RFC 4513 - Lightweight Directory Access Protocol (LDAP): Authentication Methods and Security Mechanisms (Internet Engineering Task Force)
- RFC 2818 - HTTP Over TLS (Internet Engineering Task Force)
10 thoughts on “Konfigurieren einer Zertifikatvorlage für Domänencontroller”
Comments are closed.