Windows Server 2008, along with NSA Suite B algorithms (also known as Cryptography Next Generation, CNG) with Key Storage Providers, introduced a new, modern interface for generating, storing, and using private keys in the Windows ecosystem.
In most cases, it does not matter which CSP or KSP is used for certificates. However, some applications will not work or will not work correctly if the wrong provider is chosen.
Below is a list of use cases I know of for certificates that only work with a specific Cryptographic Service Provider (CSP) or Key Storage Provider (KSP).
Use cases that only accept CSP
| Certificate type | Symptom/effect |
|---|---|
| Network Device Enrollment Service (NDES) Registration Authority Certificates | Service does not start because RA certificates are not found (events no. 2 and 10). |
| Intune Connector for NDES, Client Authentication Certificate | C:\NDESConnectorSetupMSI.log will record that the certificate private key permissions cannot be set ("AddNDESToCertPrivKey: Error 0x80090014: CryptAcquireContext failed with bad provider type 0x0"). |
| Active Directory Web Services (ADWS) and thus under certain circumstances Domain controller and Remote Desktop also | Event #1402 of the source ADWS is logged. The debug log is entered: "ProvisionCertificate: caught a CryptographicException: System.Security.Cryptography.CryptographicException: Invalid provider type specified.". The certificate selection already terminates if only one of the certificates in the machine certificate store does not use a CSP, even if this would not be usable for the ADWS at all. |
| Exchange 2013 Forms-based Authentication (FBA) Exchange 2016 (up to CU3) Forms-based Authentication (FBA) | After logging in to the FBA, you will be taken back to the login page. Certificate import can fail with error code NTE_BAD_DATA fail. |
| Forefront Identity Manager (FIM) / Microsoft Identity Manager (MIM) Certificate Managemt (CM) Agent | |
| Forefront Identity Manager (FIM) / Microsoft Identity Manager (MIM) Certificate Managemt (CM) Admin Key Diversify | |
| Forefront Identity Manager (FIM) / Microsoft Identity Manager (MIM) Certificate Managemt (CM) Key Recovery Agent | |
| Microsoft SQL Server | The RSA SChannel Cryptographic Provider is recommended |
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
Details: Intune Connector for NDES
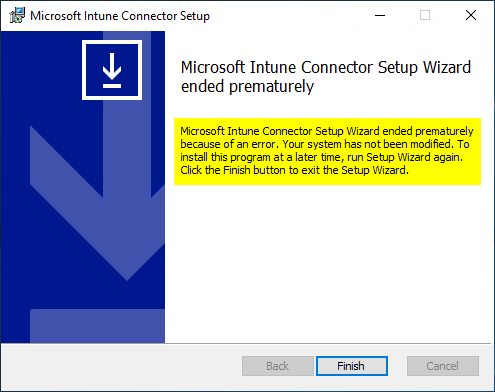
If a certificate based on a Key Storage Provider (KSP) is used, this is manifested by the setup aborting with a meaningless error message.
Microsoft Intune Connector Setup Wizard ended prematurely because of an error. Your system has not been modified. To install this program at a later time, run Setup Wizard again. Click the Finish button to exit the Setup Wizard.
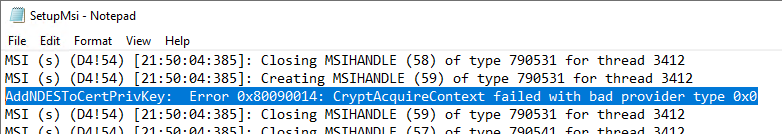
The log file C:\NDESConnectorSetupMSI.log will record that the permissions on the certificate private key cannot be set.
AddNDESToCertPrivKey: Error 0x80090014: CryptAcquireContext failed with bad provider type 0x0
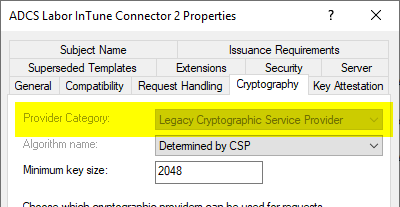
The problem can be solved by using a certificate template with Windows Server 2003 or Windows XP compatibility. This uses a Cryptographic Service Provider (CSP) to generate the key pair.
Use cases that only accept KSP
| Certificate type | Impact |
|---|---|
| Microsoft Online Responder (OCSP) signing certificate | Not configurable. |
Related links:
- The Network Device Enrollment Service (NDES) logs the error message "The Network Device Enrollment Service cannot retrieve one of its required certificates (0x80070057). The parameter is incorrect."
- Basics: Cryptographic Service Provider (CSP) and Key Storage Provider (KSP)
External sources
- SQL Server service can't start after you configure an instance to use a Secure Sockets Layer certificate (Microsoft)
- Outlook Web App and ECP redirect to the FBA page in Exchange Server 2013 (Microsoft)
- The One With The FBA Redirect Loop (Microsoft)
- Securing and Hardening Network Device Enrollment Service for Microsoft Intune and System Center Configuration Manager (Microsoft)
- Installing NDES connector for Intune fails to install NDES certificate (Microsoft)
- certutil 0x80090005 (-2146893819 NTE_BAD_DATA) (ugg.li)
- Active Directory Web Services was unable to process the server certificate. (Microsoft TechNet Forums)
- "Invalid provider type specified" error when accessing X509Certificate2.PrivateKey on CNG certificates (MSDN Blogs, archive link)
9 thoughts on “Liste der Use Cases für Zertifikate, die bestimmte Cryptographic Service Provider (CSP) oder Key Storage Provider (KSP) benötigen”
Comments are closed.