The following is an overview of the audit events generated by the online responder in the Windows Event Viewer.
In contrast to operational events, which are often understood under the term "monitoring", auditing for the certification authority is the configuration of logging of security-relevant events.
The Online Responder (Online Certificate Status Protocol, OCSP) is an alternative way of providing revocation status information for certificates. Entities that want to check the revocation status of a certificate do not have to download the complete list of all revoked certificates thanks to OCSP, but can make a specific request for the certificate in question to the online responder. For a more detailed description, see the article "Basics Online Responder (Online Certificate Status Protocol, OCSP)„.
Event Sources
Audit events are always written to the security log. They always come from the Microsoft Windows Security Auditing source. The events relevant for the certification authority have the ID numbers 5120 to 5127.
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
Activate auditing
Auditing must be activated at various points:
- At responder level
- At operating system level
Enable responder-level auditing
Auditing at the responder level is configured via the management console for the online responder. To do this, right-click in the tree view on the left and select "Responder Properties".
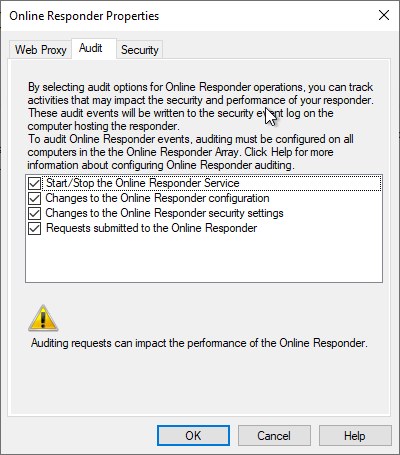
The desired audit events can now be selected in the "Audit" tab.
The audit settings are stored in the registry as a bitmask in the "Audit filter" value under the following registry key:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\OcspSvc\Responder
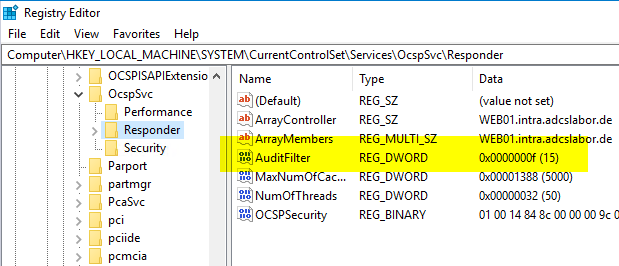
The individual values here mean the following:
| Value | Meaning |
|---|---|
| 1 | Start/Stop the Online Responder Service |
| 2 | Changes to the Online Responder configuration |
| 4 | Requests submitted to the Online Responder |
| 8 | Changes to the Online Responder security settings |
Enable auditing at operating system level
Analogous to the Audit configuration for certification authorities the audit configuration for Certification Services must be enabled at the operating system level. Preferably, this should be done via a group policy that is applied to all online responders.
Events
| ID | Event text |
|---|---|
| 5120 | OCSP Responder Service Started. |
| 5121 | OCSP Responder Service Stopped. |
| 5122 | A Configuration entry changed in the OCSP Responder Service. CA Configuration ID: %1 New Value: %2 |
| 5123 | A configuration entry changed in the OCSP Responder Service. Property Name: %1 New Value: %2 |
| 5124 | A security setting was updated on OCSP Responder Service. New Value: %1 |
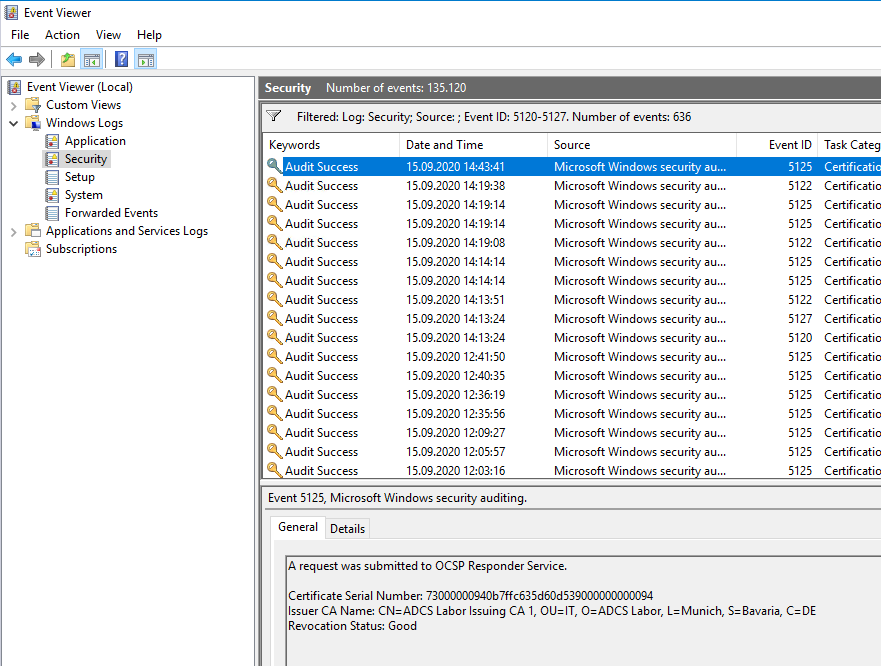
| 5125 | A request was submitted to OCSP Responder Service. |
| 5126 | Signing Certificate was automatically updated by the OCSP Responder Service. CA Configuration ID: %1 New Signing Certificate Hash: %2 |
| 5127 | The OCSP Revocation Provider successfully updated the revocation information. CA Configuration ID: %1 Base CRL Number: %2 Base CRL This Update: %3 Base CRL Hash: %4 Delta CRL Number: %5 Delta CRL Indicator: %6 Delta CRL This Update: %7 Delta CRL Hash: %8 |
| ID | Event text |
|---|---|
| 5058 | Key file operation. Subject: Security ID: %1 Account Name: %2 Account Domain: %3 Logon ID: %4 Cryptographic Parameters: Provider Name: %5 Algorithm Name: %6 Key Name: %7 Key Type: %8 Key File Operation Information: File Path: %9 Operation: %10 Return Code: %11 |
| 5059 | Key migration operation. Subject: Security ID: %1 Account Name: %2 Account Domain: %3 Logon ID: %4 Cryptographic Parameters: Provider Name: %5 Algorithm Name: %6 Key Name: %7 Key Type: %8 Additional Information: Operation: %9 Return Code: %10 |
Related links
- Overview of audit events generated by the Certification Authority
- Configuration of security event monitoring (auditing settings) for certification authorities
4 thoughts on “Übersicht über die vom Onlineresponder (OCSP) generierten Audit-Ereignisse”
Comments are closed.