Name restrictions are a part of the X.509 standard and in the RFC 5280 described. They are a tool that can be used within the qualified subordination can be used to control the validity range of a certification authority certificate in a fine-grained manner.
Continue reading „Grundlagen: Namenseinschränkungen (Name Constraints)“Tag: RFC 5280
Basics: The Key Usage Certificate Extension
Certificate extensions were introduced with version 3 of the X.509 standard. The Key Usage extension is an optional certificate extension that can be used in the RFC 5280 is defined and is used to limit the allowed uses for a key.
Continue reading „Grundlagen: Die Key Usage Zertifikaterweiterung“The "Application Policies" certificate extension
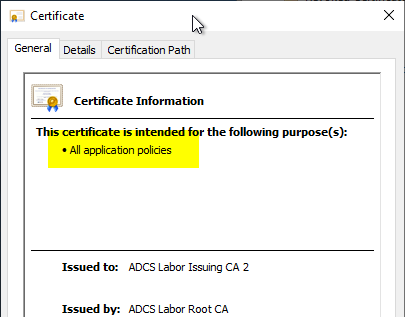
The purposes for which a digital certificate may be used are controlled via the certificate extensions "Key Usage" and "Enhanced Key Usage".
In the "Enhanced Key Usage" certificate extension, the extended key uses for which the certificate may be used.
However, there is another certificate extension called "Application Policies" for certificates issued by a Microsoft Certification Authority, which also contains a list very similar to the Extended Key Usages extension.
Continue reading „Die „Application Policies“ Zertifikaterweiterung“Basics: Configuration file for the certification authority (capolicy.inf)
The capolicy.inf contains basic settings that can or should be specified before installing a certificate authority. In simple terms, it can be said that no certificate authority should be installed without it.
Continue reading „Grundlagen: Konfigurationsdatei für die Zertifizierungsstelle (capolicy.inf)“Basics: Path Length Constraint
The attack on the MD5 signature algorithm demonstrated in late 2008 could only be used to create a usable forged certification authority certificate because the attacked certification authority had not configured any path length restriction.
The limitation of the path length is defined in the RFC 5280 described. The idea behind this is that the maximum depth of the certification authority hierarchy is stored in the "Basic Constraints" extension of a certification authority certificate.
Continue reading „Grundlagen: Einschränkung der Pfadlänge (Path Length Constraint)“Basics: Checking the revocation status of certificates
If a valid, unexpired certificate is to be withdrawn from circulation, it must be revoked. For this purpose, the certification authorities maintain corresponding revocation lists in which the digital fingerprints of the revoked certificates are listed. They must be queried during the validity check.
Continue reading „Grundlagen: Überprüfung des Sperrstatus von Zertifikaten“Use HTTP over Transport Layer Security (HTTPS) for the revocation list distribution points (CDP) and the online responder (OCSP).
With regard to the design of the infrastructure for providing revocation information - i.e. the CRL Distribution Points (CSP) as well as the Online Responders (Online Certificate Status Protocol, OCSP) - the question arises whether these should be "secured" via Secure Sockets Layer (SSL) or Transport Layer Security (TLS).
Continue reading „Verwenden von HTTP über Transport Layer Security (HTTPS) für die Sperrlistenverteilungspunkte (CDP) und den Onlineresponder (OCSP)“More than one common name (CN) in the certificate
Nowadays rather a curiosity than really relevant in practice, but it does happen from time to time that you receive certificate requests that contain more than one common name in the subject. Even though it may seem surprising, this is quite possible and also RFC compliant.
Continue reading „Mehr als ein gemeinsamer Name (Common Name, CN) im Zertifikat“Description of the necessary configuration settings for the "Common PKI" certificate profile
The following is a description of what configuration settings are necessary for a certificate hierarchy based on Active Directory Certificate Services to be compliant with the "Common PKI" standard.
Continue reading „Beschreibung der notwendigen Konfigurationseinstellungen für das „Common PKI“ Zertifikatprofil“Allowed Relative Distinguished Names (RDNs) in the Subject of Issued Certificates
In principle, the RFC 5280 the use of arbitrary strings in the subject string of a certificate. Common fields in the standard are X.520 described. The Length restrictions are also recommended by the ITU-T. The abbreviations commonly used today are mainly taken from the RFC 4519.
However, Microsoft Active Directory Certificate Services only allows certain RDNs by default.
The following Relative Distinguished Names (RDNs) are accepted by the Active Directory Certificate Services (ADCS) certificate authority by default:
Continue reading „Erlaubte Relative Distinguished Names (RDNs) im Subject Distinguished Name (DN) ausgestellter Zertifikate“Include the wildcard issuance policy (All Issuance Policies) in a certification authority certificate
If you install an issuing CA and do not explicitly request an issuance policy, the resulting CA certificate will not contain an issuance policy.
If you want to include the wildcard issuance policy (All Issuance Policies) in the certification authority certificate, you must proceed as follows:
Continue reading „Die Wildcard Ausstellungsrichtlinie (All Issuance Policies) in ein Zertifizierungsstellen-Zertifikat aufnehmen“