As a Certification Authority operator, you are (among other things) responsible for the identification of the enrollees and the confirmation of the requested identities. The fact that this task is carried out conscientiously and without errors is the central cornerstone for the trust that is placed in the Certification Authority. Well-known companies are already failed in this task, even had to file for insolvency as a result of misrepresentations and/or were severely punished by the major players on the market.
In many cases, we as enterprise (Microsoft) PKI operators (regardless of the quality involved) are able to delegate our task of uniquely identifying an enrollee to Active Directory. In many cases, however, we must also instruct our certification authority(ies) to simply issue whatever is requested.
TameMyCerts is a Policy moduleto secure the Microsoft certification authority (Active Directory Certificate Services). It extends the functions of the certification authority and enables the Extended application of regulationsto enable the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem and is available under a free license. It can downloaded via GitHub and can be used free of charge.
Notable examples include:
- Mobile Device Management (MDM) systems such as VMware AirWatch (now known as "Workspace ONE") apply for certificates on behalf of the users of the managed end devices without the certification authority being able to influence the certificate content applied for. "Workspace ONE" has a known and as yet unfixed bug that it requests certificates without identity if a device is not associated with a user.
- Many types of equipment used in the company require the operation of a Simple Certificate Enrollment (SCEP) server, which passes the requested certificate content 1:1 to the certification authority. Poorly secured SCEP interfaces can be a Gateway for attacks on the environment be
- And, of course, the human factor. PKI operators can also during the configuration of the certification authorities or manual checking of certificate requests make mistakes and thus cause certificates to be misissued. The same applies, of course, to other administrators who may have been granted certificate requests (in the worst case, even via the Certification Authority Web Enrollment).
Name restrictions of the certification authority certificate can address these cases partially, but not nearly fully.
Today I would like to present a very powerful alternative to regain control over certificate issuance, in the form of the TameMyCerts Policy Module for the Microsoft Certification Authority.
With this it is possible, among other things, to define the permissible certificate content in a fine-granular way and to have certificate requests that do not comply with the rules rejected directly at the certification authority.
It also allows much more flexible planning of the certification authority hierarchy, since multiple use cases with the same certification authority can be individually restricted. Certificate content can also be enforced.
TameMyCerts was developed in the C# programming language and placed under an open source license. So it can be used free of charge.
If desired, there is the option for a paid maintenance contract, including support hours. Applying for a maintenance contract ensures the long-term development of the module.
Functionality
In contrast to Exit modules, where the certification authority is capable to use more than one, only one policy module can be loaded at the same time. If you decide to use your own policy module, you usually lose the complete functionality of the Windows default policy module. This takes over essential important functions like (among other things)...
- Check whether the enrollee is authorized to apply for the certificate.
- Adding the configured certificate extensions to the issued certificate (from the certificate template configuration, policy module, but also the certificate template information and CDP/AIA distribution points).
- Adding the configured certificate attributes such as Subject and Subject Alternative Name if they are to be formed from Active Directory.
Since policy modules are mapped as Component Object Model (COM) objects, we can simply add it to our policy module. The certificate requests are first passed on to the Windows Default Policy Module and then its response is evaluated.
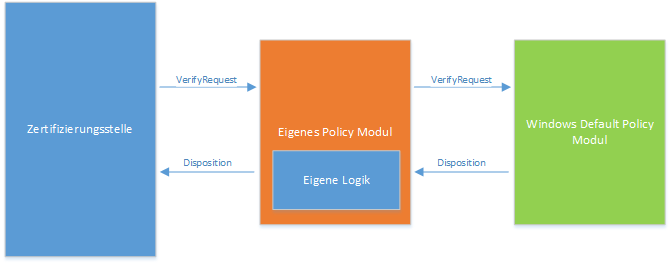
We thus retain the full functionality of the Windows Default Policy Module and can now perform additional checks. The TameMyCerts policy module supports the checking of all conceivable Subject Relative Distinguished Names and the most common Subject Alternative Name types.
Functions of TameMyCerts
TameMyCerts offers the following functions, among others:
- Apply content rules for offline certificate requests. For example, it can be configured that certificates must mandatorily include a DNS name, but under no circumstances a user principal name, and that the requested certificate content must follow certain rules (for example, only certain DNS domains, IP subnets, or hostnames following certain patterns). The possibilities here include:
- Force certain fields to appear in the certificate request, or allow them if they do.
- Force the specified field types to occur only in a specified number.
- Force the contents of defined fields to conform to specified regular expressions or not violate defined regular expressions or IP subnet masks (a fine-grained application of Name restrictions).
- Force certificate requests that have unspecified fields to be rejected.
- Establish a connection to the requested Active Directory object (user or computer) and ensure that it is in a particular security group or that it is not a member of a particular security group. Thus, for example, certificate issuance for administrative accounts can be prevented.
- Entering the Security Identifier Certificate Extension with the data of the determined Active Directory object. Also prevent a Security Identifier certificate extension (with uncertain content) from being specified by the requester.
- Issue certificates with a specific start date. In this way, certificates can be dated into the future so that they are only valid from a certain date. In conjunction with the existing means of the Windows Default Policy module certificates can thus be issued for a precisely defined period.
- "truncating" the end date of issued certificates at a certain point in time. In this way, for example, a fixed end date can be set for certificates that have been weak key variables be determined.
- Ensure that the intended key algorithm is actually being used (this is is not checked by the Windows Default Policy module).
- Ensure that certificates can only be used in certain ways (for example Autoenrollment) can be applied for, and thus also prevent the private key is marked as exportable.
Thus, the TameMyCerts Policy Module can be used to protect inadequately secured interfaces such as the Network Device Enrollment Service or connections to mobile device management systems such as VMware AirWatch can be effectively secured.
Likewise, it is suitable for delegating manual certificate requests, such as for Web server certificates to other teams.
Since TameMyCerts intervenes directly on the certification authority in the certificate issuance process, it is suitable for all interfaces, such as:
- RPC/DCOM
- SCEP with the Network Device Registration Service (NDES)
- Certificate Enrollment Web Services (CEP/CES)
- Certification Authority Web Enrollment (CAWE)
- Own developments such as the AdcsToRest REST API.
Install the policy module
The definition of certificate template rules is controlled by XML files. First, a folder must be created on the certification authority server, which will contain the definition files. Sample files are provided with the installation package.
See also the detailed enclosed documentation (README.adoc).
The module comes with an installation script (install.ps1). It must be executed on the certification authority with administrator rights. Here, the previously created folder is specified with the -PolicyDirectory Directive.
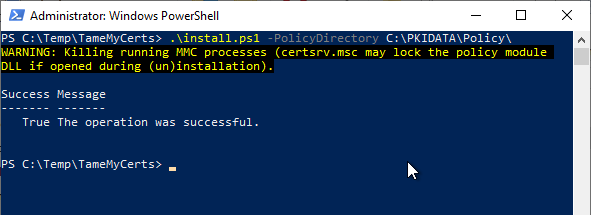
The installation script terminates running Microsoft Management Console (mmc) processes, otherwise the Certificate Authority Management Console (certsrv.msc) may prevent deregistration of the DLL file.
If a SafeNet Key Storage Provider is detected, a waiting time is inserted after the completion of the certification authority service, to work around a known problem with the KSP.
Installation on standalone certification authorities is prevented, as the module currently offers no added value to the Windows Default Policy module in this case.
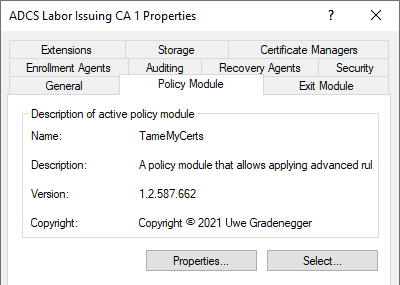
After successful execution of the installation script, the policy module is already set as the active module.
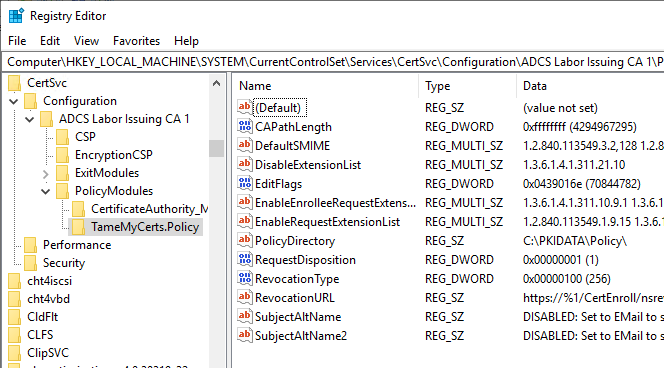
The content of the registry path of the Windows Default Policy module was copied to the one for the TameMyCerts Policy module.
Provided that the Logging level of the certification authority is set to at least 4 (CERTLOG_VERBOSE), the policy module logs that it is ready to process incoming certificate requests when the certification authority service is started.
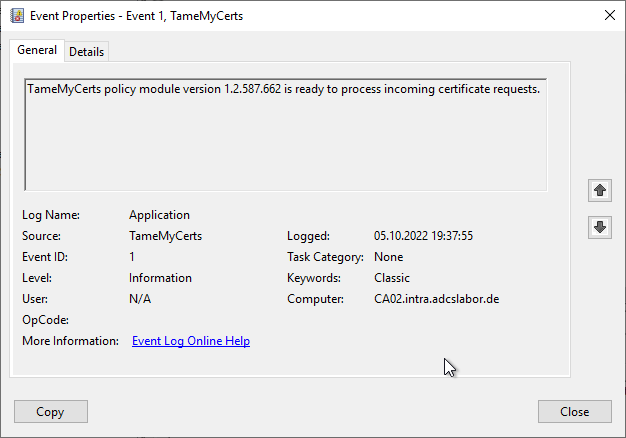
Configure the policy module
The installation package comes with several sample files (Sample_Webserver.xml, Sample_User_AE_TPM.xml). These can be used as a starting point for your own rules. For each certificate template for which the additional rules are to be applied by TameMyCerts, a file of the same name must be created in the folder previously created and specified during installation.
It is not necessary to create a configuration file for all certificate templates, but only for those to which the additional functions provided by TameMyCerts are to be applied. Certificate templates for which no configuration file exists are treated by TameMyCerts as if the Windows Default Policy module were still activated.
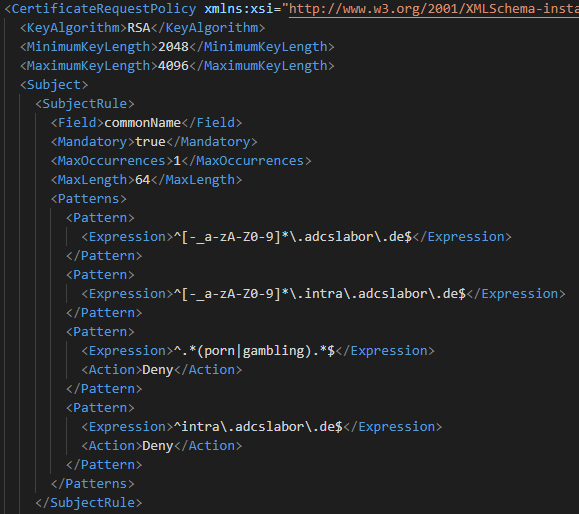
For the description of the individual field types and directives, see the enclosed detailed documentation.
Please note that the TameMyCerts Policy module applies naming rules only to certificate requests that are configured to allow the requester to specify the subject content in the certificate request.
Example:
The Policy Module in Action
The certification authority continues to log as known the Event no. 53 for rejected certificate requests.
In addition, when a certificate request is rejected, the TameMyCerts Policy Module logs the reason for the rejection.
Examples
Active Directory Certificate Services denied request 524437 because The public key does not meet the minimum size required by the specified certificate template. 0x80094811 (-2146875375 CERTSRV_E_KEY_LENGTH). The request was for CN=intranet.adcslabor.de. Additional information: Denied by Policy Module
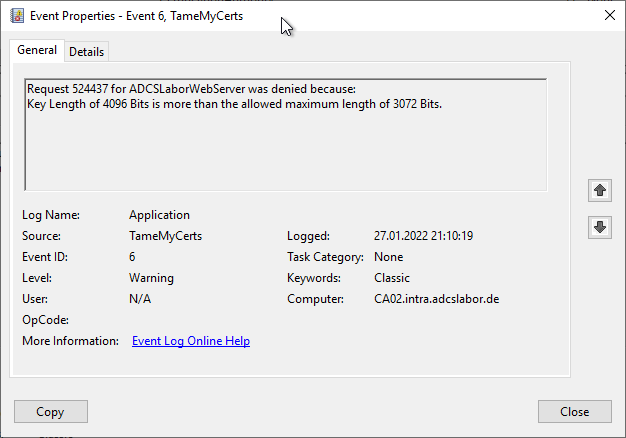
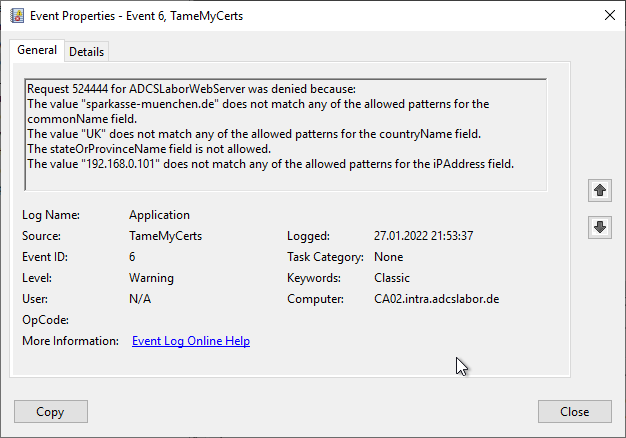
Active Directory Certificate Services denied request 524444 because The certificate has an invalid name. The name is not included in the permitted list or is explicitly excluded. 0x800b0114 (-2146762476 CERT_E_INVALID_NAME). The request was for CN=sparkasse-muenchen.de, C=UK, S=Bavaria. Additional information: Denied by Policy Module
Related links:
- Basics: Name constraints for certification authority certificates
- Changes to Certificate Issuance and Certificate-Based Logon to Active Directory with the May 10, 2022 Patch for Windows Server (KB5014754)
- Issue certificates with shortened validity period
- What key lengths should be used for certificate authorities and certificates?
- How secure is the "Allow private key to be exported" setting in the certificate templates?
- The key algorithm of certificate requests is not checked by the certification authority's policy module
- Basics of manual and automatic Certificate Enrollment via Lightweight Directory Access Protocol (LDAP) and Remote Procedure Call / Distributed Common Object Model (RPC/DCOM)
- Network Device Enrollment Service (NDES) Basics
External sources
- The "Tame My Certs" policy module for Active Directory Certificate Services (GitHub / Uwe Gradenegger)
18 thoughts on “Ein Policy Modul, um sie zu bändigen: Vorstellung des TameMyCerts Policy Moduls für Microsoft Active Directory Certificate Services”
Comments are closed.