The following describes the process that runs in the background when certificates are requested manually or automatically in order to achieve the highest possible level of automation.
Regardless of whether a manual application is made via the certificate management consoles (certmgr.msc for user and certlm.msc for computer certificates), the process is identical.
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
Step 1: Query the directory service via LDAP
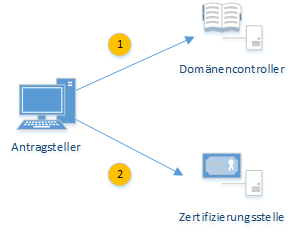
In the first step, the client establishes an LDAP connection to a domain controller and queries the following information:
- All pKICertificateTemplate Objects (certificate templates) in the Active Directory forest.
- All pKIEnrollmentService objects (enterprise certificate authorities) in the Active Directory forest.
- All msPKI-Enterprise-Oid Objects (Object Identifier) in the Active Directory forest.
This information is all stored in the Configuration partition of the Active Directory forest.
The pKICertificateTemplate and msPKI-Enterprise-OID objects can be used to determine whether the requester is authorized to request ("enroll") and whether an automatic request is to be made ("auto-enroll"). The default settings for making the certificate request are also determined here.
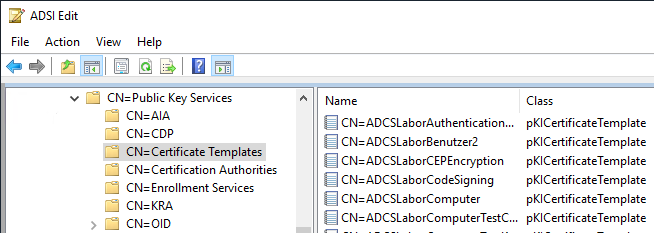
The connection between already existing certificates and the certificate templates is established via the "Certificate Template Information" extension. This contains the object identifier of the certificate template as well as version information. This prevents certificates from being requested twice during autoenrollment, and certificates can be requested again if a serious change has occurred. Replaced certificates can be identified and archived using this information.
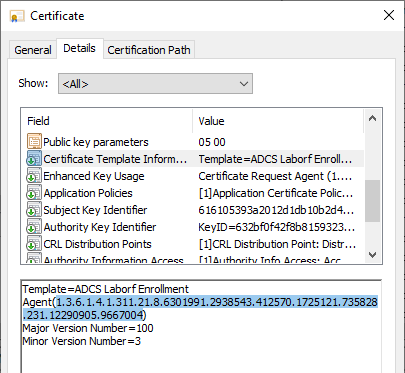
For this reason, the "Certificate Template Information" extension must not be used for certificates for which autoenrollment is to be used. be removedotherwise the process will no longer work and the Side effects could occur.
The pKIEnrollmentService objects can be used to determine the certification authorities that offer the certificate templates to be requested, as well as on which computer in the network the certification authority is running. For this purpose the attributes certificateTemplates as well as dNSHostName evaluated.
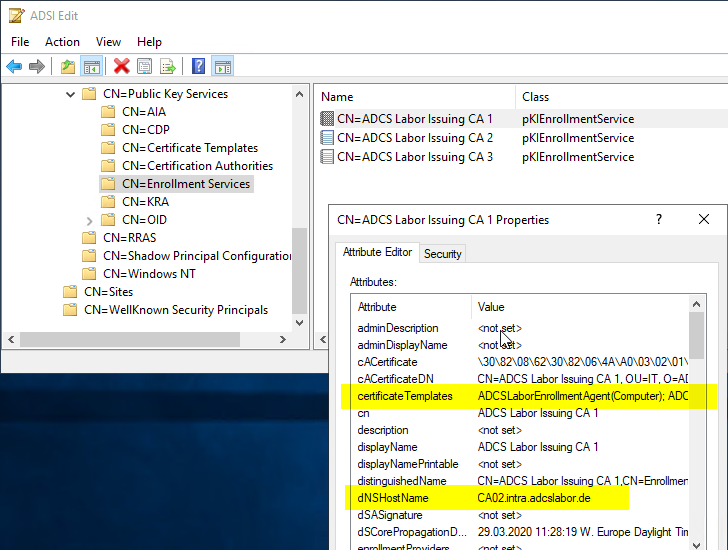
Step 2: Connection to the target certification authority via RPC/DCOM (MS-WCCE)
In the second step, a key pair and a certificate request are generated based on the requested information and sent to the responsible certification authority. Here the Windows Client Certificate Enrollment Protocol (MS-WCCE) used.
If several certification authorities offer the same certificate template, the decision is made at random if no site awareness has been configured.
The certificate authority can identify the user based on Kerberos authentication and applies the settings specified in the corresponding certificate template with its policy module.
Control of client behavior for autoenrollment
The control of client behavior is controlled by group policy. The group policies exist once for user and for computer settings.
They can be found in our "User" or "Computer Configuration" - "Windows Settings" - "Public Key Policies" - "Certificate Services Client - Autoenrollment".
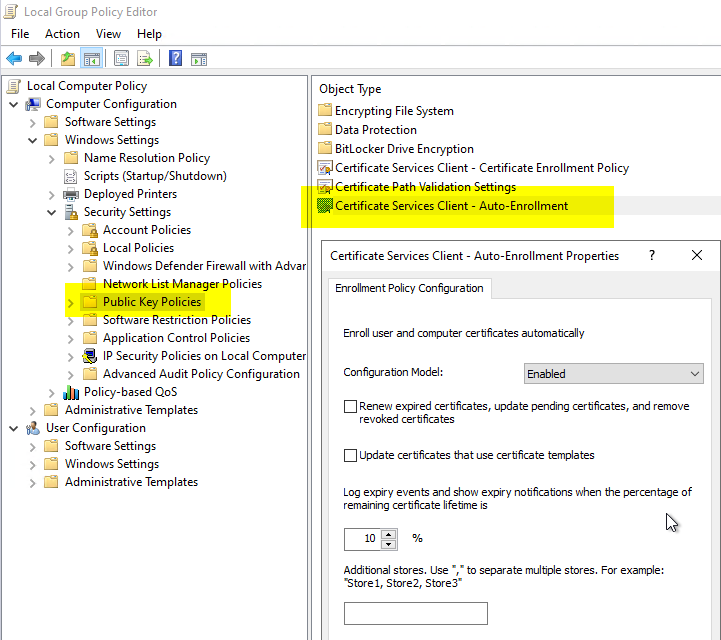
- The "Configuration Model" causes the autoenrollment process to run at all. If this setting is not configured by a group policy, it is by default on a domain member activates.
- The setting "Renew expired certificates, update pending certificates, and remove revoked certificates" causes expired certificates to be renewed automatically if they were issued by an Active Directory integrated certificate authority. In addition, approved certificate requests are fetched from certification authorities if they are available. Revoked certificates are archived. If this setting is not configured by a group policy, it is by default on a domain member deactivated.
- The "Update certificates that use certificate templates" setting causes certificates to be automatically requested that are enabled for autoenrollment for the requestor. If this setting is not configured by a group policy, it is by default set on a domain member. deactivated.
So, by default, the autoenrollment process automatically replicates all domain members to the Active Directory forest's Public Key Services object when triggered.
Determination of the current configuration
The settings can be checked via the registry on Windows computers. They can be found in the "AEPolicy" value under the following paths:
| Path | Description |
|---|---|
| HKCU\Software\Policies\Microsoft\Cryptography\AutoEnrollment | User settings, configured by group policy |
| HKCU\Software\Microsoft\Cryptography\AutoEnrollment | User settings, locally configured |
| HKLM\Software\Policies\Microsoft\Cryptography\AutoEnrollment | Computer settings, configured by group policy |
| HKLM\Software\Microsoft\Cryptography\AutoEnrollment | Computer settings, locally configured |
Settings configured via group policy take precedence over locally configured settings.
A query can be made via the command line.
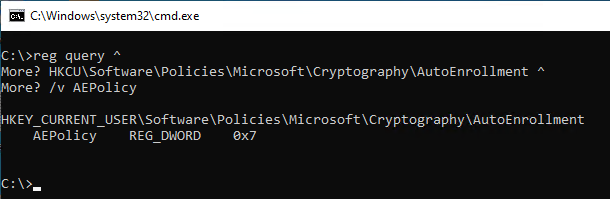
Example: Settings set by group policy for the currently logged in user account.
reg query ^ HKCU\Software\Policies\Microsoft\Cryptography\AutoEnrollment ^ /v AEPolicy
Example: Computer account settings set by group policy.
reg query ^ HKLM\Software\Policies\Microsoft\Cryptography\AutoEnrollment ^ /v AEPolicy
The values mean in detail:
| Value | Description | Result |
|---|---|---|
| 0x00000000 or not available | AutoEnrollment process is activates „Update certificates that use certificates templates" is deactivated | none automatic request for certificates none Automatic renewal of expired certificates none Automatic collection of approved certificate requests none Automatic archiving of revoked certificates |
| 0x00000001 | AutoEnrollment process is activates „Update certificates that use certificates templates" is activates „Renew expired certificates, update pending certificates, and remove revoked certificates" is deactivated | automatic request for certificates none Automatic renewal of expired certificates none Automatic collection of approved certificate requests none Automatic archiving of revoked certificates |
| 0x00000006 | AutoEnrollment process is activates „Update certificates that use certificates templates" is deactivated „Renew expired certificates, update pending certificates, and remove revoked certificates" is activates | none automatic request for certificates Automatic renewal of expired certificates Automatic collection of approved certificate requests Automatic archiving of revoked certificates |
| 0x00000007 | AutoEnrollment process is activates „Update certificates that use certificates templates" is activates „Renew expired certificates, update pending certificates, and remove revoked certificates" is activates | automatic request for certificates Automatic renewal of expired certificates Automatic collection of approved certificate requests Automatic archiving of revoked certificates |
| 0x00008000 | AutoEnrollment is deactivated | none automatic request for certificates none Automatic renewal of expired certificates none Automatic collection of approved certificate requests none Automatic archiving of revoked certificates |
Trigger for triggering the autoenrollment process
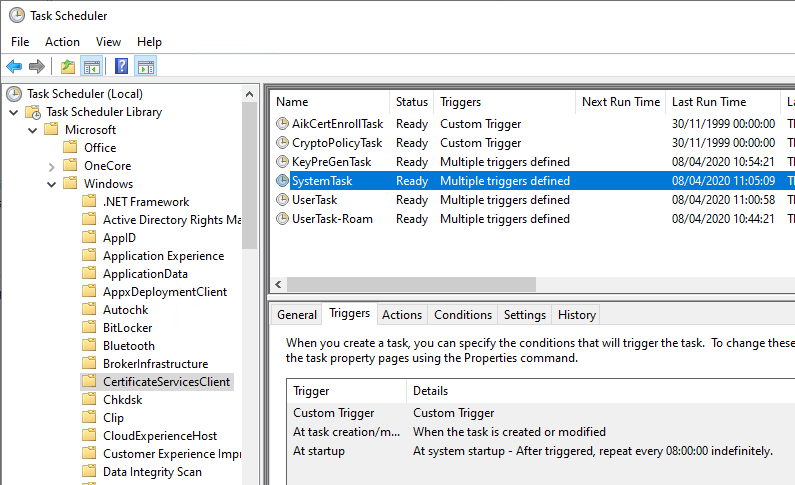
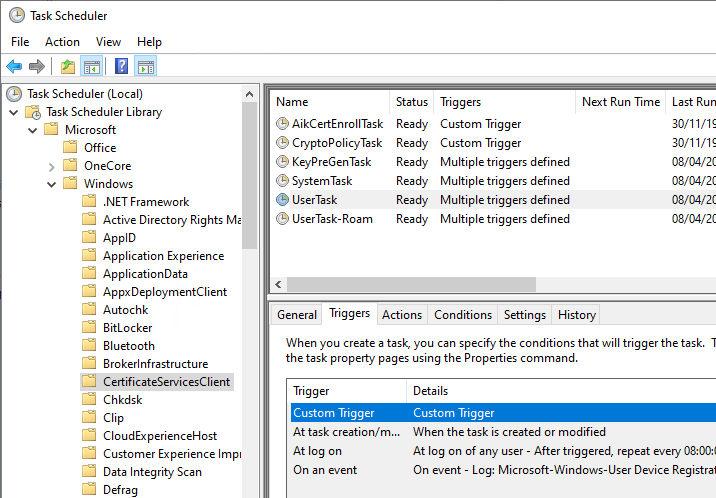
The triggers for running the autoenrollment process on domain members are:
- When the user logs in (for computers, when the computer account logs in, i.e. at system startup).
- By timer every 8 hours.
- When updating group policies, assuming there has been a change.
These settings can be viewed via the task scheduler under "Microsoft" - "Windows" - "CertificateServicesClient".
Manually running the autoenrollment process
If you do not want to wait for the autoenrollment to be triggered automatically, you can also start it manually. The different ways to run the autoenrollment process are described in the article "Manually running the autoenrollment process" described.
Related links:
External sources
- [MS-WCCE]: Windows Client Certificate Enrollment Protocol (Microsoft)
- Configure certificate auto-enrollment (Microsoft)
- Certificate Enrollment Web Services (Microsoft, archive.org)
44 thoughts on “Grundlagen manuelle und automatische Zertifikatbeantragung über Lightweight Directory Access Protocol (LDAP) und Remote Procedure Call / Distributed Common Object Model (RPC/DCOM) mit dem MS-WCCE Protokoll”
Comments are closed.