Assume the following scenario:
- An attempt is made to request a certificate from a certificate authority (Enterprise CA) integrated into Active Directory for a user or computer.
- The certificate request fails with the following error message:
The requested certificate template is not supported by this CA. 0x80094800 (-2146875392 CERTSRV_E_UNSUPPORTED_CERT_TYPE).
Two states must be distinguished here:
- The certificate request arrives at the certification authority and is rejected there
- The certificate request does not arrive at the certification authority
The certificate request arrives at the certification authority and is rejected there
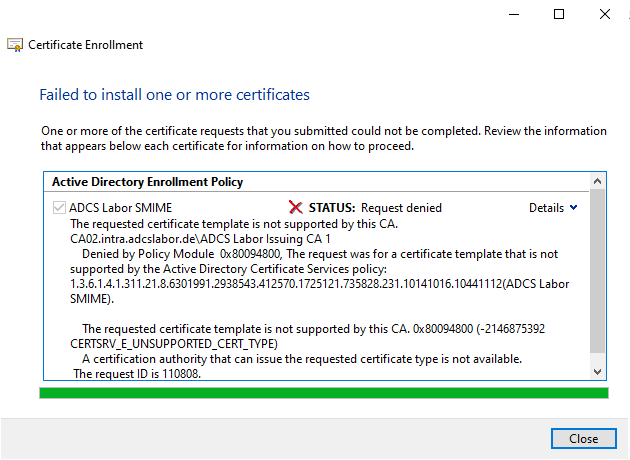
On the computer the Event no. 13 logged with the same error code.
The Certification Authority will use the Event no. 53 log with the same error code.
Cause
When requesting a certificate via MMC, the user has no selection option for the certification authority to be used after selecting the certificate template. The information that the certification authority offers the certificate template is obtained from the pKIEnrollmentService object in the Active Directory.
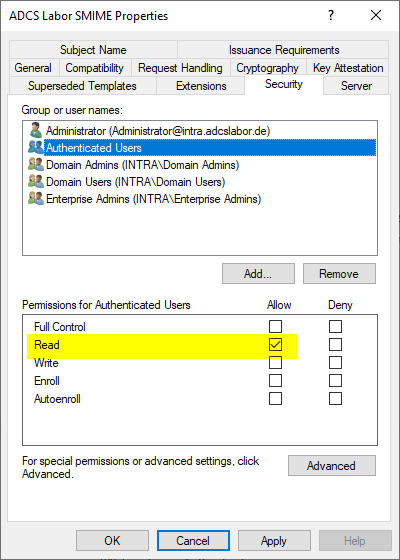
If the certification authority now claims not to know the certificate template, this is usually because it lacks the read permissions on the certificate template.
By default, the certificate authority obtains the read permission through the entry for "Authenticated Users" in the security settings of the certificate template.
The certificate request does not arrive at the certification authority
Although the error code CERTSRV_E_UNSUPPORTED_CERT_TYPE suggests this, there is also the case that the certificate request is not even sent by the requesting client.
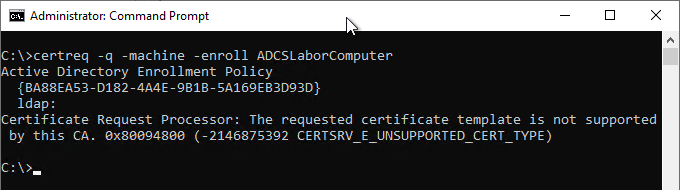
An exemplary Certificate Enrollment would look something like this (see also article "Troubleshooting for automatic certificate request (autoenrollment) via RPC/DCOM„):
certreq -q -machine -enroll ADCSLaborComputer
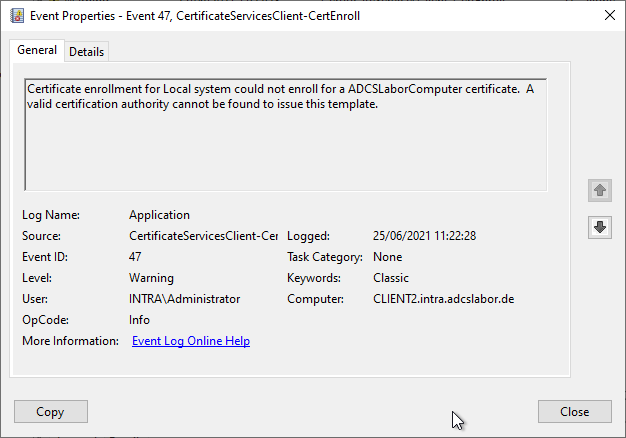
If you increase the logging level on the requesting client, you will see, among other things, the Event no. 47 locate.
Certificate enrollment for Local system could not enroll for an ADCSLaborComputer certificate. A valid certification authority cannot be found to issue this template.
Such behavior may have the following causes:
- A certificate template has been specified that has not been published on any certification authority (also check for typos here).
- The requesting client does not trust the certificate authority providing the certificate template.
Details: The requesting client does not trust the certificate authority providing the certificate template.
In this case also the Event no. 52 logged.
The CA certificate for ADCS Labor Issuing CA 1 is not trusted. Certificate enrollment for Local system for an ADCSLaborComputer certificate failed.
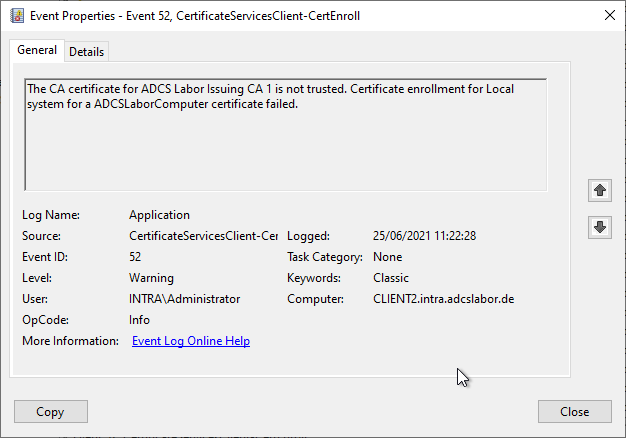
This can happen,
- if the root certificate of the hierarchy is not registered in the local certificate store for trusted root certificate authorities,
- but also when the root certificate is trusted but the certificate chain cannot be completed, e.g., because the Authority Information Access (AIA) distribution point cannot be accessed due to a missing firewall rule (for port 80/TCP). Occurs especially with certificate authority hierarchies with three or more levels.
Related links:
External sources:
- The Requested Template is not Supported by this CA (Error 0x80094800) (PKI Solutions, Inc.)
6 thoughts on “Die Beantragung eines Zertifikats schlägt fehl mit Fehlermeldung „The requested certificate template is not supported by this CA. 0x80094800 (-2146875392 CERTSRV_E_UNSUPPORTED_CERT_TYPE).“”
Comments are closed.