Assume the following scenario:
- An online responder (OCSP) is set up in the network.
- The certification authorities report at irregular intervals that certificate requests for the OCSP password signing certificates fail with the following error message:
The revocation function was unable to check revocation for the certificate. 0x80092012 (-2146885614 CRYPT_E_NO_REVOCATION_CHECK).
The Online Responder (Online Certificate Status Protocol, OCSP) is an alternative way of providing revocation status information for certificates. Entities that want to check the revocation status of a certificate do not have to download the complete list of all revoked certificates thanks to OCSP, but can make a specific request for the certificate in question to the online responder. For a more detailed description, see the article "Basics Online Responder (Online Certificate Status Protocol, OCSP)„.
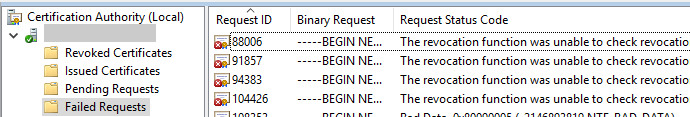
For this purpose, the Certification Authorities shall test the Event with ID 22 of the source Microsoft-Windows-CertificationAuthority with identical error message.
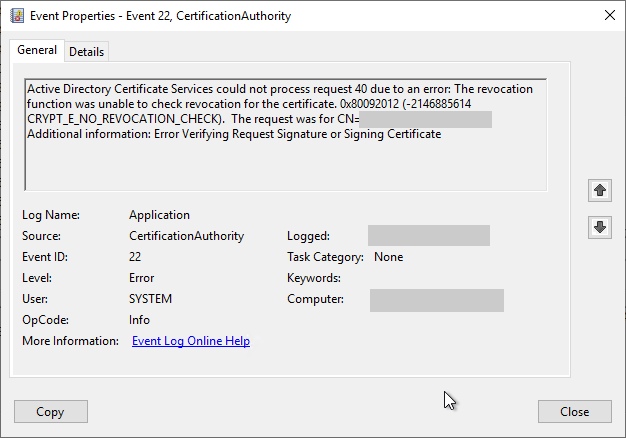
Active Directory Certificate Services could not process request 40 due to an error: The revocation function was unable to check revocation for the certificate. 0x80092012 (-2146885614 CRYPT_E_NO_REVOCATION_CHECK). The request was for CN=web01.intra.adcslabor.de. Additional information: Error Verifying Request Signature or Signing Certificate
Cause
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
To get to the bottom of the cause, inspect we will delete the failed certificate request.
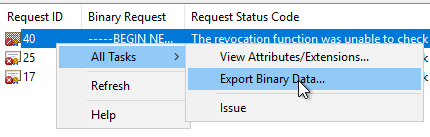
The first thing to notice is that this is a PKCS#7 certificate request, and that it was made by the taskhostw.exe process (the task scheduler). This is usually a sign that the autoenrollment process made the certificate request. Actually, the online responder (ocspsvc.exe) should make the certificate request in PKCS#10 format.
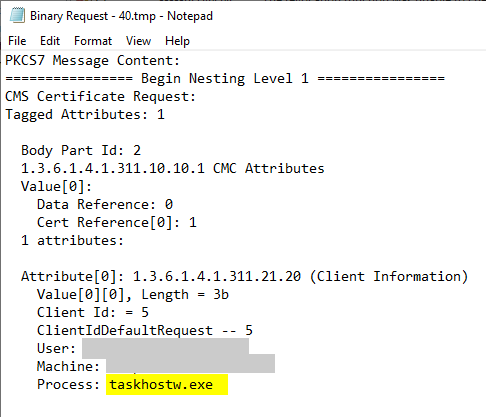
Further inspection of the certificate request reveals that it was signed (therefore PKCS#7) with the previous OCSP password signing certificate.
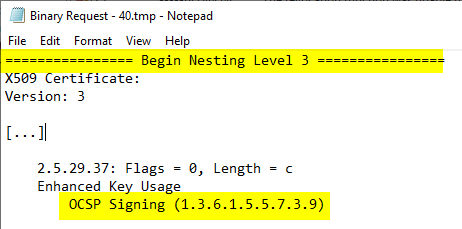
This is the reason for the error message that the revocation status cannot be verified. OCSP password signing certificates have according to RFC 6960 does not have any blocking information.
The error is therefore due to the fact that the autoenrollment permission was assigned on the certificate template for the OCSP response signature.
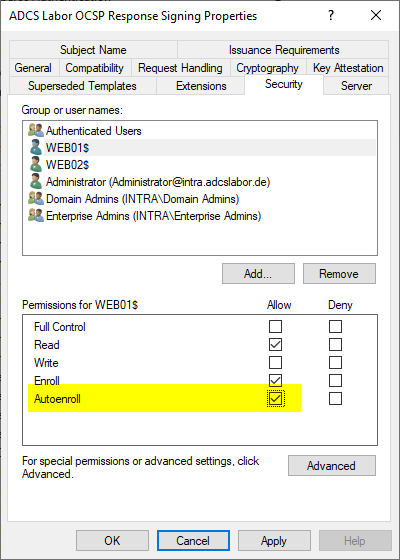
The autoenrollment process thus sometimes starts before the online responder process and tries to renew the certificate. If the online responder process successfully renews the certificate afterwards, the autoenrollment process has nothing to do, which explains the only sporadic occurrence.
Solution
The solution is very simple: The autoenrollment permission must be removed on the certificate template for the OCSP password signing certificates.
OCSP answer signing certificates do not require autoenrollment authorization because the online responder process takes care of certificate request and renewal. This is particularly necessary because certificate requests made by the online responder process include the Authority Key Identifier extension to determine the certificate authority certificate to be used for signing the certificate (see article "Allow requesting a specific signature key on a certification authority". and for this Event with ID 128 of the source Microsoft-Windows-CertificationAuthority).
Related links:
- Basics of online responders (Online Certificate Status Protocol, OCSP)
- Basics of manual and automatic Certificate Enrollment via Lightweight Directory Access Protocol (LDAP) and Remote Procedure Call / Distributed Common Object Model (RPC/DCOM)
One thought on “Zertifikatanforderungen für den Onlineresponder (OCSP) schlagen sporadisch fehl mit Fehlermeldung „The revocation function was unable to check revocation for the certificate. 0x80092012 (-2146885614 CRYPT_E_NO_REVOCATION_CHECK)“”
Comments are closed.