Assume the following scenario:
- A certificate template is configured to elliptic curves based keys to be used.
- In addition, the certificate template is configured to use the Microsoft Platform Crypto Provider to use the private key with the Trusted Platform Module (TPM) of the device.
- The certificate request fails with the following error message:
Error: The requested operation is not supported. 0x80090029 (-2146893783 NTE_NOT_SUPPORTED)
On Windows Server 2016, the error message "No provider was specified for the store or object. 0x80092006 (-2146885626 CRYPT_E_NO_PROVIDER)" is issued with otherwise identical behavior.
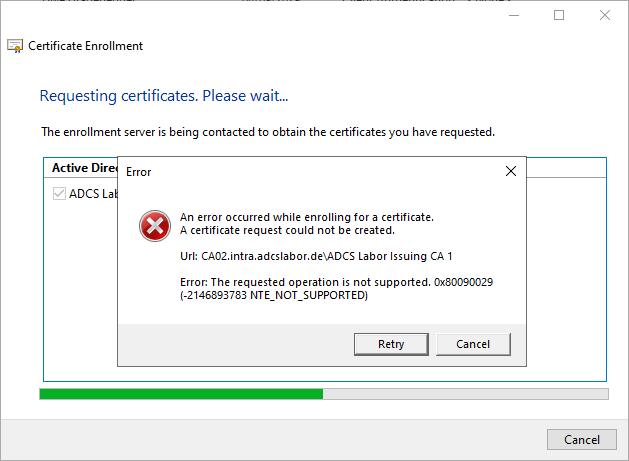
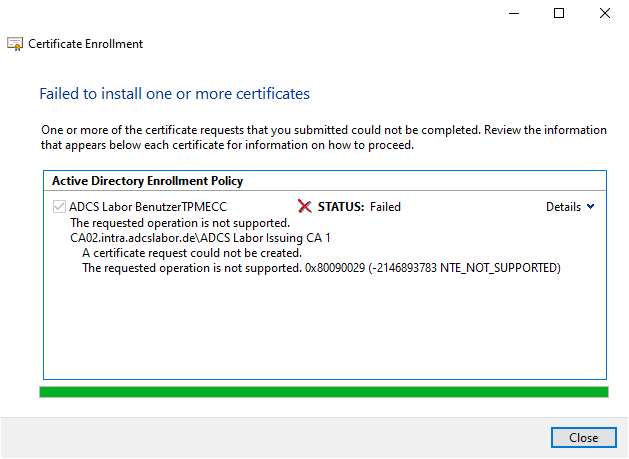
Will Autoenrollment is used, no events are logged. When applying for a certificate manually, the client logs the events with the numbers 82 and then with number 13 the source Microsoft-Windows-CertificateServicesClient-CertEnroll.
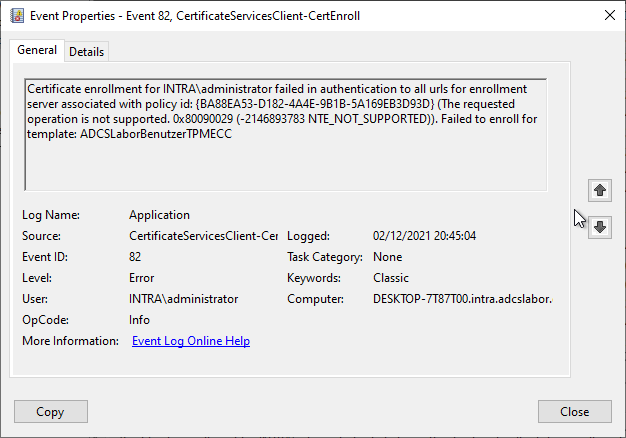
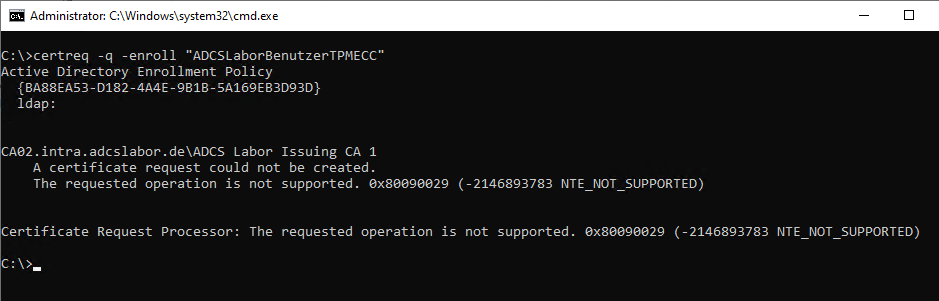
Certificate enrollment for INTRA\administrator failed in authentication to all urls for enrollment server associated with policy id: {BA88EA53-D182-4A4E-9B1B-5A169EB3D93D} (The requested operation is not supported. 0x80090029 (-2146893783 NTE_NOT_SUPPORTED)). Failed to enroll for template: ADCSLaborBenutzerTPMECC
Certificate enrollment for INTRA\administrator failed to enroll for an ADCSLaborBenutzerTPMECC certificate with request ID N/A from CA02.intra.adcslabor.de\ADCS Labor Issuing CA 1 (The requested operation is not supported. 0x80090029 (-2146893783 NTE_NOT_SUPPORTED)).
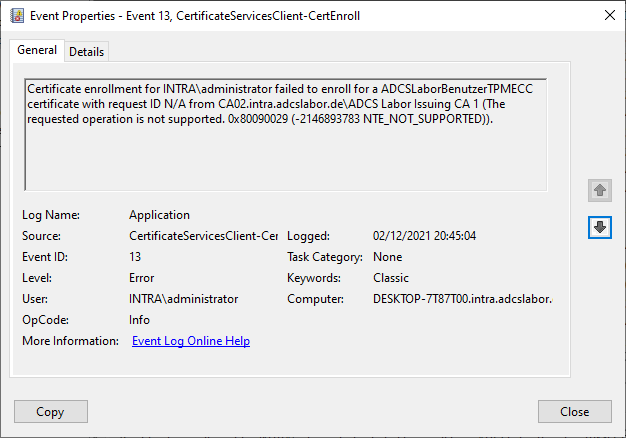
The manual request via the command line tells us that no certificate request can be made. To put it more precisely, apparently the key pair cannot be created.
A certificate request could not be created. The requested operation is not supported. 0x80090029 (-2146893783 NTE_NOT_SUPPORTED)
Cause
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
This is apparently a bug in the Microsoft Platform Crypto Provider, which is responsible for generating the keys with TPM protection. As it turns out, the Certificate Enrollment works perfectly with Windows 10 21H2 and Windows 11.
I have tested the following Windows versions:
| Windows version | State |
|---|---|
| Windows 10 Enterprise 1909 | works not |
| Windows 10 Pro 21H1 | works not |
| Windows 10 Pro 21H2 | works |
| Windows 11 Pro (Release) | works |
| Windows Server 2016 (patch status September 2022) | works not |
| Windows Server 2019 (Release) | works not |
| Windows Server 2019 (patch status August 2021) | works |
| Windows Server 2022 | works |
In a Changelog for an Insider Preview version for Windows 10 21H2 there is a halfway matching entry, but it is of dubious significance (it talks about "the" ECDSA certificate, the error message does not match our observations, and it erroneously talks about the Microsoft Software Key Storage Provider).
We fixed an issue that causes the enrollment of the Elliptic Curve Digital Signature Algorithm (ECDSA) certificate to fail with the error, "0x80090027 NTE_INVALID_PARAMETER". This issue occurs when the Trusted Platform Module (TPM) provider (the Microsoft Software Key Storage Provider) stores the key.
Announcing Windows 10 Insider Preview Build 19044.1147 (21H2) (Microsoft)
It seems a bit as if the author himself did not quite understand what the problem is about. That's why I assume that the mentioned fix (also) addresses the problem described here, even if the description doesn't fit exactly.
So the solution is to use Windows 10 21H2 or Windows 11 for corresponding systems.
Notes on the configuration of the certificate template
When configuring the certificate template, you will probably find that you cannot set the combination of elliptic curves and the Microsoft Platform Crypto Provider at all.
This is due to the fact that this combination can only be set if a correspondingly functioning TPM is also installed on the computer on which the certificate template management console is run.
So if on a TPM 2.0 capable computer the Remote Server Administration Tools (RSAT) are installed, the Platform Crypto Provider can be selected in conjunction with ECC keys. Another option is, configure the certificate template directly via LDAP.
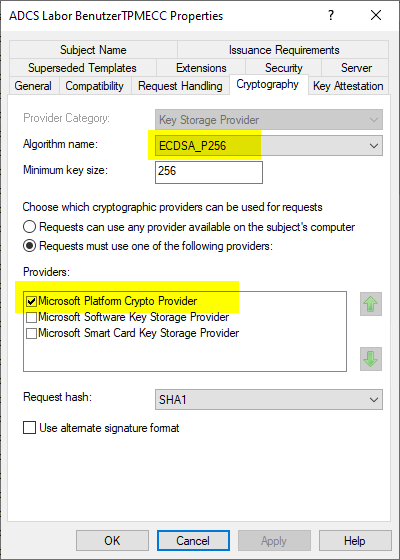
Please also note that only Trusted Platform Module version 2.0 enables the use of elliptic curve based keys at all.
The TPM 2.0 standard however, only prescribes 256-bit key sizes as mandatory.
The TPM should support ECC key sizes of at least 256 bits. Support for other key sizes is allowed.
TPM 2.0 Library specification (Trusted Computing Group)
Other key sizes can (depending on the implementation by the TPM manufacturer), but do not have to work. If you try to use a key size that is not supported by the TPM, the creation of the certificate request also fails here with the same error code "NTE_NOT_SUPPORTED".
This means that without an exact inventory of all devices and their TPM chips, only this key figure remains as the lowest common denominator. Current (2021) However, it offers more than adequate security.
Related links
- Configure a certificate template to use the Microsoft Platform Crypto Provider to enable private key protection through a Trusted Platform Module (TPM).
- Basics: Cryptographic Service Provider (CSP) and Key Storage Provider (KSP)
- Basics: key algorithms, signature algorithms and signature hash algorithms
- Basics: Elliptic curves with regard to their use in the public key infrastructure
- Installing Remote Server Administration Tools for Active Directory Certificate Services on Windows 10 version 1809 and later
External sources
- Announcing Windows 10 Insider Preview Build 19044.1147 (21H2) (Microsoft)
- TPM 2.0 Library specification (Trusted Computing Group)
3 thoughts on “Die Beantragung von Zertifikaten mit auf elliptischen Kurven basierenden Schlüsseln schlägt fehl, wenn der Microsoft Platform Crypto Provider verwendet wird”
Comments are closed.