Assume the following scenario:
- A certificate is requested for a user or a computer from a certificate authority via the certificate management console (certlm.msc or certmgr.msc).
- Autoenrollment does not request a certificate from the desired certificate template, although it is enabled and the permissions are set accordingly.
- The desired certificate template is not displayed when applying manually via the Microsoft Management Console (MMC). If the "Show all templates" check box is selected, the following error message is displayed for the desired certificate template:
Cannot find object or property. Can not find a valid CSP in the local machine.
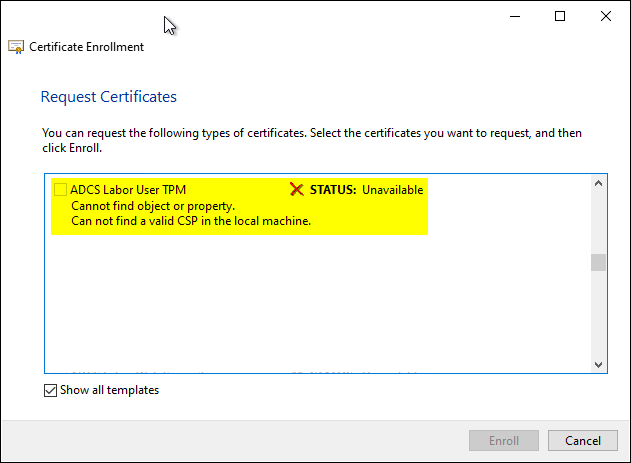
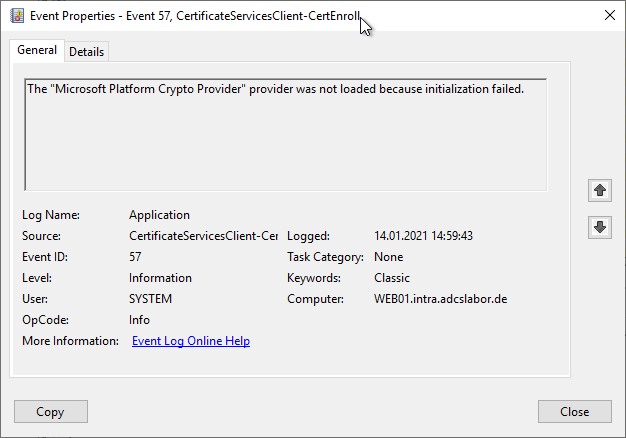
Provided logging is enabled the client runs the Event with ID 57 of source Microsoft-Windows-CertificateServicesClient-CertEnroll logged.
The "Microsoft Platform Crypto Provider" provider was not loaded because initialization failed.
Cause
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
The message occurs because the certificate template is configured to use a Cryptographic Service Provider (CSP) or Key Storage Provider (KSP) that does not exist on the local system. For example, this could be a key storage provider for a Hardware Security Module (HSM) or a Trusted Platform Module (TPM) be
For example, if the certificate template is configured to use the "Microsoft Platform Crypto Provider", a Trusted Platform Module (TPM) is required to generate a key pair for the subsequent certificate request. Therefore, if the machine does not have a working TPM, it is not possible to request a certificate from this template.
Workaround
The workaround is not compatible with the TPM Key Attestation. If TPM Key Attestation is enabled, certificate requests on systems that do not have TPM will fail with error code ERROR_BAD_ARGUMENTS.
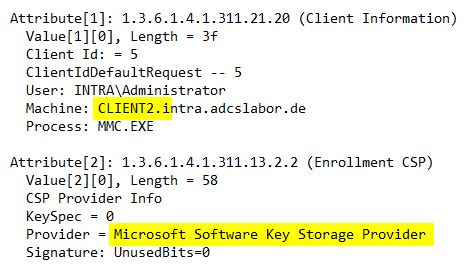
If it is acceptable that non-compatible clients do not protect the key material in hardware, and that they should also receive a certificate from this template, the problem can be circumvented by still entering a generally valid key storage provider such as the Microsoft Software Key Storage Provider as a fallback option.
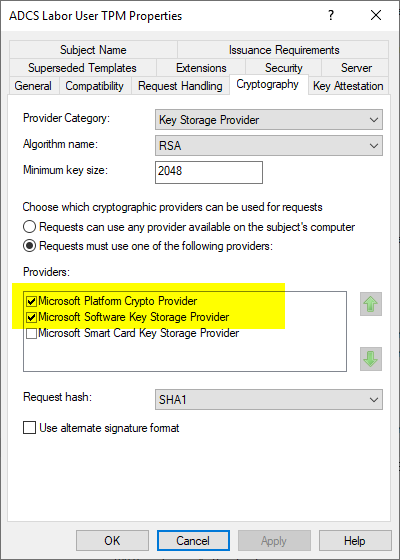
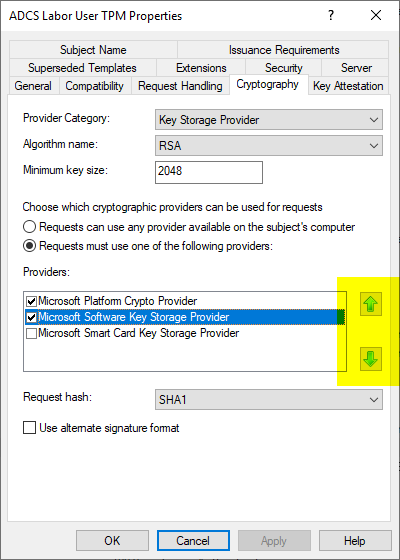
The workaround only works reliably if the preferred key storage provider is in first place. The order can be specified via the configuration dialog of the certificate template.
Inspecting the certificate requirements, you will notice that a client that has a working Trusted Platform module will also use it to create the key pair.
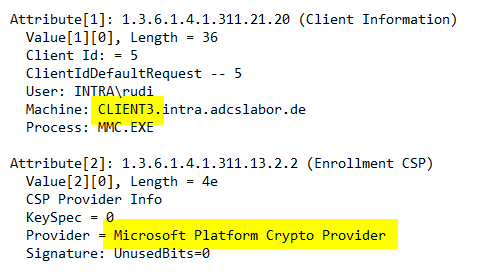
For comparison, a client without a Trusted Platform module. It finds that the Microsoft Platform Crypto Provider cannot be used and falls back to the next entry.
Related links:
- Configure a certificate template to use the Microsoft Platform Crypto Provider to enable private key protection through a Trusted Platform Module (TPM).
- Requesting a Trusted Platform Module (TPM) protected certificate fails with error message "The requested operation is not supported. 0x80090029 (-2146893783 NTE_NOT_SUPPORTED)"
- Troubleshooting for automatic certificate request (autoenrollment) via RPC/DCOM
5 thoughts on “Die Beantragung eines Zertifikats ist nicht möglich, da die Zertifikatvorlage nicht angezeigt wird. Die Fehlermeldung lautet „Can not find a valid CSP in the local machine.“”
Comments are closed.