If autoenrollment is used, participants apply for and renew certificates independently.
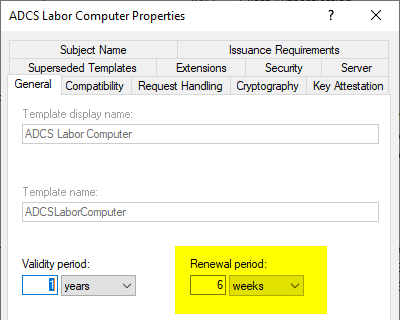
Regarding the validity of the certificates and the period for their automatic renewal, there are two values that can be configured in the General tab of a certificate template:
- Validity period: Describes the overall validity of the issued certificate.
- Renewal period: Describes from which time window, viewed backwards from the expiration date of the certificate, automatic renewal is attempted for the first time (e.g. 6 weeks before expiration).
The validity period value configured in the certificate template can be overridden by other factors. For more information, see the article "Configure the maximum validity period for certificates issued by a certification authority„.
The "Renewal period" only affects certificate templates that are requested or renewed using autoenrollment. Certificate templates whose certificate requests are made manually, as is the case with web servers, for example, cannot use this value. Therefore, it is not relevant for such certificate templates.
In the case of client certificates, for example, the central question that should first be asked regarding certificate validity is: what period of time can I guarantee users by not having any contact with the certification authority? This period determines how early (in terms of the upcoming expiration of the certificate) renewal must begin. Client computers are not always permanently connected to the network - users go on vacation, perhaps often work without VPN, or the device is on standby as spare hardware.
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
The official documentation concerning the renewal period states the following:
The minimum renewal period is 80 percent of the certificate lifetime or six weeks, whichever is greater.
This means that 80% of the certificate's validity must always have elapsed before a renewal of the certificate is attempted.
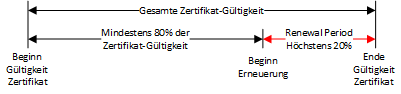
The renewal period must therefore correspond at least to the period that can be guaranteed for offline use. Since this value is at most 20% of the total validity of the certificate, it also determines the minimum value for the total validity of a certificate.
For example, if you want to guarantee three months for renewal, the certificate must have a total validity of 15 months.
However, please note that the renewal period should not be less than 8 hours even for short-lived certificates. This is because the trigger for a reapplication is only triggered every eight hours in the worst case. See article "Basics of manual and automatic Certificate Enrollment via Lightweight Directory Access Protocol (LDAP) and Remote Procedure Call / Distributed Common Object Model (RPC/DCOM)„.
A long certificate validity also means that revoked certificates must be kept longer on the revocation list, which increases its size accordingly and may therefore mean higher network load and load times for resources protected with certificates. The premise should always be: As short as possible, as long as necessary.
Related links:
- Clients connected via Virtual Private Network (VPN) do not renew certificates automatically
- Configure the maximum validity period for certificates issued by a certification authority
- Basics of manual and automatic Certificate Enrollment via Lightweight Directory Access Protocol (LDAP) and Remote Procedure Call / Distributed Common Object Model (RPC/DCOM)
External sources
- Administering Certificate Templates (Microsoft)
5 thoughts on “Planung von Zertifikat-Gültigkeit und Erneuerungs-Zeitraum von End-Entitäts-Zertifikaten mit Autoenrollment”
Comments are closed.