The Network Device Enrollment Service (NDES) uses two certificate templates for its internal function to make it act as a Registration Authority (RA). These are published during role configuration of the NDES service on the configured certificate authority and certificates are requested:
- CEP Encryption
- Exchange Enrollment Agent (Offline Request)
These certificate templates are standard templates from the Windows 2000 world (version 1 templates), i.e. they cannot be edited. In addition, the Exchange Enrollment Agent (Offline Request) template is marked as a user template, i.e. during NDES role configuration the certificate is requested in the context of the installing user and then imported into the machine store. At the latest when the certificates are to be renewed after two years, things get complicated here.
It is therefore a good idea to use your own certificate templates for NDES. These can be adapted in terms of their key length, for example. The use of hardware security modules (HSM) is also possible in this way. Even automatic renewal can be configured.
The Network Device Enrollment Service (NDES) provides a way for devices that do not have an identifier in Active Directory (for example, network devices such as routers, switches, printers, thin clients, or smartphones and tablets) to request certificates from a certification authority. For a more detailed description, see the article "Network Device Enrollment Service (NDES) Basics„.
NDES also uses a certificate template for the connecting devices. The setup is described in the article "Configure Device Template for Network Device Enrollment Service (NDES)". In addition, the service is optionally offered via HTTPS. The setup is described in the article "Enabling Secure Sockets Layer (SSL) for the Network Device Enrollment Service (NDES)." described.
Configure your own certificate template for CEP Encryption
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem and is available under a free license. It can downloaded via GitHub and can be used free of charge.
The CEP Encryption Template is used to encrypt the certificate request during transfer to the certificate authority. The SCEP protocol was originally designed to be used without HTTPS (HTTP over Secure Socket Layer, SSL), so the encryption here is at the protocol level.
The core properties of the template that the NDES process will look for at startup are:
- Key Usage: Key Encipherment (0x20)
- Extended Key Usage: Certificate Request Agent (1.3.6.1.4.1.311.20.2.1)
The default template "CEP Encryption" ("CEP-Verschlüsselung" in German) is used as the initial template and a copy is created.
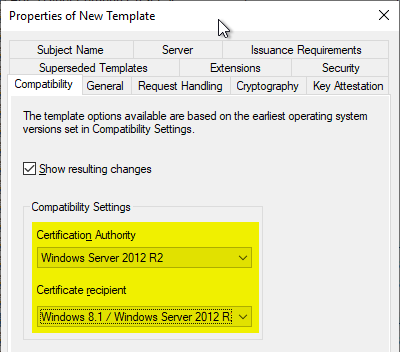
If a domain account is used for the NDES service, the permissions on the private keys can be configured directly in the certificate template. For this purpose, the compatibility of the template on Windows Server 2012 R2 must be configured in the "Compatibility" tab.
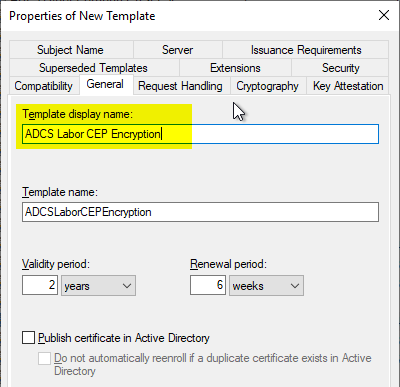
A meaningful name is assigned in the "General" tab.
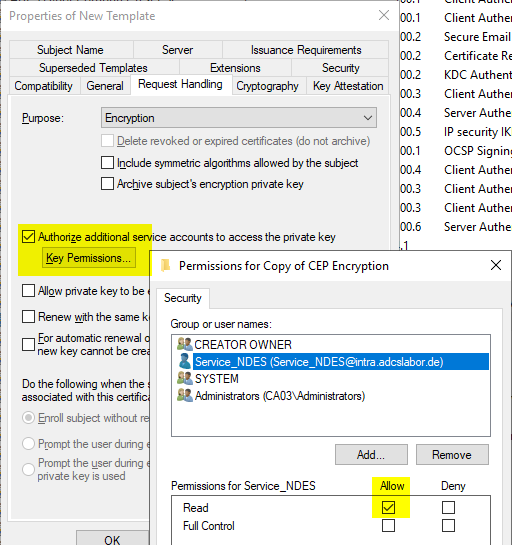
If the permissions on the private key can and should be set via the template, these can be assigned in the "Request Handling" tab.
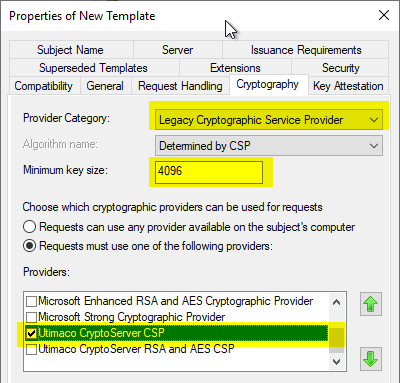
In the "Cryptography" tab, a higher key length and optionally a Hardware Security Module (HSM) Cryptographic Service Provider (CSP) can be configured.
Only the "old" Cryptographic Service Provider (CSP) supported. Key Storage Providers, as available since Windows Server 2008, are not supported by NDES.
The CSP for an HSM must have been previously installed and set up on the NDES system so that it can be used. The system on which the certificate template is configured must also have the CSP installed so that it can be selected when configuring the certificate template.
The CSP for the HSM is only displayed if it is also installed on the system on which the certificate template is configured.
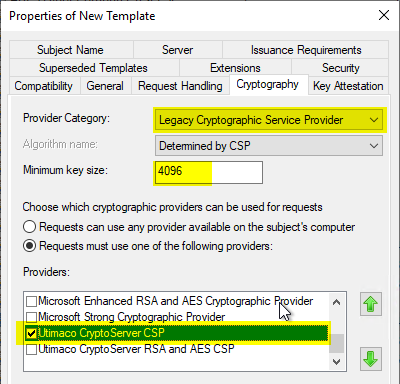
In the NDES installation routine, the Microsoft RSA SChannel Cryptographic Provider is preselected.
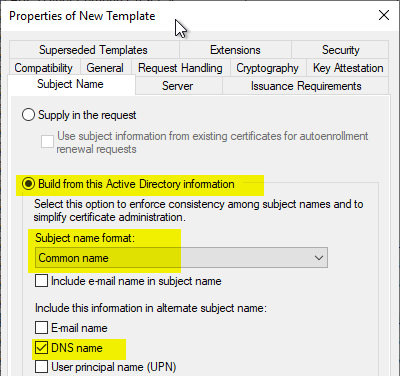
In the "Subject Name" tab, the identity can be created from the Active Directory. It is recommended to fill both Subject (Common Name) and Subject Alternative Name (DNS name).
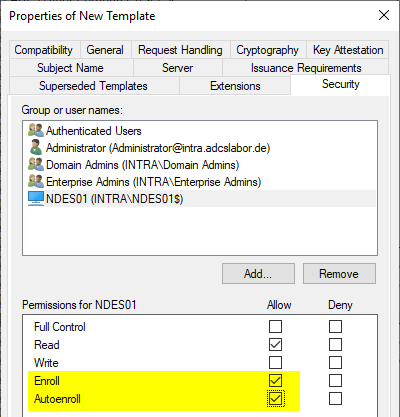
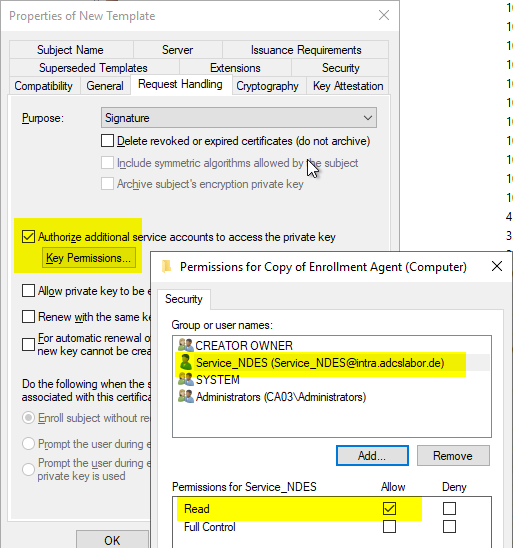
In the "Security" tab, the computer account of the NDES server gets rights to request.
Automatic application (auto-enrollment) is also possible, but this is not recommended, as rework is required (setting key permissions and restarting the NDES service, if necessary).
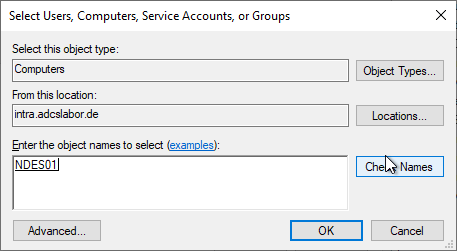
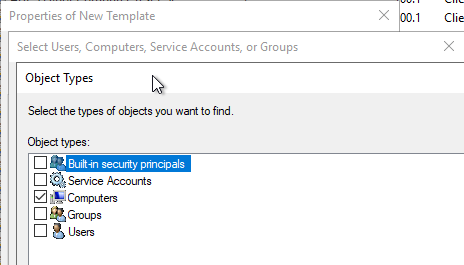
In order for computer accounts to be included in the search, the corresponding object type must be selected in the search dialog.
Configure your own certificate template for Exchange Enrollment Agent (Offline Request)
The Exchange Enrollment Agent template is used to sign the certificate request before it is submitted to the certificate authority to ensure that it actually originates from the NDES service, which is acting as the enrollment agent here.
The core properties of the template that the NDES process will look for at startup are:
- Key Usage: Digital Signature (0x80)
- Extended Key Usage: Certificate Request Agent (1.3.6.1.4.1.311.20.2.1)
By default, the certificate request signature is not verified by the certificate authority, but this is quite useful and should be configured. How this is done is described in the article "Configure Device Template for Network Device Enrollment Service (NDES)" described.
As a starting template not the default Exchange Enrollment Agent (Offline Request) template is used because it is a user template, but the customized template is to be configured for a computer. Instead, the otherwise identical Enrollment Agent (Computer) template is used and a copy is created.
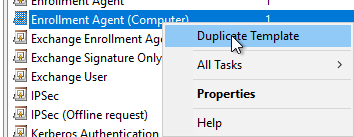
If a domain account is used for the NDES service, the permissions on the private keys can be configured directly in the certificate template. For this purpose, the compatibility of the template on Windows Server 2012 R2 must be configured in the "Compatibility" tab.
A meaningful name is assigned in the "General" tab.
If the permissions on the private key can and should be set via the template, these can be assigned in the "Request Handling" tab.
In the "Cryptography" tab, a higher key length and optionally a Hardeware Security Module (HSM) Cryptographic Service Provider (CSP) can be configured.
Only the "old" Cryptographic Service Providers (CSP) are supported. Key Storage Providers as they are available since Windows Server 2008, are not supported by NDES.
The CSP for an HSM must have been previously installed and set up on the NDES system so that it can be used. The system on which the certificate template is configured must also have the CSP installed so that it can be selected when configuring the certificate template.
The CSP for the HSM is only displayed if it is also installed on the system on which the certificate template is configured.
The Microsoft Enhanced Cryptographic Provider v1.0 is preselected in the NDES installation routine.
In the "Subject Name" tab, the identity can be created from the Active Directory. It is recommended to fill both Subject (Common Name) and Subject Alternative Name (DNS name).

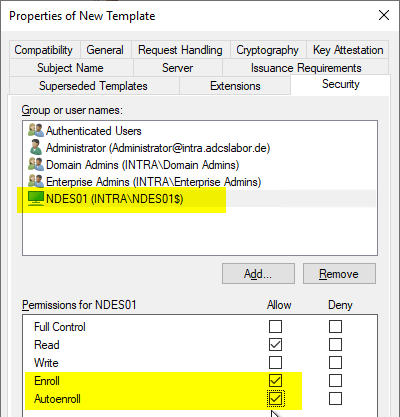
In the "Security" tab, the computer account of the NDES server is given rights to apply. Automatic application (autoenrollment) is also possible.
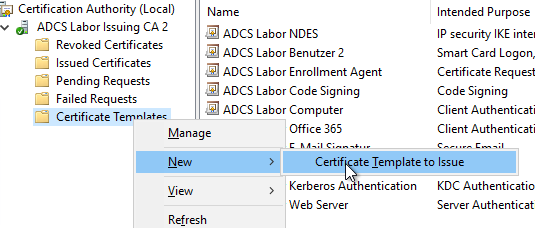
Publish the certificate templates
The two templates can now be published on the Certification Authority.
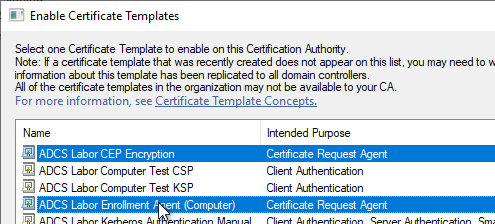
Applying for the Registration Authority certificates
Afterwards, the certificates can be requested from the certificate management console of the computer account (certlm.msc) of the NDES server.
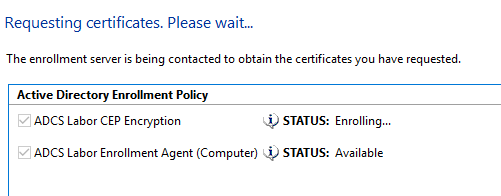
If multiple certification authorities offer the certificate templates described here, a certification authority will be randomly selected during the request process, which may result in certificates being issued by the wrong certification authority. NDES will refuse service in this case. Therefore, the certificate templates described here should only ever be temporarily published on the certification authority for whose NDES server new certificates are currently to be requested.
Set permissions on private keys
If the permissions on the private keys have not been configured in the certificate templates in the "Request Handling" tab, or NDES is running with the identity of the IIS application tool, the permissions on the private keys of both certificates must be set manually. This is done through the computer certificate management console (certlm.msc).
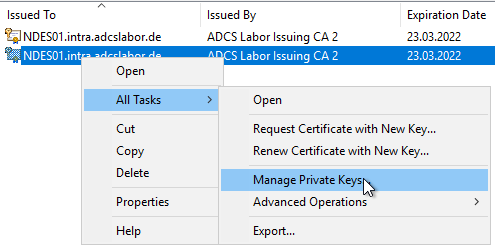
The NDES service account requires read permissions to the private keys of both certificates.
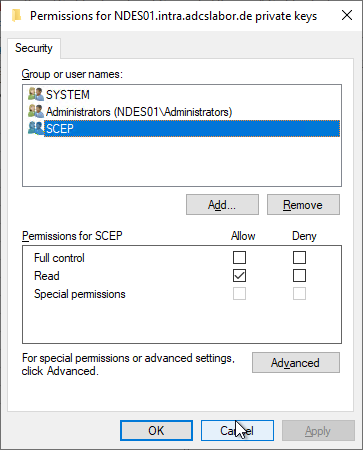
Unfortunately, you cannot configure the SCEP IIS application pool identity from the Certificate Management Console. However, one can find here a PowerShell script with which this can be done.
Related links:
- Configure Device Template for Network Device Enrollment Service (NDES)
- Enabling Secure Sockets Layer (SSL) for the Network Device Enrollment Service (NDES).
- The Network Device Enrollment Service (NDES) logs the error message "The Network Device Enrollment Service cannot retrieve one of its required certificates (0x80070057). The parameter is incorrect."
13 thoughts on “Eigene Registration Authority (RA) Zertifikatvorlagen für den Registrierungsdienst für Netzwerkgeräte (NDES) verwenden”
Comments are closed.