The Network Device Enrollment Service (NDES) is Microsoft's implementation of the Simple Certificate Enrollment Protocol (SCEP) developed by Cisco in the early 2000s. The first implementation was released with Windows Server 2003.
It may come as a surprise that NDES does not use Secure Socket Layer (SSL) for the HTTP connections in the default setting to this day. This fact is explained and evaluated in more detail below.
The Network Device Enrollment Service (NDES) provides a way for devices that do not have an identifier in Active Directory (for example, network devices such as routers, switches, printers, thin clients, or smartphones and tablets) to request certificates from a certification authority. For a more detailed description, see the article "Network Device Enrollment Service (NDES) Basics„.
There are two crucial addresses at NDES:
- The request web page (certsrv/mscep) where SCEP clients submit their certificate requests and obtain issued certificates.
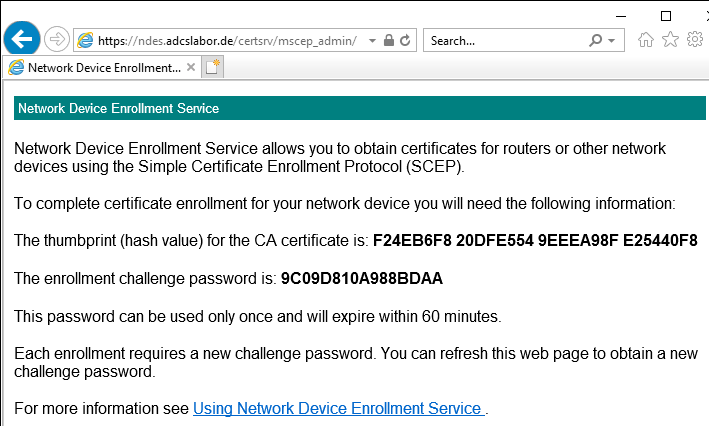
- The administration web page (certsrv/mscep_admin, under which device administrators can request one-time passwords and distribute them to the requesting network devices.
Consideration for NDES application website
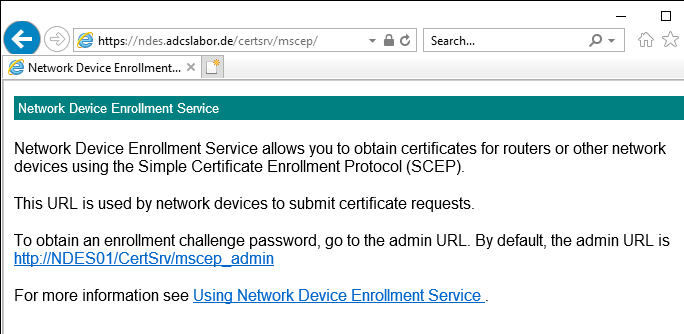
For evaluation see in the standard for the SCEP protocol:
The information portion of a SCEP message is carried inside an enveloped-data content type [...] The PKCS#7 [RFC2315] content-encryption key [...] is encrypted using the public key of the recipient of the message, i.e. the RA or the CA public key [...].
This means that the confidential information with the Registration Authority (RA) Certificate of the NDES server (CEP Encryption).
The one-time password is a plain text attribute within the certificate request, but this is not problematic for the reason mentioned before, as this information is not transmitted unencrypted.
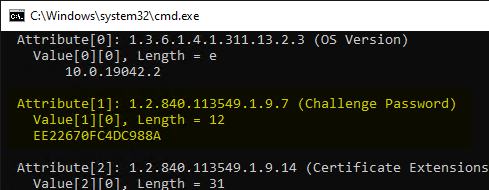
Consideration for the NDES administration website
Even though it is visually identical to the application web page, the NDES administration web page belongs to not to the official SCEP standard. It is specific to the Microsoft implementation of the SCEP protocol, known as the Network Device Enrollment Service (NDES).
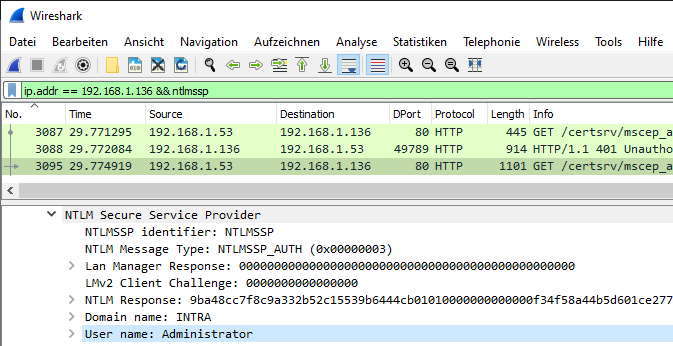
If you take a look at the data traffic transmitted during logon, you will see that logically the user's logon information can be found there again if no Secure Sockets Layer is used to protect the transmission. These can easily read out and used for identity theft.
SSL should therefore definitely be used here.
Conclusion
It is not a security risk to perform the certificate request via SCEP over HTTP without Secure Sockets Layer, because the transmitted information is sufficiently protected by the SCEP protocol.
The situation is different with the NDES administration web page: here, SSL should definitely be enabled and its use enforced to prevent disclosure of the administrators' credentials.
For the setup see article "Enabling Secure Sockets Layer (SSL) for the Network Device Enrollment Service (NDES).„.
Related links:
- Network Device Enrollment Service (NDES) Basics
- Certificate Enrollment for Windows Systems via the Network Device Enrollment Service (NDES) with Windows PowerShell
External sources
- draft-nourse-scep-23 - Simple Certificate Enrollment Protocol (Internet Engineering Task Force)
- A 9-step recipe to crack a NTLMv2 hash from a freshly acquired .pcap (801Labs)
- Why don't we need to do SCEP with SSL? (Christian T. Drieling - Apanthos.com, archive link)
4 thoughts on “Sollte HTTPS für den Registrierungsdienst für Netzwerkgeräte (NDES) verwendet werden?”
Comments are closed.