By default, the Network Device Enrollment Service (NDES) requests certificates from the "IPsec (Offline Request)" template. This certificate template is from Windows 2000 times and cannot be edited. Therefore, it is recommended to change the default settings and use your own certificate templates that serve your personal requirements.
The Network Device Enrollment Service (NDES) provides a way for devices that do not have an identifier in Active Directory (for example, network devices such as routers, switches, printers, thin clients, or smartphones and tablets) to request certificates from a certification authority. For a more detailed description, see the article "Network Device Enrollment Service (NDES) Basics„.
Configure the certificate template
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem and is available under a free license. It can downloaded via GitHub and can be used free of charge.
The SCEP protocol supports three certificate types:
- EncryptionTemplate: A certificate that can only be used to encrypt data but not to sign it. The Key Usage extension of this certificate includes Key Encipherment (0x20).
- SignatureTemplate: A certificate that can only be used for signing, but not for encrypting data. The key usage extension of this certificate includes Digital Signature (0x80).
- GeneralPurposeTemplate: A certificate that can be used for both signing and encrypting data. The Key Usage extension of this certificate includes Key Encipherment and Digital Signature (0xA0).
Typically, however, all three settings are set to the identical value, so NDES can effectively serve only one certificate template.
You are completely free with regard to the content of the certificate template. For example, the "Enhanced Key Usage" extension depends on the desired use case. Often, for example, "Secure E-Mail" or "Client Authentication" is used here.
Microsoft uses the term "Enhanced Key Usage", the correct name according to RFC 5280 is "Extended Key Usage"..
In the "Subject Name" tab, it must be configured that the requester provides the identity with the certificate request. This is mandatory for NDES, but of course also means a certain security risk, since the authority to determine the identities is thus relinquished to the requesting users.
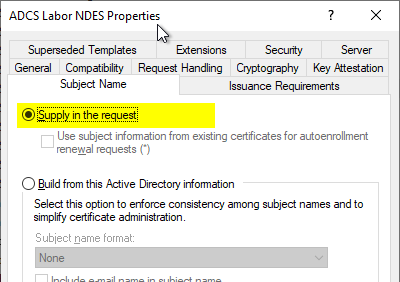
It is recommended to configure in the Issuance Requirements tab that certificate requests require an authorized signature with the "Certificate Request Agent" application policy. Certificate requests are signed by NDES with the Enrollment Agent certificate, so another security barrier can be created in this way: it is no longer possible to bypass the NDES server for certificate requests.
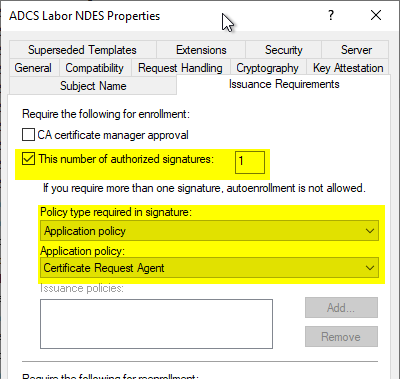
In the Security tab, make sure that the following entities are given the enroll right:
- The identity of the SCEP application pool on the NDES server. This can be either a service account or the computer account of the NDES server, depending on the configuration. The certificates are requested using this account.
- Any account that should be able to request one-time passwords (OTPs) from the NDES server and will access the mscep_admin application. NDES checks the authorization on the certificate template to determine the authorization to issue the OTPs.
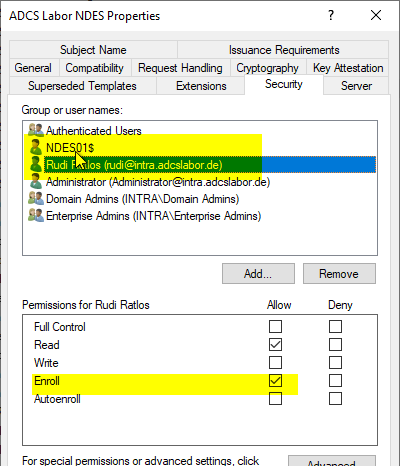
Configuring the NDES server to use the certificate template
The configuration of the corresponding certificate templates can be found in the registry on the NDES server under:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\MSCEP
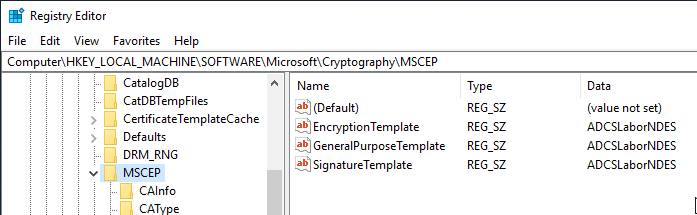
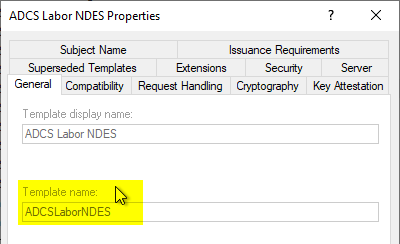
Note that the name of the LDAP object of the certificate template is entered, i.e. the name without the spaces.
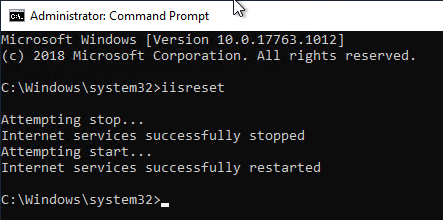
The configuration is applied to the NDES server using the iisreset command.
iisreset
Related links:
- Enabling Secure Sockets Layer (SSL) for the Network Device Enrollment Service (NDES).
- Using custom Registration Authority (RA) certificate templates for the Network Device Enrollment Service (NDES).
External sources
- Certreq.exe syntax (Microsoft)
- Simple Certificate Enrollment Protocol (SCEP) does not strongly authenticate certificate requests (Carnegie Mellon University)
13 thoughts on “Gerätevorlage für den Registrierungsdienst für Netzwerkgeräte (NDES) konfigurieren”
Comments are closed.