In the default configuration, the online responder returns the status "Good" for requested certificates that do not appear on one of the configured revocation lists.
This can be problematic because the online responder has no knowledge of certificates issued by the certification authorities. If an attacker succeeds in issuing a certificate using the private key of the certification authority without their knowledge, this would not be detected by the online responder, and would also be reported in the Audit log show up as "Good".
The Online Responder (Online Certificate Status Protocol, OCSP) is an alternative way of providing revocation status information for certificates. Entities that want to check the revocation status of a certificate do not have to download the complete list of all revoked certificates thanks to OCSP, but can make a specific request for the certificate in question to the online responder. For a more detailed description, see the article "Basics Online Responder (Online Certificate Status Protocol, OCSP)„.
See also RFC 6960:
The "good" state indicates a positive response to the status inquiry. At a minimum, this positive response indicates that no certificate with the requested certificate serial number currently within its validity interval is revoked. This state does not necessarily mean that the certificate was ever issued or that the time at which the response was produced is within the certificate's validity interval.
Functionality
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
The following steps are performed below:
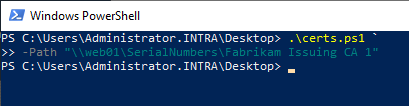
- Export serial numbers of certificates issued by certification authorities.
- Configure the online responder to use the exported serial numbers to check the certificate status.
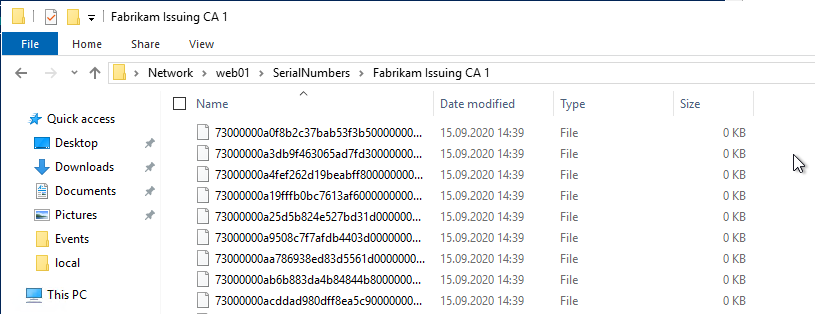
The serial numbers of the certificates issued by the certification authorities concerned are exported as empty text files. The file name here corresponds to the serial number of the certificate.
These files must be made available to the online responder. After it has been configured to search for the serial numbers in the configured directory, it will check for each requested certificate whether a file corresponding to the serial number can be found.
After the configuration is done, the online responder will behave as follows:
- For certificates whose serial numbers are found in one of the configured directories, the status "Good" is returned.
- For certificates whose serial numbers appear in one of the configured revocation lists, the status "Revoked" is returned.
- For certificates for which the previous two criteria do not apply, the status "Unknown" is returned.
Solution reliability
The use of the online responder by all participants is not guaranteed. For example, in the following cases, the online responder may not be used:
- The application under test does not use OCSP.
- The certificate to be verified does not have an OCSP path entered in the Authority Information Access (AIA) extension. Since this can be determined by an attacker under certain circumstances, this is problematic when CDP is provided.
- The OCSP Magic Number takes effect when CDP are configured in the certificate (for example, in domain controllers that verify smartcard logins). In this case, the application will prefer to use the revocation list because it thinks this would be more efficient.
That OCSP is used in all cases can only be ensured if the certificates issued do not contain CDP and the revocation lists are not accessible anywhere.
Alternatively, there is also the possibility, Instruct individual computers via group policy for specific certification authorities to use only the online responders.
Establishment
Install hotfix
For Windows Server 2012 R2, the hotfix must be KB2967917 must be installed. Windows Server 2016 and newer already include the hotfix.
Export serial numbers of certificates issued by certification authorities
Attached is the sample script from the aforementioned Knowledge Base article.
param(
[ValidateScript({test-path $_})]
[String] $Path
)
pushd $Path
dir | foreach {
remove-item $_ -force
}
certutil.exe -out serialnumber -restrict "Disposition = 20" -view | foreach {
if ($_ -match 'Serial Number: "([^"]+)"') {
New-Item -type File $matches[1] | out-null
}
}
popd
The script must be run regularly to keep the information about issued certificates in sync.
Alternatively, it is possible and also more elegant to write an exit module for this, which saves the serial numbers directly into the file system when a certificate is issued. See article "Create an exit module for the certification authority in C#„.
Configure the online responder to use the exported serial numbers for checking the certificate status
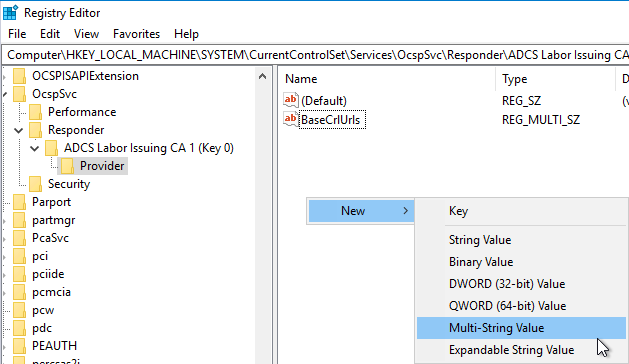
In order for the online responder to be able to check the exported serial numbers, the respective revocation configuration must be configured for this. There is no graphical interface or command line command for this. Instead, the path must be specified directly via a registry key.
To do this, navigate to the following directory using the registry editor:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\OcspSvc\Responder\{name-of-blocking-configuration}\Provider
A new multi-string value is created there.
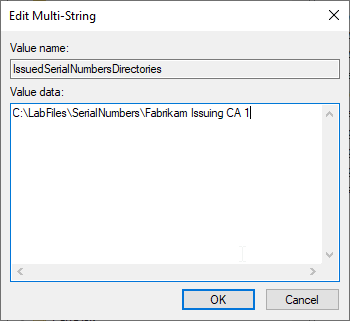
This is assigned the name "IssuedSerialNumbersDirectories".
The configured path, which contains the serial numbers, is configured as the content.
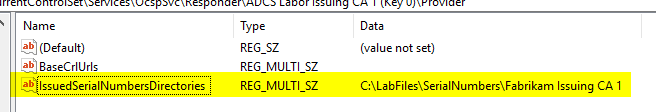
Apply the changes
After the configuration is completed, the online responder service must be restarted.
Restart service OCSPSvc
Result control
When the Auditing of OCSP events is activated and a certificate with an unknown serial number is requested for verification, the online responder now reports back a status of "Unknown" (to be viewed in event no. 5125).
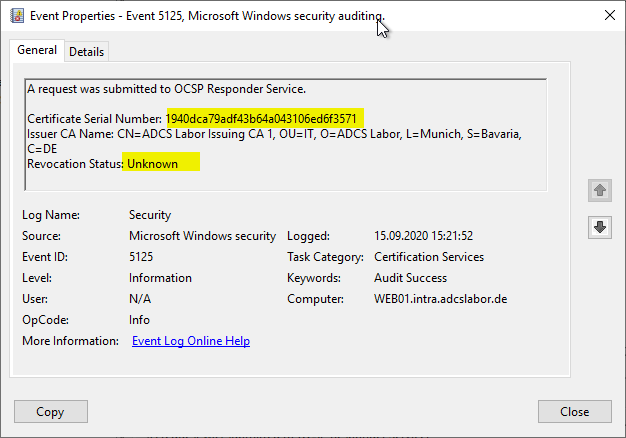
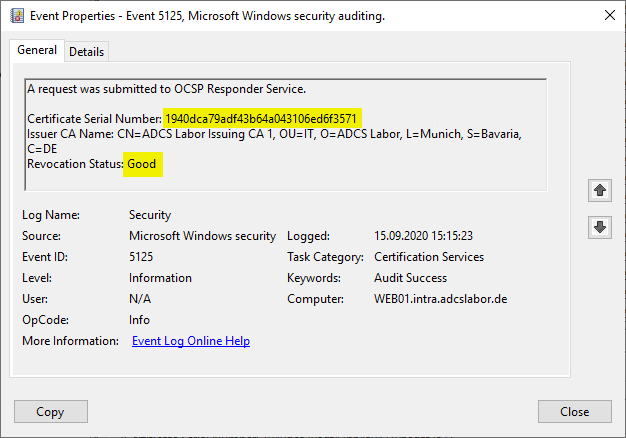
For comparison: If no deterministic Good is configured, the same certificate causes a status of "Good".
Related links:
- Force domain controller (or other participants) to use an online responder (OCSP)
- Attack vector on Active Directory directory service via smartcard logon mechanism
- Overview of the audit events generated by the online responder (OCSP)
10 thoughts on “Deterministisches „Good“ für den Onlineresponder (OCSP) konfigurieren”
Comments are closed.