In contrast to operational events, which are often understood under the term "monitoring", auditing for the certification authority is the configuration of logging of security-relevant events.
Auditing of security events must be enabled in two places:
- At the certification authority level. Here you define which event categories are to be logged by the Certification Authority. Optionally, an additional category of audit events can be enabled.
- At the operating system level. Here you specify that the events generated by the certification authority are written to the Windows security log.
If only one of the two settings is made, no security events are logged for the certification authority.
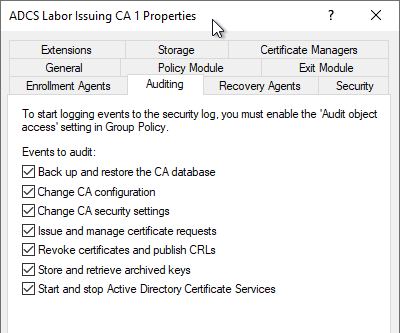
Verify audit settings at Certification Authority level
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
The audit settings can be viewed and modified via the Certification Authority Management Console (certsrv.msc) in the properties of the certification authority, in the "Auditing" tab.
It is also possible to query the audit settings with the following command line command:
certutil -getreg CA\Auditfilter
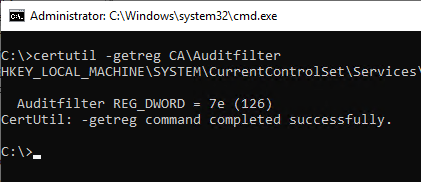
The audit settings are stored as a bit mask. The returned number can be broken down as follows:
| Value | Meaning | Enables events |
|---|---|---|
| 0 | Disable Auditing | |
| 1 | Start and stop Active Directory Certificate Services | 4880 and 4881 |
| 2 | Back up and restore the CA Database | tbd. |
| 4 | Issue and manage certificate requests | tbd. |
| 8 | Revoke certificates and publish CRLs | tbd. |
| 16 | Change CA security settings | tbd. |
| 32 | Store and retrieve archived keys | tbd. |
| 64 | Change CA configuration | tbd. |
The "Start and stop Active Directory Certificate Services" option causes a checksum of the certificate authority database to be generated each time the certificate authority service is stopped and started, which can cause performance degradation and side effects for larger databases. For more information, see the article "Performance problems with auditing of "Start and stop Active Directory Certificate Services"." to find.
Enable logging of audit events related to certificate template processing.
The events concerning the processing of certificate templates (event ID 4898, 4899 and 4900) are not generated until a corresponding configuration setting (the flag EDITF_AUDITCERTTEMPLATELOAD) was set on the certification authority.
certutil -setreg policy\EditFlags +EDITF_AUDITCERTTEMPLATELOAD
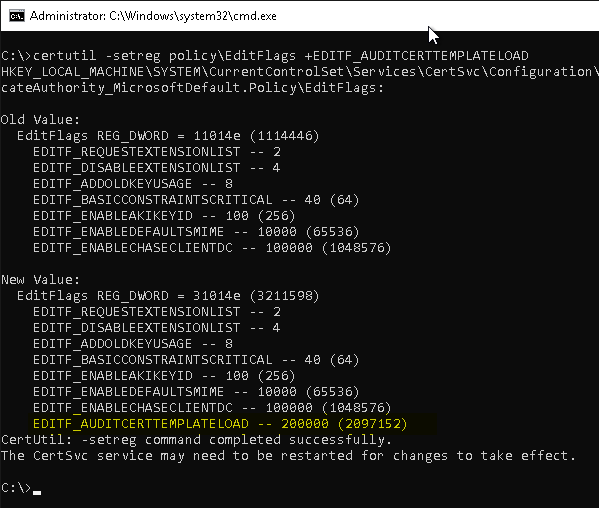
Subsequently, a restart of the Certification Authority service is required to apply the settings.
Enable audit settings at Certification Authority level
In addition to being able to configure the audit settings through the Certificate Authority Management Console, they can also be set using the following command line command.
certutil -getreg CA\Auditfilter {value}
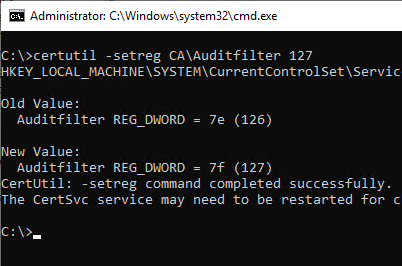
After the change, a restart of the certification authority service is necessary for the settings to be applied.
Check audit settings at operating system level
The audit settings on operating system level can be queried with the following command. In the "Object Access" area, there is a "Certification Services" category.
auditpol.exe /get /category:*
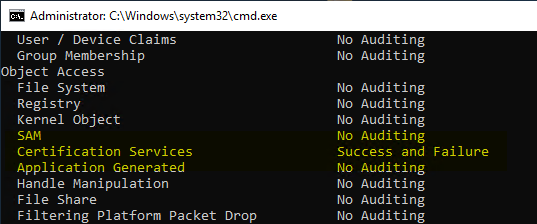
If Certification Services are configured for auditing via Group Policy, the default auditing settings are disabled. If no auditing setting is configured via a higher-level group policy (for example, the Microsoft Security Baselines), a corresponding group policy for a certification authority should therefore also contain the default audit settings. See the article "Standard auditing rules for Windows Server operating systems„.
Configure audit settings at operating system level via command line
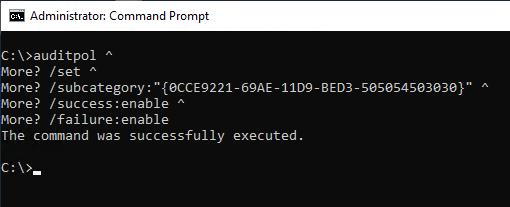
To enable auditing for certificate authority events at the operating system level, the following command line command can be used:
auditpol /set /subcategory:"{0CCE9221-69AE-11D9-BED3-505054503030}" /success:enable /failure:enable
Setting the auditing settings via the command line should only ever be understood as a stopgap solution, as they can be overridden at any time by a group policy with different settings. This method is therefore mainly suitable for offline certification authorities. For Active Directory integrated certification authorities, the audit settings should be set centrally via a group policy.
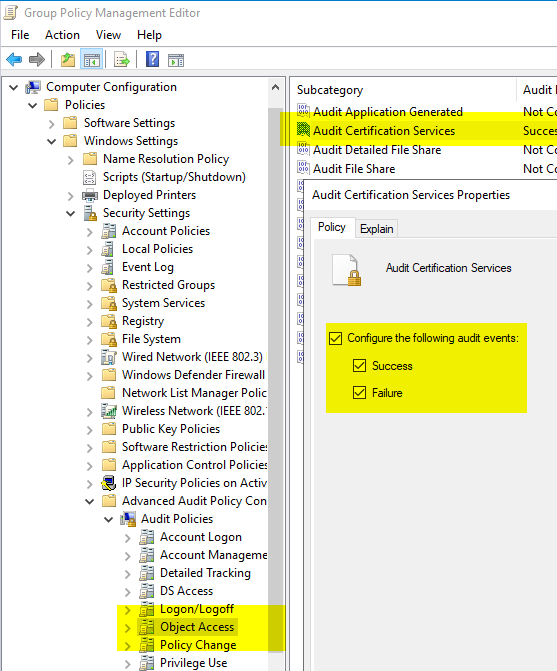
Configure audit settings at operating system level via group policy (recommended)
The settings are located under "Computer Configuration" - "Policies" - "Windows Settings" - "Security Settings" - "Advanced Audit Policy Configuration" - "Audit Policies" - "Object Access". There is a category "Audit Certification Services" which should be set to "Success" and "Failure".
If Certification Services are configured for auditing via Group Policy, the default auditing settings are disabled. If no auditing setting is configured via a higher-level group policy (for example, the Microsoft Security Baselines), a corresponding group policy for a certification authority should therefore also contain the default audit settings. See the article "Standard auditing rules for Windows Server operating systems„.
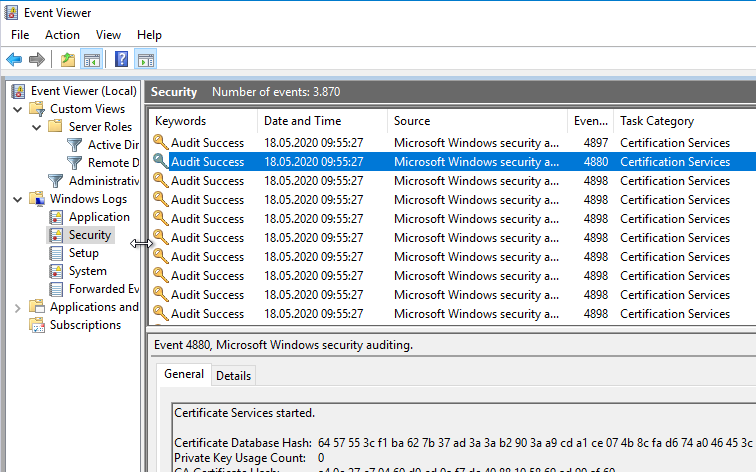
Result control
After the audit settings are enabled in both places, the certification authority should start writing appropriate events to the security log.
Related links:
- Overview of audit events generated by the Certification Authority
- Standard auditing rules for Windows Server operating systems
- Performance problems with auditing of "Start and stop Active Directory Certificate Services".
- Role configuration for the Network Device Enrollment Service (NDES) fails with error message "Failed to enroll RA certificates. The RPC server is unavailable. 0x800706ba (Win32: 1722 RPC_S_SERVER_UNAVAILABLE)".
6 thoughts on “Konfiguration der Überwachung von Sicherheitsereignissen (Auditierungseinstellungen) für Zertifizierungsstellen”
Comments are closed.