| Event Source: | Microsoft Windows Security Auditing |
| Event ID: | 5059 (0x13C3) |
| Event log: | Security |
| Event type: | Information |
| Event text (English): | Key migration operation. Subject: Security ID: %1 Account Name: %2 Account Domain: %3 Logon ID: %4 Cryptographic Parameters: Provider Name: %5 Algorithm Name: %6 Key Name: %7 Key Type: %8 Additional Information: Operation: %9 Return Code: |
| Event text (German): | Key migration process. Applicant: Security ID: %1 Account name: %2 Account domain: %3 Login ID: %4 Cryptographic parameters: Provider Name: %5 Algorithm Name: %6 Key Name: %7 Key Type: %8 Additional Information: Operation: %9 Return code: |
Parameter
The parameters contained in the event text are filled with the following fields:
- %1: SubjectUserSid (win:SID)
- %2: SubjectUserName (win:UnicodeString)
- %3: SubjectDomainName (win:UnicodeString)
- %4: SubjectLogonId (win:HexInt64)
- %5: ProviderName (win:UnicodeString)
- %6: AlgorithmName (win:UnicodeString)
- %7: KeyName (win:UnicodeString)
- %8: KeyType (win:UnicodeString)
- %9: Operation (win:UnicodeString)
- : ReturnCode (win:HexInt32)
In contrast to operational events, which are often understood under the term "monitoring", auditing for the certification authority is the configuration of logging of security-relevant events.
Example events
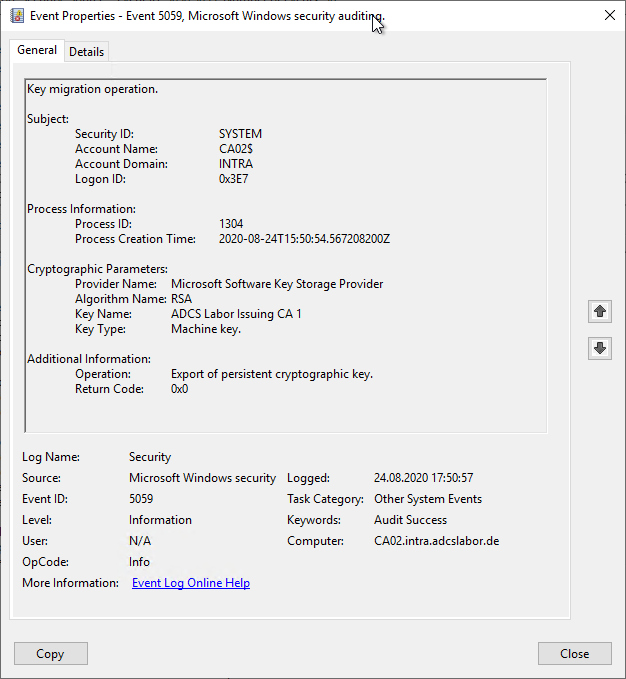
Key migration operation.
Subject:
Security ID: SYSTEM
Account Name: CA02$
Account Domain: INTRA
Logon ID: 0x3E7
Process Information:
Process ID: 1304
Process Creation Time: 2020-08-24T15:50:54.567208200Z
Cryptographic Parameters:
Provider Name: Microsoft Software Key Storage Provider
Algorithm Name: RSA
Key Name: ADCS Labor Issuing CA 1
Key Type: Machine key.
Additional Information:
Operation: Export of persistent cryptographic key.
Return Code: 0x0
Description
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
This event occurs when accessing a Software-based key on. The same applies if a certification authority has a software key and accesses it.
It occurs together with the Event with ID 5058 of source Microsoft-Windows-Security-Auditing on.
The event occurs only when the Auditing is activated for "Other System Events".
Safety assessment
The security assessment is based on the three dimensions of confidentiality, integrity and availability.
This event can be evaluated as critical for integrity if there is an access to the certification authority key away from the certification authority context. The certification authority service runs in the "SYSTEM" context.
It is therefore a good idea to set up monitoring for this event and filter it using the following criteria:
- Access is not through the "SYSTEM" account.
- (Optional) Access is to a specific named key (see event details.
Windows Event Forwarding (WEF) example:
{QueryList}
{Query Id="0" Path="Security"}
{Select Path="Security"}
*[System[(EventID='5058') or (EventID='5059')]] and
*[EventData[Data[@Name="SubjectLogonId"] != "0x3e7"]]
{/Select}
{/Query}
{/QueryList}
Related links:
- Overview of audit events generated by the Certification Authority
- Overview of the audit events generated by the online responder (OCSP)
- Basics: Cryptographic Service Provider (CSP) and Key Storage Provider (KSP)
External sources
- 5059(S, F): Key migration operation. (Microsoft Corporation)
4 thoughts on “Details zum Ereignis mit ID 5059 der Quelle Microsoft-Windows-Security-Auditing”
Comments are closed.