There are cases in which you cannot or do not want to obtain web server certificates directly from a certification authority in your own Active Directory forest via the Microsoft Management Console, for example if the system in question is not a domain member.
In this case, the use of certificate templates is not possible, and one must manually create a Certificate Signing Request (CSR).
Preliminary work
If the certificate request is to be answered by an Active Directory integrated certification authority, a corresponding certificate template must be defined for this authority. The procedure for this is described in the article "Configuring a Secure Socket Layer (SSL) Certificate Template for Web Server" described.
Generate the key pair and certificate request
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
There are several ways to create the key pair and certificate request. The following two methods are described below:
- Generate the certificate request using Windows standard tools (graphical user interface, certlm.msc)
- Generate the certificate request using Windows onboard resources (command line, certreq.exe)
- Generating the certificate request with the PSCertificateEnrollment PowerShell module
Method 1: Creating the certificate request using Windows standard tools (graphical user interface, certlm.msc)
The following method assumes that the machine is a member of the same Active Directory forest as the certification authority.
Web server certificates are generated and stored in the computer certificate store. The certificate request is therefore made via the management console for computer certificates (certlm.msc), which must now be called up.
Local administrator authorizations on the machine are required for this step.
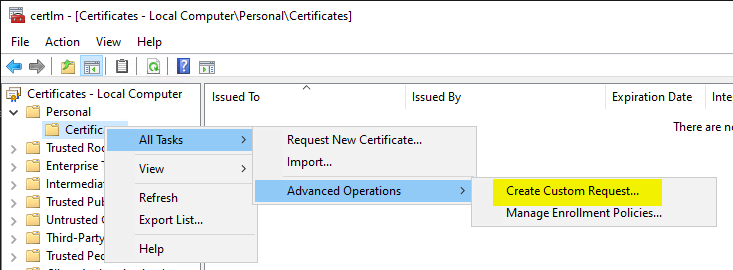
Our aim is to save the certificate request as a file after it has been created. To achieve this, we click on the right under "Personal" / "Certificates" and select "All Tasks" / "Advanced Operations" / "Create Custom Request...".
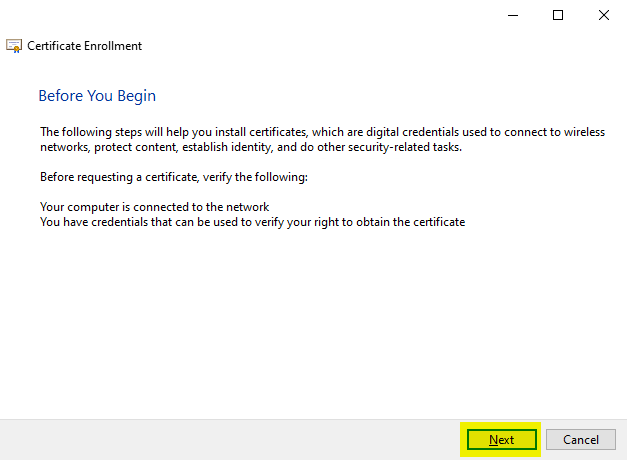
In the following dialog, we can continue by clicking on "Next".
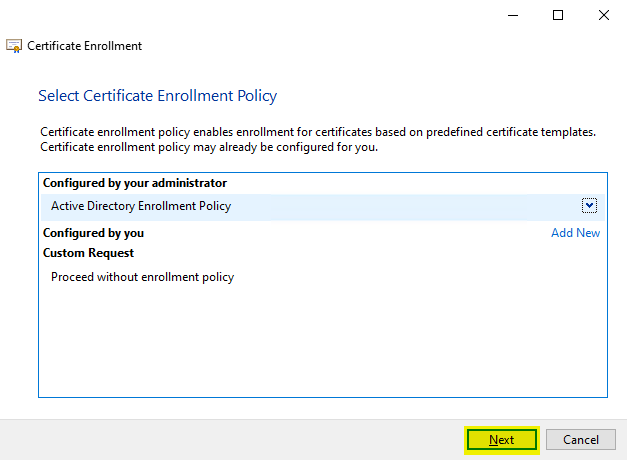
In the following dialog, we can (in most cases) continue by clicking on "Next".
In rare cases, an enrollment policy may need to be configured. For background information on this, see the article "Certificate request basics via Certificate Enrollment Web Services (CEP, CES)„).
In the following dialog, the desired certificate template can be selected. Once you have made your selection, you can continue by clicking on "Next".
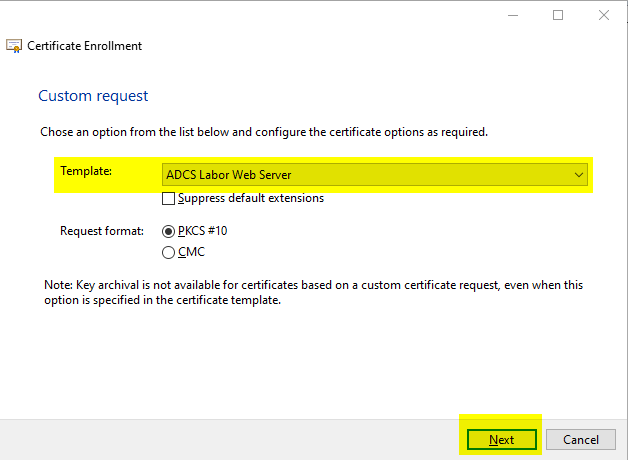
In the following dialog, it is important to activate further options by clicking on "Details".
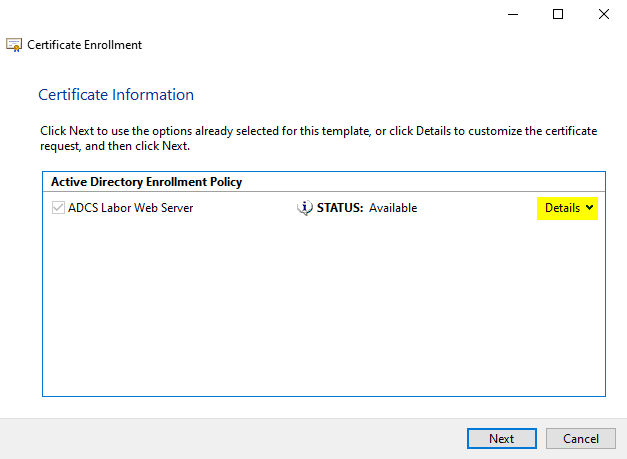
Click on "Properties" in the dialog box that now opens.
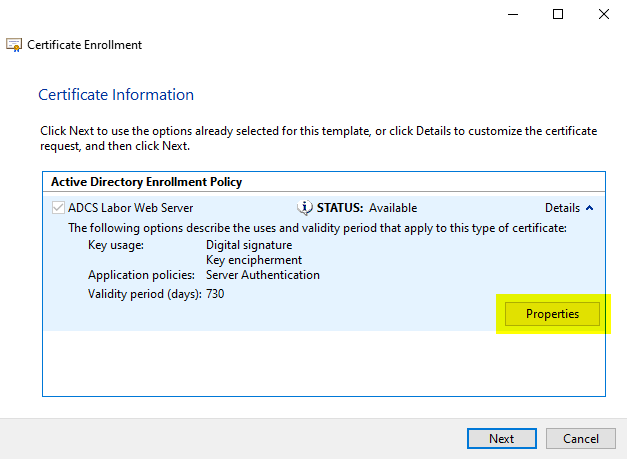
In the dialog that now opens, the identities that the certificate request should contain can be configured in the "Subject" tab.
RFC 2818 is decisive for web server certificates. This requires that the identities are to be mapped via the Subject Alternative Name (SAN) of type dNSName.
However, it can also be useful to store a commonName. This should be ignored according to RFC, but allows applications that are not compliant to make a fallback.
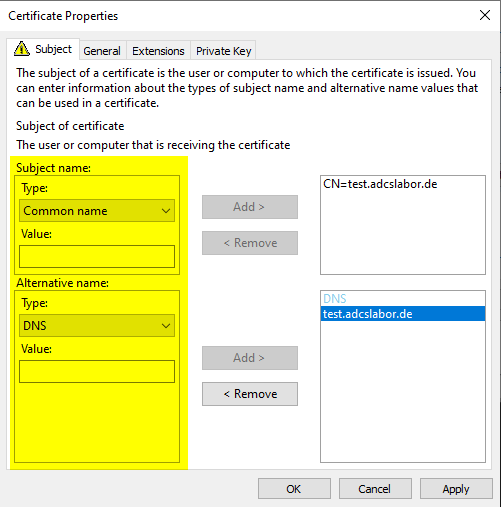
Optionally, the private key can be made exportable in the "Private Key" tab.
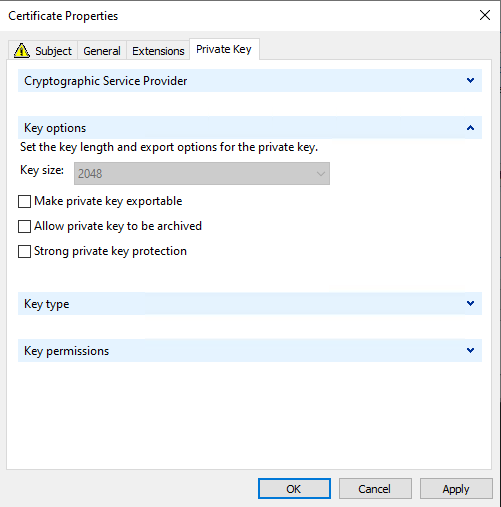
The dialog can now be closed and continued with "Next".
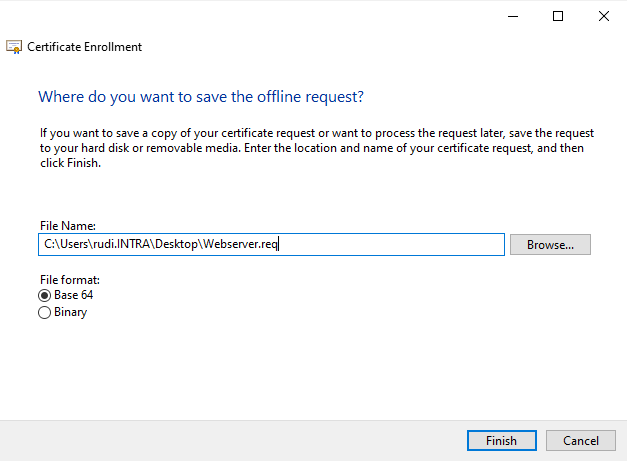
Finally, the certificate application is saved as a file and the process is ended with "Finish".
Method 2: Generating the certificate request using Windows onboard resources (command line, certreq.exe)
If the certificate request is to be made using Windows on-board resources, an information file (.inf) for the certificate request must first be created.
The information file must be saved with UTF-8 encoding. If the encoding is different, the certificate request creation will fail (see article "Creation of a manual certificate request fails with error message "Expected INF file section name 0xe0000000".„).
The following file is used to generate a certificate request for an SSL certificate that contains a 3072-bit key and "test.intra.adcslabor.de" as both the "commonName" within the subject and the "dNSName" within the alternate requestor name.
[Version]
Signature="$Windows NT$"
[Strings]
; Adapt the following variable to the environment
SERVER_FQDN = "test.intra.adcslabor.de"
; Do not edit the following strings
; ----------------------------------------------------------------
szOID_SUBJECT_ALT_NAME2 = "2.5.29.17"
szOID_ENHANCED_KEY_USAGE = "2.5.29.37"
szOID_PKIX_KP_SERVER_AUTH = "1.3.6.1.5.7.3.1"
[NewRequest]
Subject = "CN=%SERVER_FQDN%"
Exportable = FALSE
MachineKeySet = True
KeyLength = 3072
KeyUsage = 0xA0 ; Digital Signature, Key Encipherment
ProviderName = "Microsoft Software Key Storage Provider".
[Extensions]
%szOID_SUBJECT_ALT_NAME2% = "{text}dns=%SERVER_FQDN%"
%szOID_ENHANCED_KEY_USAGE% = "{text}%szOID_PKIX_KP_SERVER_AUTH%"
For background information on each option, see the following articles:
- Basics: The Key Usage Certificate Extension
- What key lengths should be used for certificate authorities and certificates?
- Basics: Cryptographic Service Provider (CSP) and Key Storage Provider (KSP)
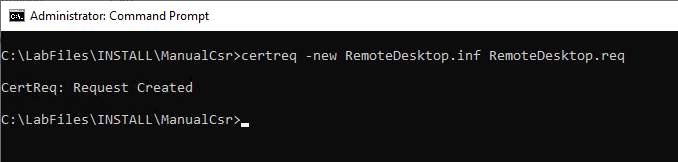
Now a key pair and a certificate request can be generated using this information file. The following command generates the certificate request.
certreq.exe -new {information file}.inf {certificate request}.req
A certificate request with file extension .req is generated from the .inf file.
The command must be listed on the system on which the certificate is to be used later. The key pair is generated on this, the private key never leaves the system.
Method 3: Generating the certificate request with the PSCertificateEnrollment PowerShell module
The PSCertificateEnrollment PowerShell module can be accessed via the PowerShell Gallery obtained and then loaded.
Install-Module -Name PSCertificateEnrollment
Import-Module -Name PSCertificateEnrollment
To create the certificate request, Windows PowerShell must be started as an administrator, since the key pair for a web server should usually be created in the system context.
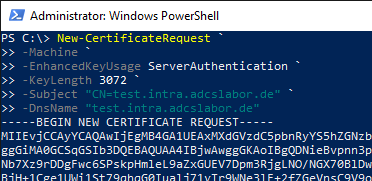
The following command generates a certificate request for an SSL certificate that includes a 3072-bit key and "test.intra.adcslabor.de" as both the common name within the subject and the DNS name within the alternate requestor name.
New-CertificateRequest ` -Machine ` -EnhancedKeyUsage ServerAuthentication ` -KeyLength 3072 ` -Subject "CN=test.intra.adcslabor.de" ` -DnsName "test.intra.adcslabor.de"
With the -Exportable argument can optionally be specified that the private key should be exportable.
Verify the certificate request
The certificate request now generated can be viewed if desired with the following command line command:
certutil -dump {certificate request}.req
See also article "Inspect a certificate request (CSR)„.
Sending the certificate request to the certification authority
Sending a certificate request to a certification authority and collecting the issued certificate is described in the article "Send a manually created certificate request to a certification authority" described.
Installation of the issued certificate
The certificate can now be copied to the computer. It must now be installed in the certificate store and linked to the private key. This is done with the following command line command:
certreq -accept {filename certificate}
Activation of the certificate and subsequent function test
The certificate must now be bound to the specific application (for example, Internet Information Services). This process is specific to the web server product in question.
Related links:
- Manually requesting a Remote Desktop (RDP) certificate
- Manual application for a domain controller certificate
External sources
- How to Request a Certificate With a Custom Subject Alternative Name (Microsoft)
- certreq (Microsoft)
- Object IDs associated with Microsoft cryptography (Microsoft)
8 thoughts on “Manuelle Beantragung eines Webserver-Zertifikats”
Comments are closed.