The ACME protocol was developed by the operators of the project Let's Encrypt designed to support the exhibition of Web server certificates to automate. It is specified in RFC 8555.
The goal is to make the process of proving ownership of the DNS resource (IP addresses cannot currently be identified, but this is planned in the future), but not of the person or organization behind it, in order to subsequently be able to obtain a web server certificate without human interaction.
The motivation for developing this protocol arose because the existing certification authorities used proprietary processes that could not be automated and were correspondingly error-prone, making it misstatements occurred. Likewise, automation is expected to improve the user experience and achieve a higher penetration rate of SSL usage among web servers.
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
Functionality
Using the ACME protocol, applicants can apply for and also revoke certificates for the DNS identities in their possession fully automatically.
The messages are formatted in JSON, encoded using UTF8, and transmitted using HTTPS. The JSON messages use JSON Web Security (JWS) to provide anti-replay, message authentication, and integrity protection. Binary data is encoded in BASE64.
In communication, there are the roles of "client" (applicant) and "server" (the ACME server instance, the RFC also speaks of the certification authority in this case, although strictly speaking it is only a registration authority or interface).
Certificate request
It is intended that the client can choose from several ACME-enabled certificate authorities.
The procedure is as follows:
- Create an account (newAccount). Optionally, contact information can be stored and consent to the terms and conditions of the PKI can be given. The account creation request is signed with a previously generated private key.
- Ordering a certificate (newOrder).
- prove possession of the identities contained in the order (the ways to do this are determined by the server in response to the previously received order).
- Send certificate requests.
- Request issuance of the certificate and pick up/download the certificate.
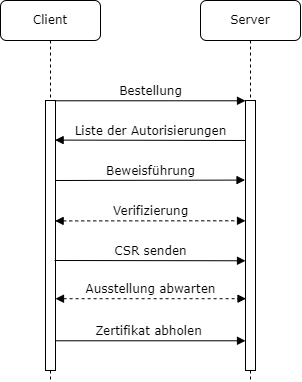
The ACME server briefly acts as an HTTP or DNS client during the verification of identities.
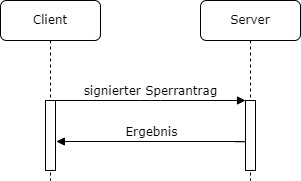
Lock request
It is also possible to use ACME to request revocation of a previously issued certificate.
- Sending a signed lock request (revokeCert).
- The ACME server communicates the result.
Certificate renewal
By creating an account, contact information and a link between the applicant and the issued certificate can be established. This makes it possible, for example, to notify the applicant when the certificate is approaching the end of its validity period.
The requester can thus be reminded to renew the certificate in good time. However, notification of certificate expiration is not mandatory and is not necessary in every case, since certificate renewal can also be performed proactively (and automatically) by the applicant.
What ACME cannot do
The ACME protocol cannot determine whether an attacker has taken control of a DNS domain or an individual host. Certificates are issued if the required proof is successful. Therefore, it is not suitable for all use cases. Extended validation (EV) cannot be mapped with the protocol.
The ACME protocol assumes that the service is provided free of charge. Accordingly, there is no methodology to implement billability. However, due to the required creation of an account prior to certificate issuance, such logic could be implemented through custom development.
ACME for Active Directory Certificate Services
An ACME interface is also very beneficial for an internal certificate authority. Automating the application and issuance of web server certificates improves the user experience and acceptance for the use of HTTPS, reduces the workload of PKI staff and minimizes errors during certificate issuance.
However, the Active Directory Certificate Services bring unfortunately no support for the ACME protocol out of the box with. There are commercial solutions like certACME from Secardeo or xc from essendi it, which can fill this gap.
It exists with ACME Server ADCS also an open source solution published on GitHub. Please note that the project may be used free of charge for study purposes only. For commercial use, a license must be purchased from the author.
Related links:
External sources
- Automatic Certificate Management Environment (ACME) (Internet Engineering Task Force)
- ACME Server ADCS (GitHub / Thomas Ottenhus)
One thought on “Grundlagen: Automatic Certificate Management Environment (ACME)”
Comments are closed.