There are cases in which you cannot or do not want to obtain Remote Desktop certificates from a certificate authority in your own Active Directory forest, for example, if the system in question is not a domain member.
In this case, the use of certificate templates is not possible, and one must manually create a Certificate Signing Request (CSR).
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
Preliminary work
Before applying for Remote Desktop certificates, the following requirements should be met:
- Active Directory subscribers must trust the certificate authority hierarchy. If the Remote Desktop certificates are issued by a third-party certificate authority, the root certificate authority certificate must be made known to all participants. This can be done, for example, via group policy, which is described in the article "Distribute Trusted Root Certification Authorities via Group Policy" is described in more detail.
- In order to check the revocation status of the certificates, it must be ensured that they can be resolved (Domain Name System) as well as downloaded (routing, proxy, firewall rules) by all participants.
Inventory for the manual creation of a certificate request
First, the content of the certificate request must be determined. One of the standard certificate templates for domain controllers can serve as a reference point for this. In the following example, we will use the template described in the article "Configuring a Certificate Template for Remote Desktop (RDP) Certificates"certificate template for Remote Desktop certificates.
In the "Request Handling" tab you can see that the movement of the certificate template is set to "Signature and Encryption", which means that the Key Usage extension of the certificate will contain "Key Encipherment" and "Digital Signature", i.e. the hexadecimal value A0. This must already be taken into account during key creation on the requesting computer.
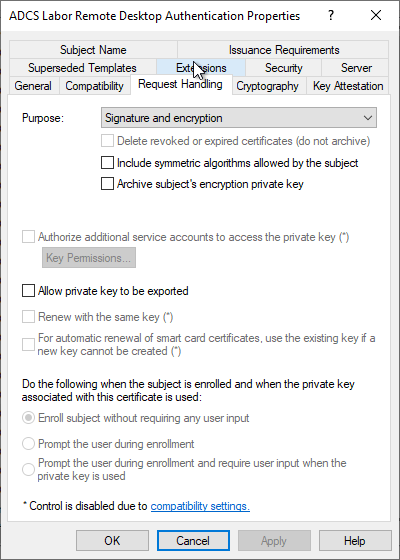
In the "Cryptography" tab, the key algorithm, the key length and the Cryptographic Service Provider (CSP) are relevant for us. The Remote Desktop template still uses "legacy" providers, i.e. CSPs that only support RSA. The key length is set to 2048 bits and the "Microsoft RSA SChannel Cryptographic Provider" is used.
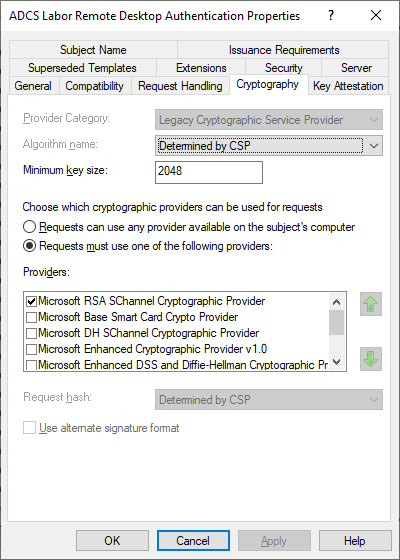
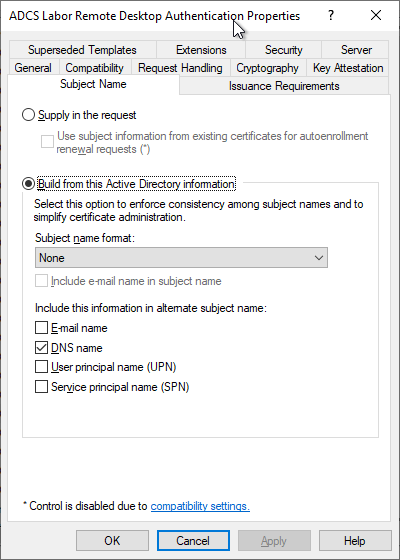
In the "Subject Name" tab we see that the Subject is empty and a Subject Alternative Name is selected in the form of a DNS name.
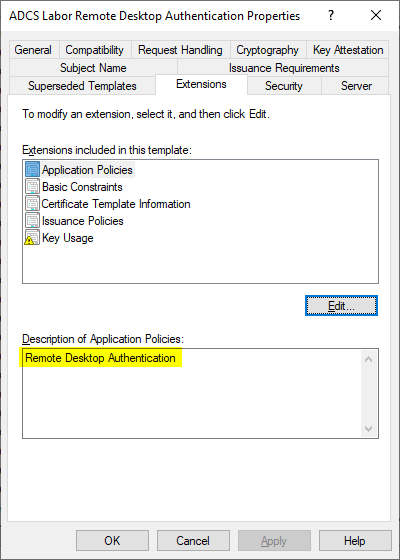
In the "Extensions" tab we see that the following values are set as Extended Key Usage (Application Policies):
- Remote Desktop Authentication (Object Identifier: 1.3.6.1.4.1.311.54.1.2)
Create Certificate Template for Manual Remote Desktop Certificate Enrollment
If the certificate request is to be answered by an Active Directory integrated certification authority, a corresponding certificate template must be defined for this authority. The procedure for this is described in the article "Configuring a Certificate Template for Remote Desktop (RDP) Certificatesis described in the "Subject Name" tab. For manual requests, however, it must be configured differently in the "Subject Name" tab that the requester can specify the identity with the certificate request.
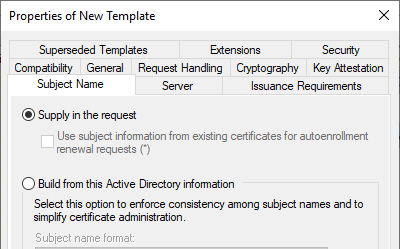
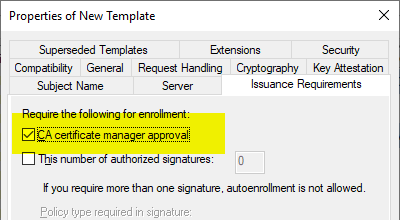
However, since this can pose a security problem, the certificate requirements should be approved by a certificate manager, which can be achieved by enabling the "CA certificate manager approval" option in the "Issuance Requirements" tab.
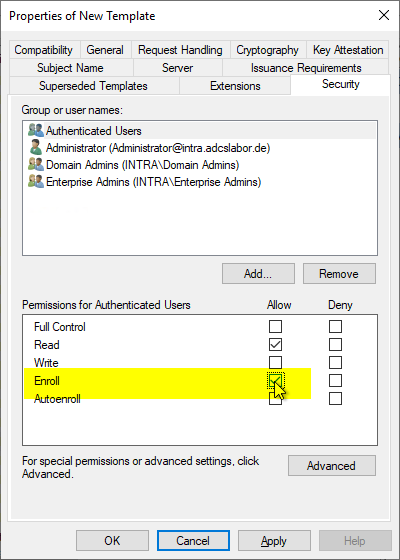
Since a user account instead of a computer account will make the certificate request in the case of a manual certificate request, the corresponding user or a security group of which he is a member must be granted the "Enroll" right.
Create information file for manual certificate request
From all this information, an information file (.inf) can now be created for the certificate request. Below is an example that should generate a certificate request analogous to the Kerberos Authentication certificate template:
The information file must be saved with UTF-8 encoding. If the encoding is different, the certificate request creation will fail (see article "Creation of a manual certificate request fails with error message "Expected INF file section name 0xe0000000".„).
[Version]
Signature="$Windows NT$"
[Strings]
; Adapt the following variable to the environment
SERVER_FQDN = "CA01.intra.adcslabor.de"
; Do not edit the following strings
szOID_SUBJECT_ALT_NAME2 = "2.5.29.17"
szOID_ENHANCED_KEY_USAGE = "2.5.29.37"
szOID_KP_RDC_AUTH = "1.3.6.1.4.1.311.54.1.2"
[NewRequest]
According to RFC2818, the subject should no longer be used and may be empty (Subject =)
Subject = "CN="
; The private key is not exportable
Exportable = FALSE
; The key pair is generated in the local machine memory
MachineKeySet = True
; Recommended key lengths: 2048, 3072, 4096
; 2048 bits should only be used until 2021
; Compatibility should be ensured before increasing the key length
KeyLength = 3072
; AT_KEYEXCHANGE
KeySpec = 1
; Digital Signature, Key Encipherment
KeyUsage = 0xA0
ProviderName = "Microsoft RSA SChannel Cryptographic Provider"
ProviderType = 12
SMIME = FALSE
RequestType = CMC
[Extensions]
%szOID_SUBJECT_ALT_NAME2% = "{text}dns=%SERVER_FQDN%"
%szOID_ENHANCED_KEY_USAGE% = "{text}%szOID_KP_RDC_AUTH%"
Generating the key pair and the certificate request
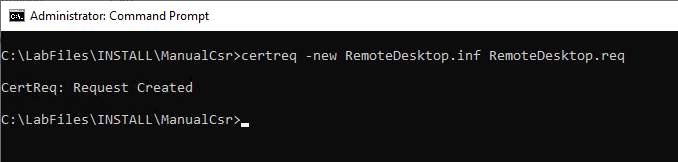
Now a key pair and a certificate request can be generated using this information file. The creation is done on the computer as administrator via command line with the following command:
certreq.exe -new {information file}.inf {certificate request}.req
The certificate request now generated can be viewed if desired with the following command line command:
certutil -dump {certificate request}.req
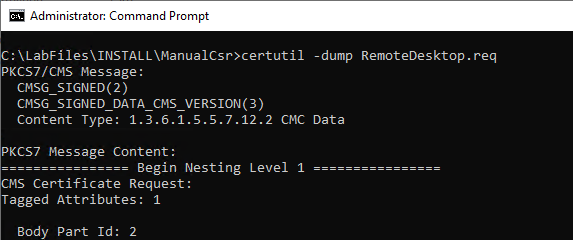
Sending the certificate request to the certification authority
Sending a certificate request to a certification authority and collecting the issued certificate is described in the article "Send a manually created certificate request to a certification authority" described.
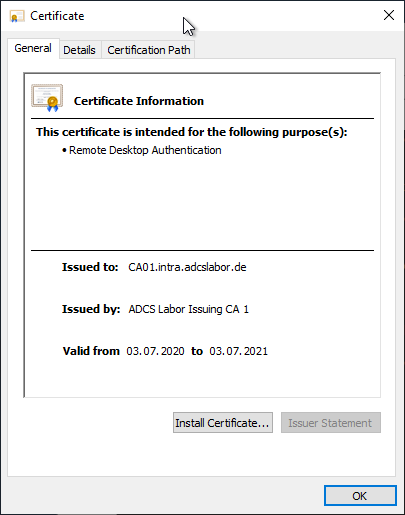
Installation of the issued certificate
The certificate can now be copied to the computer. It must now be installed in the certificate store and linked to the private key. This is done with the following command line command:
certreq -accept {certificate}
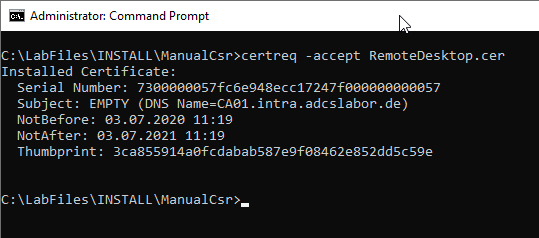
Activation of the certificate and subsequent function test
The assignment of the certificate to the Remote Desktop session host is described in the article "Manually assigning a Remote Desktop (RDP) certificate" described.
How to identify the currently used Remote Desktop certificate is described in the article "Identify the active Remote Desktop (RDP) certificate" described.
Related links:
- Manually assigning a Remote Desktop (RDP) certificate
- Identify the active Remote Desktop (RDP) certificate
- Configuring a Certificate Template for Remote Desktop (RDP) Certificates
- Configuring a Group Policy (GPO) for Remote Desktop (RDP) Certificates
External sources
- How to Request a Certificate With a Custom Subject Alternative Name (Microsoft)
- certreq (Microsoft)
- Object IDs associated with Microsoft cryptography (Microsoft)
4 thoughts on “Manuelle Beantragung eines Remotedesktop (RDP) Zertifikats”
Comments are closed.