Often, before submitting a certificate request to a certification authority - or before issuing the certificate - you want to verify that it contains the desired values.
The following describes how to achieve this.
There are two ways to inspect a certificate request:
- Inspect a certificate request before submission
- Inspect a certificate request after submission
Inspect a certificate request before submission
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
Assume that a certificate request is available as a text file. If you open it, you will encounter either binary data or the BASE64 encoded variant as shown in the picture.
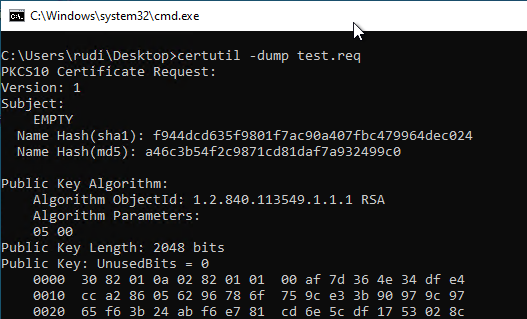
In every current Windows version there is the utility certutilwhich can be used to decode such a file and make it readable. The following is an example:
certutil -dump {filename certificate request}
Inspect a certificate request after submission
Assume that the certificate request has already been submitted to the certification authority, but the certificate has not been issued directly, but configured for approval by a certificate manager, as recommended for web server certificates, for example.
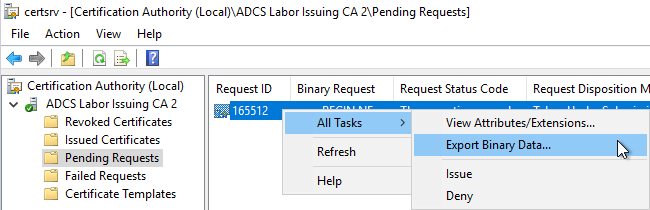
In this case a certificate manager can check the pending certificate request via the Certificate Authority Management Console (certsrv.msc). Under "Pending Requests" right-click on the certificate request and select "All Tasks" - "Export Binary Data...".
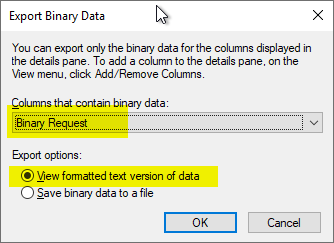
In the following selection one chooses the database column "Binary Request" and the option "View formatted text version of data".
Afterwards, you get the same view as the previous certutil command, but exported to a text file.
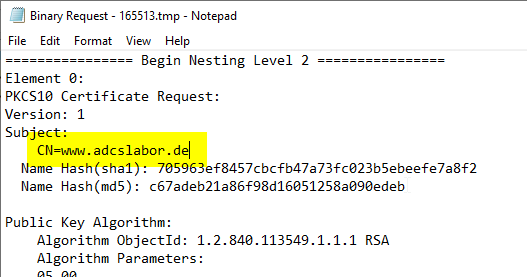
Inspect a certificate request after the certificate has been issued
If the certificate has already been issued, the associated certificate request is nevertheless stored in the certification authority database and can thus still be retrieved even after it has been issued.
To do this, navigate to "Issued Certificates" and select the "View" - "Add/Remove Columns..." option from the menu.
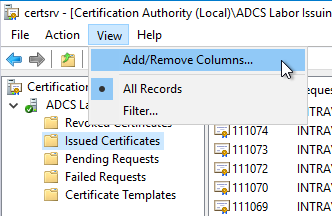
Add the "Binary Request" column by selecting it and clicking on "Add ->".
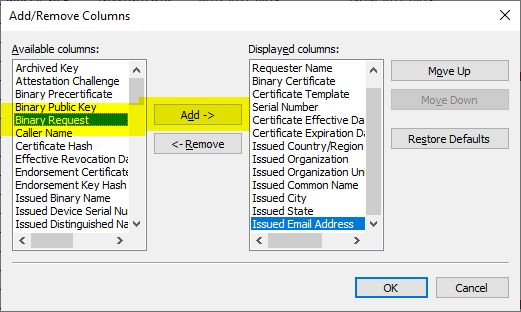
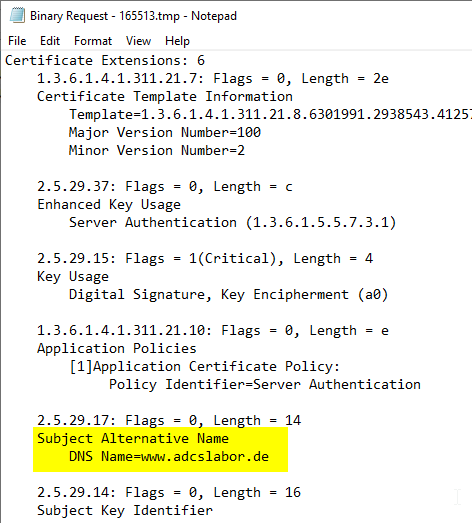
Afterwards, the certificate request can be inspected analogously to the previous procedure.
What information should a certificate manager look for
In addition to the Common Name, the Subject Alternative Name (SAN) should definitely be looked for. According to RFC2818, this should be used preferentially, at least for HTTPS, in order to map the identity. If a SAN is available, it can be found below under Certificate Extensions.
If a certificate request does not include a Subject Alternative Name (SAN), this can be be added subsequently by the certificate managerwhich is recommended for web server certificates.
Under certain circumstances, the subject of a certificate request can be changed by a certificate manager. How this is achieved, in the article "Subsequently change the subject of a certificate request (CSR)." described.
Both pieces of information should be checked for conformity with the certificate's own policy. Certificate requests that contain unauthorized domain names, for example, should be rejected.
7 thoughts on “Eine Zertifikatanforderung (CSR) inspizieren”
Comments are closed.