Since Windows 8, it has been possible for private keys for certificates to be protected with a - if available - Trusted Platform Module (TPM). This ensures that the key is truly non-exportable.
The process for setting up a certificate template that uses a Trusted Platform module is described below.
The configuration of your certificate template described below to use the Microsoft Platform Crypto Provider is merely a default setting for the requesting client. The certification authority cannot guarantee that the applicant is actually using a trusted platform module. To achieve this level of security, the additional TPM Key Attestation be used.
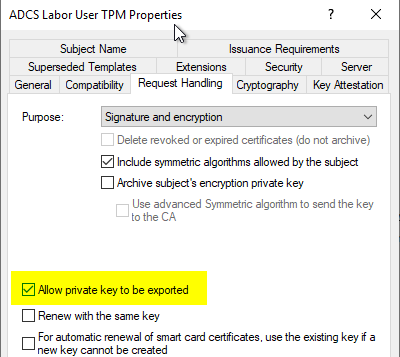
Private key must not be configured as exportable
In the Request Handling tab, make sure that the Allow private key to be exported option is not enabled. The Microsoft Platform Crypto Provider does not support key export. If the option is enabled, certificate requests will fail (see the article "Requesting a Trusted Platform Module (TPM) protected certificate fails with error message "The requested operation is not supported. 0x80090029 (-2146893783 NTE_NOT_SUPPORTED)"„).
Configuring the Key Storage Provider
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
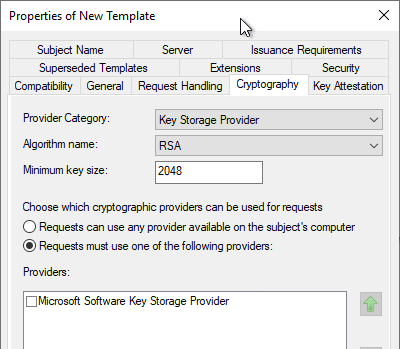
In most cases, when you open the Cryptography tab, you will find that the Microsoft Platform Crypto Provider - is not available despite correct configuration of the compatibility settings of the certificate template. This is due to the fact that only key storage providers that are available and usable on the current system are displayed.
If the computer running the Certificate Template Management Console does not have a Trusted Platform module, it is not possible to select the corresponding KSP.
There are several ways around this problem:
- Installation of the Remote Server Administration Tools (RSAT) on a computer (preferably a Privileged Admin Workstation (PAW)) with Trusted Platform module and configuration of the certificate template from there (see also article "Installing Remote Server Administration Tools for Active Directory Certificate Services on Windows 10 version 1809 and later„).
- Editing the pKIDefaultCSPs attribute using certutil.
- Editing the pKIDefaultCSPs attribute using Windows PowerShell.
- Edit the pKIDefaultCSPs attribute using ADSI Editor.
Editing the pKIDefaultCSPs Attribute Using Windows PowerShell
The list of Key Storage Providers is stored in the LDAP object of the certificate template in the attribute pKDefaultCSPs. There it can be changed with Windows PowerShell (ActiveDirectory module).
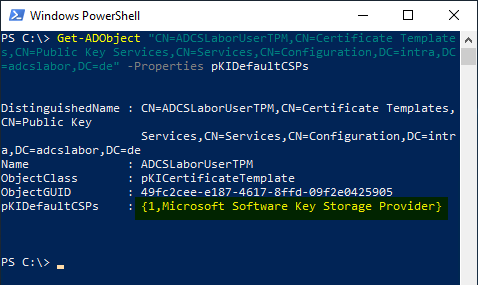
The current value can be displayed with the following command:
Get-ADObject "CN=ADCSLaborUserTPM,CN=Certificate Templates,CN=Public Key Services,CN=Services,CN=Configuration,DC=intra,DC=adcslabor,DC=de" -Properties pKIDefaultCSPs
If the attribute is not displayed, this may be because it is empty by default, i.e. not defined.
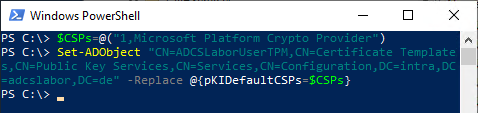
The following two commands can be used to change the content of the attribute. The "Microsoft Platform Crypto Provider" must be configured:
$CSPs=@("1,Microsoft Platform Crypto Provider")
Set-ADObject "CN=ADCSLaborUserTPM,CN=Certificate Templates,CN=Public Key Services,CN=Services,CN=Configuration,DC=intra,DC=adcslabor,DC=de" -Replace @{pKIDefaultCSPs=$CSPs}
To check, you can ensure the change by querying the value again.
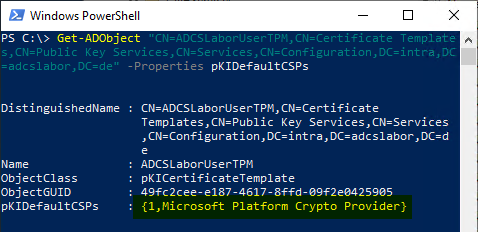
Please note that the pKIDefaultCSPs attribute can be overwritten by the certificate template management console. Therefore, after each change to the certificate template, it is necessary to check whether the attribute is set correctly again.
Editing the pKIDefaultCSPs attribute using ADSI Editor
The change is analogously also possible via the ADSI editor. The information can be found in the "Configuration" partition of the overall structure.
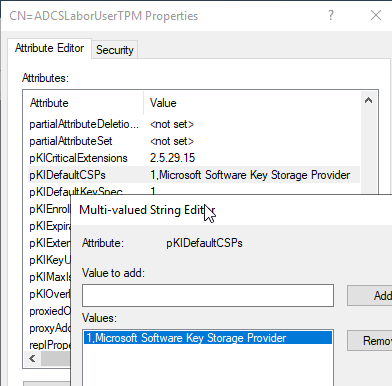
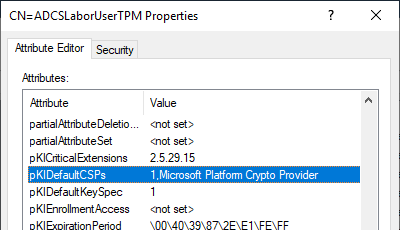
No certificates are requested if no TPM is present
No Certificate Enrollment is made on systems that do not have a Trusted Platform module. If these systems are also to be served with certificates, a software key storage provider can also be stored as a second entry.
6 thoughts on “Konfigurieren einer Zertifikatvorlage für die Verwendung des Microsoft Platform Crypto Provider, um Schutz des privaten Schlüssels durch ein Trusted Platform Module (TPM) zu ermöglichen”
Comments are closed.