Since Windows 8 it is possible, that private keys for certificates are protected with a - if available - Trusted Platform Module (TPM). This makes the key non-exportable - even with tools like mimikatz.
However, it is not obvious at first glance that it cannot be guaranteed that a TPM is really used. Although no application via Microsoft Management Console or AutoEnrollment possible if the computer does not have a TPM.
However, the configuration in the certificate template is merely a default setting for the client. The certification authority will not explicitly check whether a trusted platform module has actually been used when a request is made.
Thus - if the certificate request is done away from the MMC - arbitrary parameters can be used for the private key.
For demonstration purposes, for example, the PSCertificateEnrollment PowerShell module can be used. We use the Microsoft Software Key Storage Provider to generate the key pair and mark the private key as exportable.
New-CertificateRequest ` -Exportable ` -Upn "rudi@intra.adcslabor.de" ` -Ksp "Microsoft Software Key Storage Provider
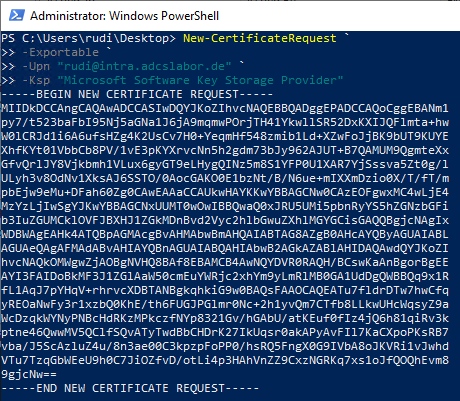
To be on the safe side, you can take a look at the generated certificate request. There is an attribute "Enrollment CSP" which contains the key storage provider used.
certutil noTPM.req
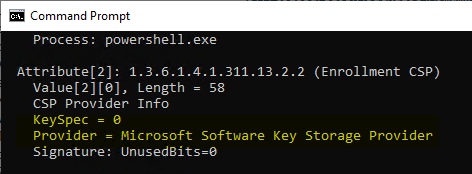
The certificate request is then sent to the certification authority. We include the server name of the certification authority as well as the name of the certificate template to be used.
certreq ^ -config "CA02.intra.adcslabor.de\ADCS Lab Issuing CA 1" ^ -attrib "CertificateTemplate:ADCSLaborUserTPM" ^ -submit noTPM.req
As a rule, the certification authority will now issue the certificate. At this point, proof has already been provided that there is no check of the CSP/KSP used by the certification authority.
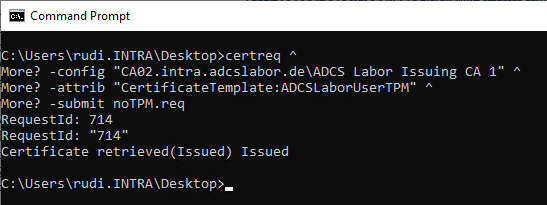
The certificate can now be installed locally.
certreq -accept noTPM.cer
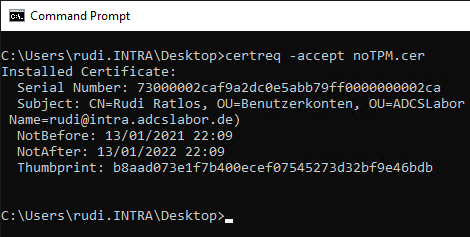
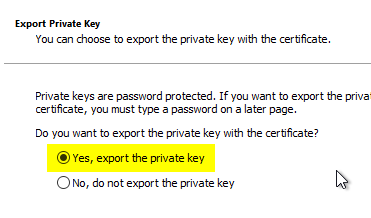
We will be able to export the private key.
Countermeasures
The TameMyCerts Policy Module for Microsoft Certification Authority allows certificate requests to be restricted to certain process names and cryptographic providers. However, the attributes evaluated for the decision-making process could be manipulated by the enrollee with a corresponding amount of effort, so it is not possible to speak of full protection here.
TameMyCerts is open source and can be used free of charge. For use in the corporate sector, however, we recommend the Conclusion of a maintenance contract. This ensures that you receive qualified support and that the module can be further developed to a high quality in the long term.
If you want to ensure that private keys are really secured by a Trusted Platform Module, the (much more complex) TPM Key Attestation be used.
2 thoughts on “Beantragen eines durch ein Trusted Platform Modul (TPM) geschütztes Zertifikat – ohne ein TPM zu besitzen”
Comments are closed.