To use the Online Certificate Status Protocol (OCSP), it is necessary to configure an appropriate certificate template.
The Online Responder (Online Certificate Status Protocol, OCSP) is an alternative way of providing revocation status information for certificates. Entities that want to check the revocation status of a certificate do not have to download the complete list of all revoked certificates thanks to OCSP, but can make a specific request for the certificate in question to the online responder. For a more detailed description, see the article "Basics Online Responder (Online Certificate Status Protocol, OCSP)„.
Certificate template configuration
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem and is available under a free license. It can downloaded via GitHub and can be used free of charge.
The Active Directory Certificate Services provide the Standard Certificate Template "OCSP Response Signing" with, which should be used as a starting point for a new certificate template.
Compatibility" tab
Support for OCSP was introduced with Windows Vista and Windows Server 2008. Since OCSP requires some special settings, the default certificate template for OCSP is basically a version 3 certificate template.
The compatibility settings can thus be adopted unchanged.
General" tab
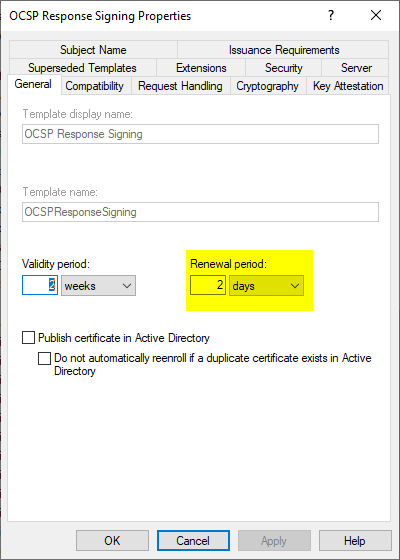
By default, two weeks are configured for the Validity Period and two days for the Renewal Period.
Since OCSP response signature certificates cannot be revoked, the shortest possible validity period makes a lot of sense.
The application and renewal of the OCSP password signature certificates is not performed by Autoenrollment, but by the online responder directly. This evaluates the certificate renewal setting and renews the certificate according to the settings.
In order to achieve the greatest possible resilience in the event of a failure of the certification authority, a similar logic should be applied as for revocation list overlapping, i.e. the aim should be to achieve the earliest possible renewal of the certificate. If this is not possible, the previous certificate can continue to be used for as long as possible in this way.
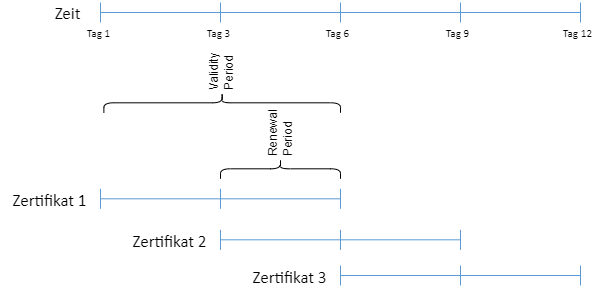
It should be noted here that, in contrast to Autoenrollment, not the rule applies that first 80% of the certificate validity must be exceeded. However, the certificate template configuration dialog does not allow renewal periods greater than 75% of certificate validity.
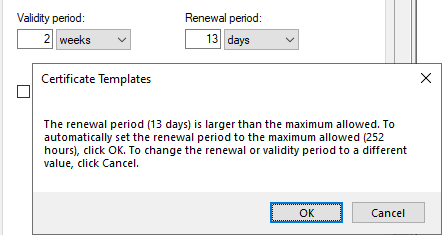
Accordingly, the ratios between certificate validity and renewal period should be planned.
Cryptography" index card
Since it is in the one Scheme Version 3 Certificate Template and the online responder only supports these, only Key Storage Provider be used.
The key size is configured to 2048 bits with RSA key by default. In the meantime it is advisable to increase this to 3072 bits. The The use of elliptical curves is technically possible, butHowever, this may cause compatibility problems.
It can be very useful, to protect the key material, to use a Hardware Security Module (HSM) to use. However, care must be taken here to ensure that no storage space restrictions (e.g. when using a SafeNet HSM) are present that could jeopardize availability at a later date.
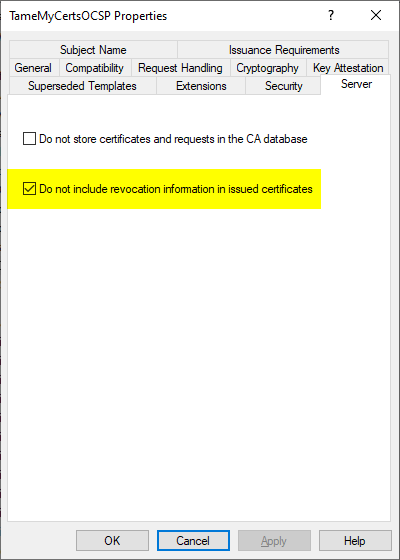
Server" tab
Since OCSP password signing certificates themselves must not contain revocation status information, the "Do not include revocation information in issued certificates" option must be enabled. This is already the case in the default setting.
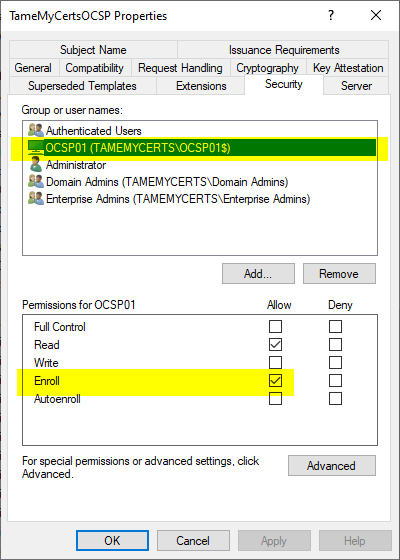
Security" tab
To apply for the certificates, the computer accounts of the online responder servers have to be configured with "Enroll" (Attention: not "Autoenroll") can be authorized. This can be done by explicitly entering the computer accounts or by a security group.
Related links:
- Basics of online responders (Online Certificate Status Protocol, OCSP)
- Overview of the setting options for blocking configurations of the online responder (OCSP).
- Basics: Cryptographic Service Provider (CSP) and Key Storage Provider (KSP)
- List of certificate use cases for which compatibility with elliptic curve (ECC)-based keys is known
- Planning of certificate validity and renewal period of end entity certificates with autoenrollment
- What key lengths should be used for certificate authorities and certificates?
One thought on “Konfigurieren einer Zertifikatvorlage für Onlineresponder (OCSP) Antwortsignatur-Zertifikate”
Comments are closed.