If a blocking configuration is configured for an online responder, there are various setting options that are discussed below.
The Online Responder (Online Certificate Status Protocol, OCSP) is an alternative way of providing revocation status information for certificates. Entities that want to check the revocation status of a certificate do not have to download the complete list of all revoked certificates thanks to OCSP, but can make a specific request for the certificate in question to the online responder. For a more detailed description, see the article "Basics Online Responder (Online Certificate Status Protocol, OCSP)„.
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
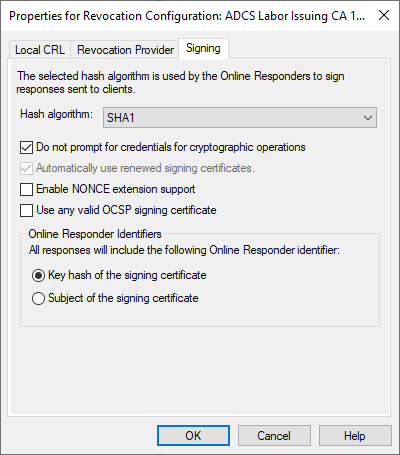
Hash Algorithm
Specifies which algorithm is used to sign the OCSP response.
Valid values are:
| Algorithm | Notes |
|---|---|
| MD2 | outdated, not recommended |
| MD4 | outdated, not recommended |
| MD5 | outdated, not recommended |
| SHA1 | obsolete, not recommended, default value |
| SHA256 | recommended default value according to RFC 6960 |
| SHA384 | |
| SHA512 |
Do not prompt for credentials for cryptographic operations
If the private key of the OCSP password signing certificate is additionally protected (e.g. by a password or a hardware security module that requires interaction when loading the key), the corresponding dialog would be presented when loading the private key (starting the online responder service or loading a revocation configuration for the first time).
If this option is enabled (default setting), no dialog is displayed, instead the revocation configuration would silently transition to an error state.
This option is mapped by the flag "OCSP_SF_SILENT" (0x1).
Automatically use renewed signing certificates
If this option is enabled (default for online configurations), the online responder automatically uses new OCSP password signing certificates. Thus, no manual assignment by an administrator is required.
This option is mapped by the flag "OCSP_SF_ALLOW_SIGNINGCERT_AUTORENEWAL" (0x4).
Enable NONCE extension support
If the option is enabled and an OCSP request contains the Number used only Once (NONCE) extension, the server-side cache is ignored and a new response is generated containing the requested NONCE.
Please note that NONCE is only used if an OCSP client uses it. The Microsoft OCSP client does not support the NONCE extension.
The Microsoft OCSP client does not support the nonce extension.
Online Responder Installation, Configuration, and Troubleshooting Guide (Microsoft)
This option is mapped by the flag "OCSP_SF_ALLOW_NONCE_EXTENSION" (0x100).
Use any valid OCSP signing Certificate
If the option is not enabled (default setting), only OCSP answer signing certificates issued by the same certificate authority are used.
If this option is enabled, the online responder can use all signature certificates that include "OCSP signing" extended key usage, regardless of which certificate authority issued them.
This option is mapped by the flag "OCSP_SF_FORCE_SIGNINGCERT_ISSUER_ISCA" (0x8).
Online Responder Identifiers
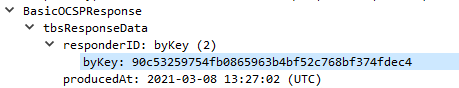
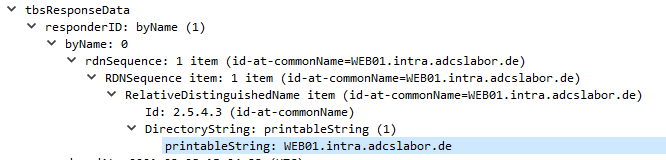
Specifies whether the ResponderID of the OCSP response contains the subject name or the key hash (SHA1 private key checksum, default) of the OCSP response signing certificate (see RFC 6960).
The setting is represented by the following two flags:
| Type | Flag |
|---|---|
| Key hash | OCSP_SF_RESPONDER_ID_KEYHASH (0x40) |
| Subject Name | OCSP_SF_RESPONDER_ID_NAME (0x80) |
Related links:
External sources
- Online Responder Installation, Configuration, and Troubleshooting Guide (Microsoft)
- IOCSPCAConfiguration::get_SigningFlags method (certadm.h) (Microsoft)
- Installing, Configuring, and Troubleshooting the Online Responder (Microsoft's OCSP Responder) (Microsoft, archive link)
- RFC 6960 - X.509 Internet Public Key Infrastructure / Online Certificate Status Protocol - OCSP (Internet Engineering Task Force)
2 thoughts on “Übersicht über die Einstellungsmöglichkeiten für Sperrkonfigurationen des Onlineresponders (OCSP)”
Comments are closed.