In the default configuration, all certification authority certificates of Active Directory integrated certification authorities (Enterprise Certification Authority) are located in an object of type CertificationAuthority named NTAuthCertificates within the Configuration Partition of the Active Directory forest.
For an overall structure named intra.adcslabor.de, the object is located in the following LDAP path:
CN=NTAuthCertificates,CN=Public Key Services,CN=Services,CN=Configuration,DC=intra,DC=adcslabor,DC=de
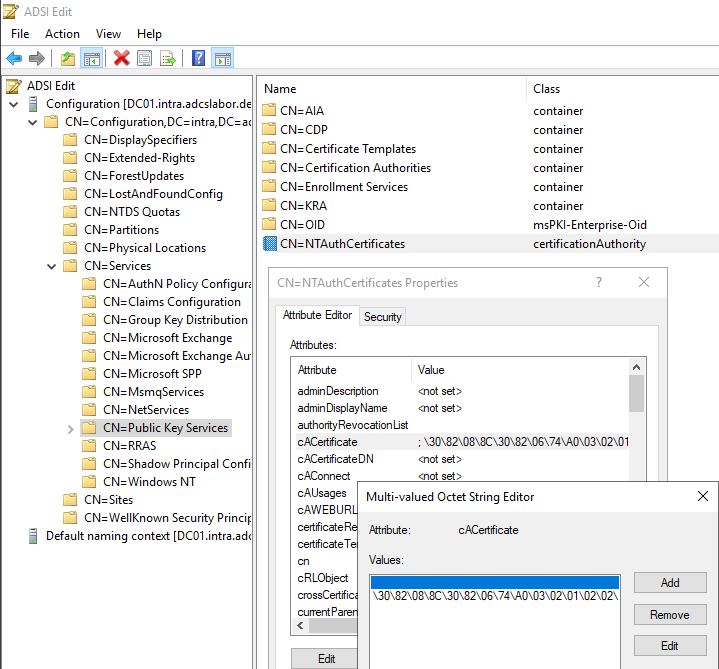
The certification authority certificates are automatically entered into the object during the installation of certification authorities integrated into Active Directory (Enterprise Certification Authority).
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
The NTAuthCertificates object is used in the Windows ecosystem to authorize certificate authorities for certificate-based logins. This includes, among others:
| Function | Description |
|---|---|
| Enroll on Behalf Of (EOBO) | The CA certificate of the certification authority that issues the certificates for the enrollment agents must be located in NTAuthCertificates. |
| Key Recovery / Private Key Archiving | The CA certificate of the certification authority that archives the keys must be located in NTAuthCertificates. |
| Smartcard Logon | The CA certificate of the certification authority that issues the certificates of the domain controllers and logon users must be located in NTAuthCertificates. |
| Windows Hello for Business | Identical to Smartcard Logon. If Windows Hello for Business is used without certificates, only the certification authority for domain controllers must be entered. |
| Network Policy Server (Network Policy Server, NPS) when certificate-based logins are processed (e.g. 802.1x over wireless or wired network, DirectAccess, Always ON VPN). | The CA certificate of the certification authority that issues the certificates of the logging in users or computers must be located in NTAuthCertificates. |
| EFS File Recovery Agents | The CA certificate of the certification authority that issues the certificates of the file recovery agents must be located in NTAuthCertificates. |
| IIS Client Certificate Mapping (against Active Directory) | The CA certificate of the certification authority that issues the certificates of the logging in users must be located in NTAuthCertificates. |
| Network Device Enrollment Service (Network Device Enrollment Service, NDES), Renewal mode only | Only affects renewal mode, i.e. signing a certificate request with an existing certificate. The CA certificate of the certification authority that issued the certificates of the certificates to be renewed must be located in NTAuthCertificates. |
See also article "Changes to Certificate Issuance and Certificate-Based Logon to Active Directory with the May 10, 2022 Patch for Windows Server (KB5014754)„.
Certificate authorities that do not serve such logon forms can be safely removed from the object. Since the CA certificates are stored as an ASN.1 encoded byte array, and one cannot see the contents of the certificates, the ADSI editor is less suitable for this.
Instead, the Enterprise PKI tool (pkiview.msc) should be downloaded from the Remote Server Administration Tools (RSAT) for the Certification Authority can be used. In this program there is an option "Manage AD Containers".
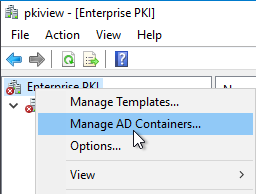
Enterprise Administrator or appropriately delegated permissions are required for this step.
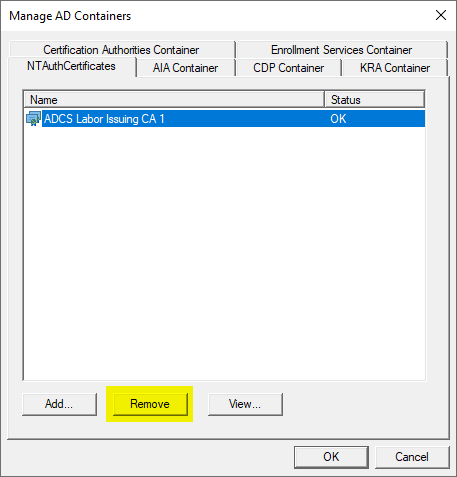
In the tab NTAuthCertificates all CA certificates that are not needed can be removed.
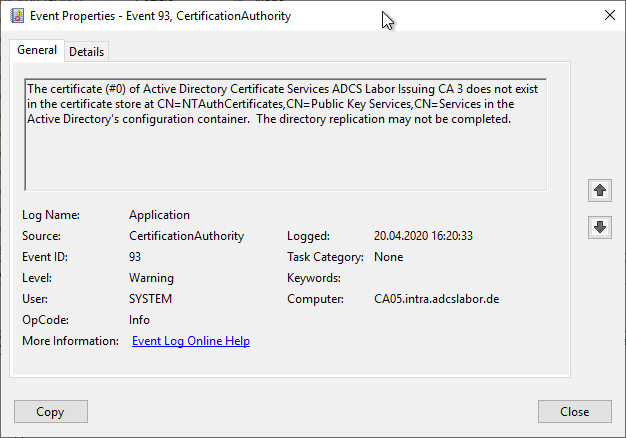
Please note that Certification Authorities, in the absence of one of their certification authority certificates, will not issue the Event no. 93 in the event log, which of course can be deliberately ignored in this case.
Related links:
- Requesting a certificate fails with the error message "A certification chain processed correctly, but one of the CA certificates is not trusted by the policy provider. 0x800b0112 (-2146762478 CERT_E_UNTRUSTEDCA)".
- Attack vector on Active Directory directory service via smartcard logon mechanism
- Installing Remote Server Administration Tools for Active Directory Certificate Services on Windows 10 version 1809 and later
- What requirements must be met on the infrastructure side for smartcard logins to be possible?
- Logon error with Windows Hello for Business: "Contact the system administrator and tell them that the KDC certificate could not be verified."
External sources
- Map Client Certificates by Using Active Directory Mapping (IIS 7) (Microsoft Corporation)
- Client Certificate Mapping Authentication (Microsoft Corporation)
- How to import third-party certification authority (CA) certificates into the Enterprise NTAuth store (Microsoft Corporation)
22 thoughts on “Bearbeiten des NTAuthCertificates Objektes im Active Directory”
Comments are closed.