When configuring a certificate template for the Registration Authority (RA) certificates for the Network Device Enrollment Service (NDES), the question arises, especially when using Hardware Security Modules (HSM), which Cryptographic Service Provider (CSP) of the HSM manufacturer should be used.

The Network Device Enrollment Service (NDES) provides a way for devices that do not have an identifier in Active Directory (for example, network devices such as routers, switches, printers, thin clients, or smartphones and tablets) to request certificates from a certification authority. For a more detailed description, see the article "Network Device Enrollment Service (NDES) Basics„.
A Cryptograpic Service Provider (CSP) is a key storage and usage abstraction for applications that use certificates. CSPs were replaced by key storage providers with Windows Server 2008 and Windows Vista. More information can be found in the article "Basics: Cryptographic Service Provider (CSP) and Key Storage Provider (KSP)„.
To answer this question, it is helpful to first check which CSP is used in an installation without HSM in the default setting.
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
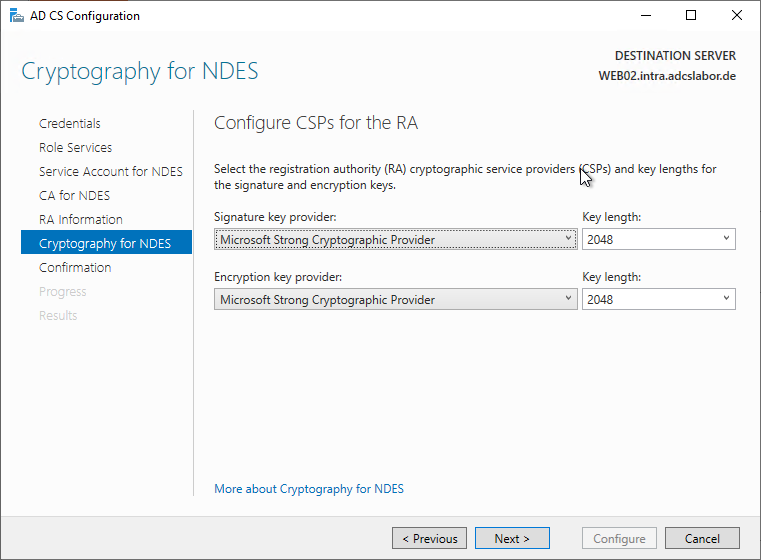
As can be seen, in both cases this is the "Microsoft Strong Cryptographic Provider". Details about this and other CSPs can be viewed with the following command line command:
certutil -csplist
If you configure your own certificate templates for the Registration Authority certificates, the "Microsoft RSA SChannel Cryptographic Provider" is selected for the CEP Encryption certificate template.
The provider type for the "Microsoft Strong Cryptographic Provider" is PROV_RSA_FULL.
If you look at the Microsoft documentation for the provider types, you will find the following description.
| Provider type | Description (Microsoft) |
|---|---|
| PROV_RSA_FULL | Supports both digital signatures and data encryption. It is considered a general purpose CSP. The RSA public key algorithm is used for all public key operations. |
| PROV_RSA_AES | Supports the same as PROV_RSA_FULL with additional AES encryption capability. |
| PROV_RSA_CHANNEL | Supports both RSA and Schannel protocols. |
For the selection of the correct CSP of the HSM one looks now at the provider types of the respective HSM manufacturer.
Example Gemalto (SafeNet) Luna:
Provider Name: Luna Cryptographic Services for Microsoft Windows
Provider Type: 1 - PROV_RSA_FULL
Provider Name: Luna enhanced RSA and AES provider for Microsoft Windows
Provider Type: 24 - PROV_RSA_AES
Provider Name: Luna SChannel Cryptographic Services for Microsoft Windows
Provider Type: 12 - PROV_RSA_SCHANNEL
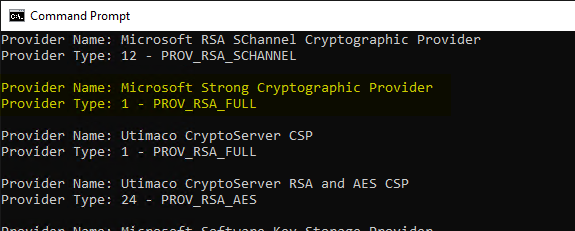
Example Utimaco CryptoServer:
Provider Name: Utimaco CryptoServer CSP
Provider Type: 1 - PROV_RSA_FULL
Provider Name: Utimaco CryptoServer RSA and AES CSP
Provider Type: 24 - PROV_RSA_AES
The documentation on provider types indicates that the PROV_RSA_AES and the PROV_RSA_SCHANNEL both have at least the same functionality as the PROV_RSA_FULL.
Conclusion
At least one CSP of type PROV_RSA_FULL should be selected for the Registration Authority (RA) certificates of the network device registration service.
For the common hardware security modules these would be:
- Gemalto (SafeNet): Luna Cryptographic Services for Microsoft Windows
- Utimaco (CryptoServer): Utimaco CryptoServer CSP
- Thales (nCipher): nCipher Enhanced Cryptographic Provider
The use of Key Storage Providers (KSP) is not possible with the Network Devices Registration Service. See also article "List of use cases for certificates that require specific Cryptographic Service Providers (CSP) or Key Storage Providers (KSP).„.
Further safety hardening
A poorly secured NDES installation can a significant risk for the company salvage.
Hardening of Registration Authority certificates is useful only in this case, if its signatures are also required by the device certificate template.
The use of a Hardware Security Module (HSM) is not the only or the most effective means of hardening the security of an NDES installation.
Besides the Using HTTPS for the NDES administration website it is highly recommended to select the associated Certification Authority from the NTAuthCertificates Remove object in Active Directory and either Name restrictions (English "Name Constraints"), or to limit the scope of the Certificate Enrollment by the TameMyCerts Policy Module to narrow down.
Related links:
External sources
- Cryptographic Provider Type (Microsoft)
- PROV_RSA_FULL (Microsoft)
One thought on “Welcher Cryptographic Service Provider (CSP) sollte für den Registrierungsdienst für Netzwerkgeräte (NDES) verwendet werden?”
Comments are closed.