Assume the following scenario:
- A certification authority is implemented in the network.
- The certification authority service does not start.
- When trying to start the Certification Authority service, you get the following error message:
The revocation function was unable to check revocation because the revocation server was offline. 0x80092013 (-2146885613 CRYPT_E_REVOCATION_OFFLINE)
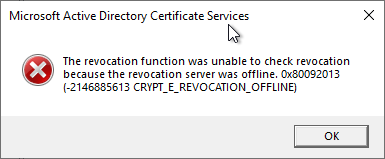
A corresponding error message can also be found in the event display (Event no. 100) of the Certification Authority:
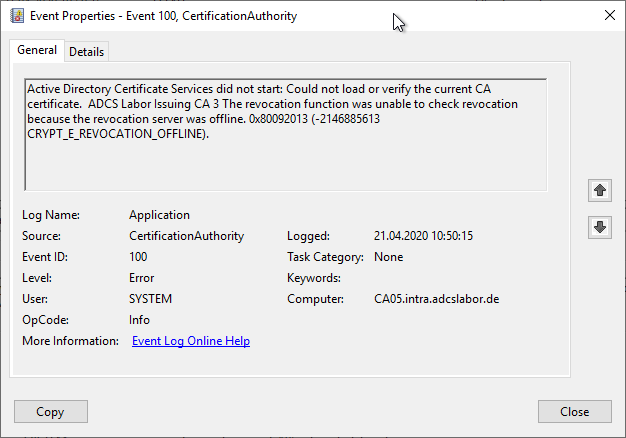
Active Directory Certificate Services did not start: Could not load or verify the current CA certificate. ADCS Labor Issuing CA 3 The revocation function was unable to check revocation because the revocation server was offline. 0x80092013 (-2146885613 CRYPT_E_REVOCATION_OFFLINE).
Cause
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
In this case, the subordinate issuing certification authority was unable to check the revocation status of its currently used certification authority certificate.
This error occurs only with the currently used certificate authority certificate. The certification authority always uses the last of the installed certificates for issuing certificates. This error should not occur with the previous certification authority certificates.
The cause can usually be identified by the management console for the corporate PKI (pkiview.msc) can be determined.
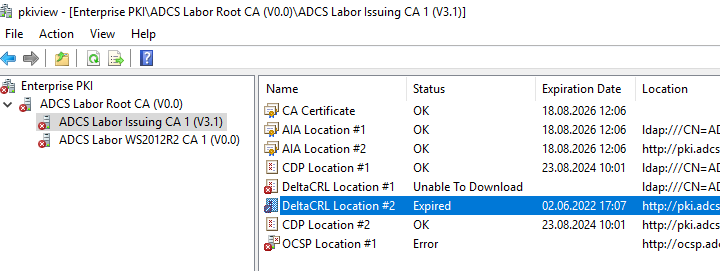
In such a case, the revocation list of the higher-level certification authority is usually not available (offline, blocked by firewall), or it has expired (in both cases, the error code CRYPT_E_REVOCATION_OFFLINE generated).
Solution: Issue and publish the revocation list of the higher-level certification authority
As a rule, the problem can be solved by Issue and publication of a new certificate revocation list on the higher-level certification authority.
It should also be ensured that the blacklist can actually be retrieved, i.e. name resolution and Firewall rules be controlled.
Workaround: Disable revocation list check for the certification authority
It is not possible in all cases to restore the availability of the revocation status information in time, for example, because one depends on an external entity.
As Temporary solution the revocation list check for the certification authority can be deactivated in such cases. To do this, the flag CRLF_REVCHECK_IGNORE_OFFLINE on the certification authority.
The preferred solution should always be to eliminate the cause of the failed revocation information retrieval.
First, the following command line command should be used to view the current configuration:
certutil -getreg CA\CRLFlags
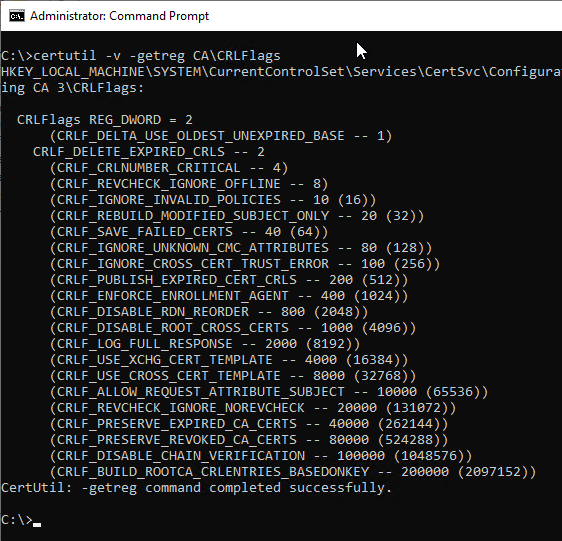
In the example above, the CRLF_REVCHECK_IGNORE_OFFLINE flag is indented and set in brackets, which means that it is not active. It can be set with the following command line command:
certutil -setreg CA\CRLFlags +CRLF_REVCHECK_IGNORE_OFFLINE
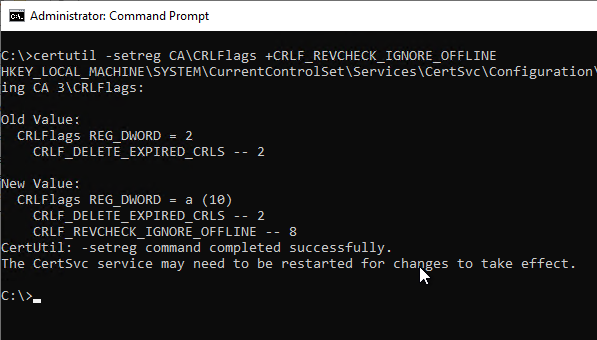
Afterwards, the certification authority service must be restarted.
The flag can be removed again with the following command:
certutil -setreg CA\CRLFlags -CRLF_REVCHECK_IGNORE_OFFLINE
Is there a solution for the case that the certificate authority certificate does not contain any revocation information?
In this case, too, the preferred option is to clarify why the certification authority certificate does not contain any revocation information and to resolve the underlying cause.
Under certain circumstances, you may receive a certificate from the higher-level certification authority that has no revocation information - i.e. no reference to a certificate revocation list/CRL or a Online responder (OCSP) disposes
In this case, the flag CRLF_REVCHECK_IGNORE_NOREVCHECK can be activated in the same way.
Related links:
- The certification authority service does not start and throws the error message "A certificate chain processed, but terminated in a root certificate which is not trusted by the trust provider. 0x800b0109 (-2146762487 CERT_E_UNTRUSTEDROOT)"
- The certificate authority service does not start and throws the error message "A certificate chain could not be built to a trusted root authority. 0x800b010a (-2146762486 CERT_E_CHAINING)".
- The certificate authority service does not start and throws the error message "The certificate is revoked. 0x80092010 (-2146885616 CRYPT_E_REVOKED)".
- What impact does a non-functioning revocation list of a certification authority certificate have on the certification authority?
- What impact does the revocation of a certification authority certificate have on the certification authority?
- What impact does the revocation of the trust status of a root certification authority certificate have on the certification authority
External sources
- Ignore Revocation Checking - The bane of my existence! (PKI Solutions, Inc.)
10 thoughts on “Der Zertifizierungsstellen-Dienst startet nicht und wirft die Fehlermeldung „The revocation function was unable to check revocation because the revocation server was offline. 0x80092013 (-2146885613 CRYPT_E_REVOCATION_OFFLINE)“”
Comments are closed.