The following describes the impact on certification authority operations if one of the root certification authority certificates from which one of the certification authority certificates is derived has its trust status revoked, or never had it.
This case may also occur as planned, for example, when a previous certification authority hierarchy is to be decommissioned.
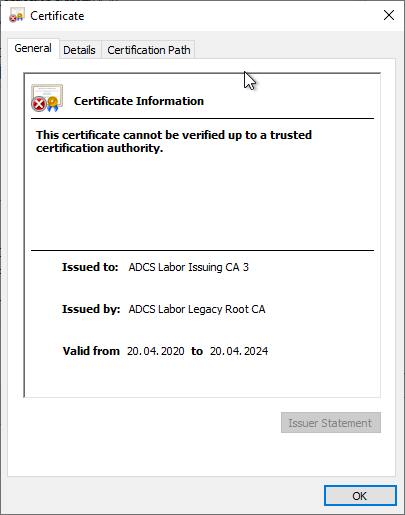
If the LDAP AIA paths are still reachable, the certification authority itself restores the trust status. The certification authority will use the Event no. 103 log:
Active Directory Certificate Services added the root certificate of certificate chain 0 to the downloaded Trusted Root Certification Authorities Enterprise store on the CA computer. This store will be updated from the Certification Authorities container in Active Directory the next time Group Policy is applied. To verify that the CA certificate is published correctly in Active Directory, run the following command: certutil -viewstore "ldap:///CN=ADCS Labor Issuing CA 3,CN=Certification Authorities,CN=Public Key Services,CN=Services,CN=Configuration,DC=intra,DC=adcslabor,DC=en?cACertificate?base?objectClass=certificationAuthority" (you must include the quotation marks when you run this command). If the root CA certificate is not present, use the Certificates console on the root CA computer to export the certificate to a file, and then run the following command to publish it to Active Directory: Certutil -dspublish rtificatefilename% Root.
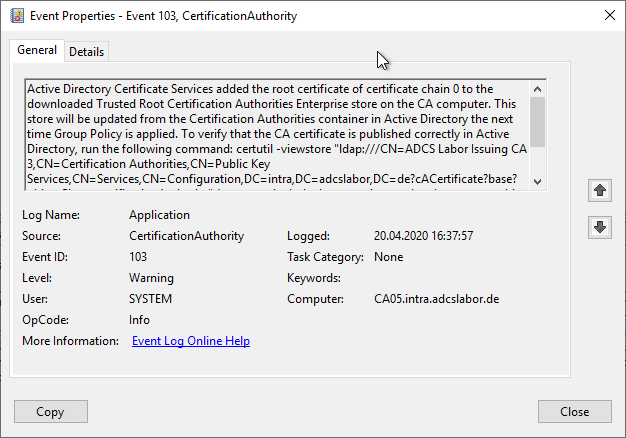
If the certification authority cannot independently restore the trust status, a distinction must be made as to which of the certification authority certificates is affected.
Case 1: The current certification authority certificate is affected
The certification authority always uses the latest, i.e. most recently installed, certification authority certificate to issue its certificates. If this certificate is affected, the certification authority refuses to start the service, but this can be circumvented under certain circumstances. More information can be found in the article "The certification authority service does not start and throws the error message "A certificate chain could not be built to a trusted root authority. 0x800b010a (-2146762486 CERT_E_CHAINING)"„.
The Certification Authority will use the Event no. 100 log:
Active Directory Certificate Services did not start: Could not load or verify the current CA certificate. ADCS Labor Issuing CA 3 A certificate chain could not be built to a trusted root authority. 0x800b010a (-2146762486 CERT_E_CHAINING).
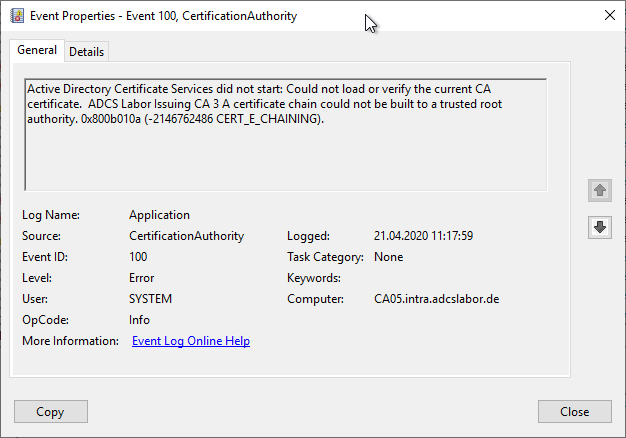
Case 2: A previous certification authority certificate is affected
If one of the previous certification authority certificates is affected, the certification authority service starts normally. Restoring archived keys of certificates issued by the no longer trusted certification authority certificate is also possible without any problems.
The Certification Authority will use the Event no. 42 log:
Could not build a certificate chain for CA certificate 2 for ADCS Labor Issuing CA 3. A certificate chain could not be built to a trusted root authority. 0x800b010a (-2146762486 CERT_E_CHAINING).
Related links:
- The certification authority service does not start and throws the error message "A certificate chain processed, but terminated in a root certificate which is not trusted by the trust provider. 0x800b0109 (-2146762487 CERT_E_UNTRUSTEDROOT)"
- The certificate authority service does not start and throws the error message "A certificate chain could not be built to a trusted root authority. 0x800b010a (-2146762486 CERT_E_CHAINING)".
- The certificate authority service does not start and throws the error message "The certificate is revoked. 0x80092010 (-2146885616 CRYPT_E_REVOKED)".
- The certificate authority service does not start and throws the error message "0x80092013 (-2146885613 CRYPT_E_REVOCATION_OFFLINE)".
- What impact does a non-functioning revocation list of a certification authority certificate have on the certification authority?
- What impact does the revocation of a certification authority certificate have on the certification authority?
3 thoughts on “Welchen Einfluss hat der Entzug des Vertrauensstatus eines Stammzertifizierungsstellen-Zertifikats auf die Zertifizierungsstelle?”
Comments are closed.