After installing a Network Device Enrollment Service (NDES), or after more extensive maintenance, an extensive functional test should be performed to ensure that all components are operating as desired.
The Network Device Enrollment Service (NDES) provides a way for devices that do not have an identifier in Active Directory (for example, network devices such as routers, switches, printers, thin clients, or smartphones and tablets) to request certificates from a certification authority. For a more detailed description, see the article "Network Device Enrollment Service (NDES) Basics„.
Carrying out the function test
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
A functional test of the Network Device Enrollment Service (NDES) includes the following steps:
- Ensure start of registration service for network devices service
- Checking the event display of the network device registration service.
- Calling the application page of the registration service for network devices
- Calling the administration page of the network device registration service.
- Apply for a certificate via NDES.
Details: Ensure the start of the registration service for network devices service.
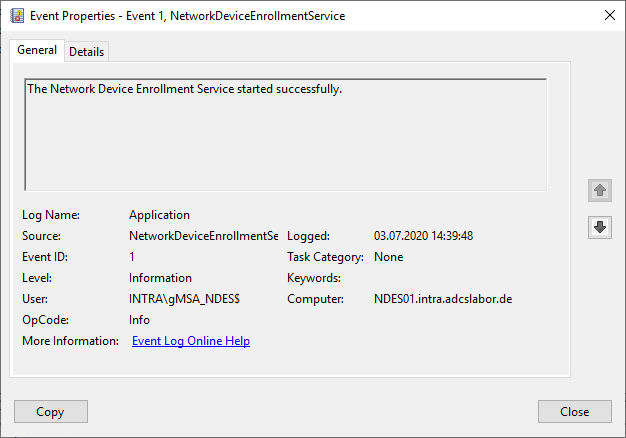
Since the network device registration service is implemented as a module within the Internet Information Server (IIS) service, it is not possible to control the service startup via the services administration account (services.msc). Instead, a corresponding Event me No. 1 logged in the event display.
However, this is only generated the first time it is called by a requester, so the "Calling the Network Device Registration Service Request Page" step described below must be performed first for this purpose. Alternatively, the call can also be performed with the following Windows PowerShell command:
[void](Invoke-WebRequest -Uri "http://localhost/certsrv/mscep/mscep.dll/pkiclient.exe?operation=GetCACaps")
Details: Checking the event display of the registration service for network devices
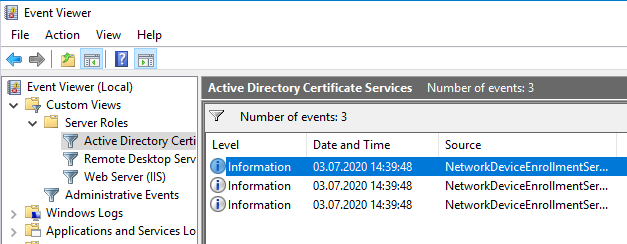
First, the Windows Event Viewer on the Network Device Server Registry Service should be scanned for any relevant events that might indicate an error. For this purpose, there is a predefined view in the Event Viewer under "Custom Views" - "Server Roles" - "Active Directory Certificate Services", which has already defined the required filters on the Event Viewer.
See also article "Overview of Windows events generated by the Network Device Enrollment Service (NDES).„.
If you encounter problems with this step, the following articles may be helpful:
- Enabling Debug Logging for the Network Device Enrollment Service (NDES)
- The Network Device Enrollment Service (NDES) logs the error message "The Network Device Enrollment Service cannot be started (0x80070002). The system cannot find the file specified."
- The Network Device Enrollment Service (NDES) logs the error message "The Network Device Enrollment Service cannot retrieve one of its required certificates (0x80070057). The parameter is incorrect."
- The Network Device Enrollment Service (NDES) logs the error message "The Network Device Enrollment Service cannot create or modify the registry key Software\Microsoft\Cryptography\MSCEP\EncryptedPassword."
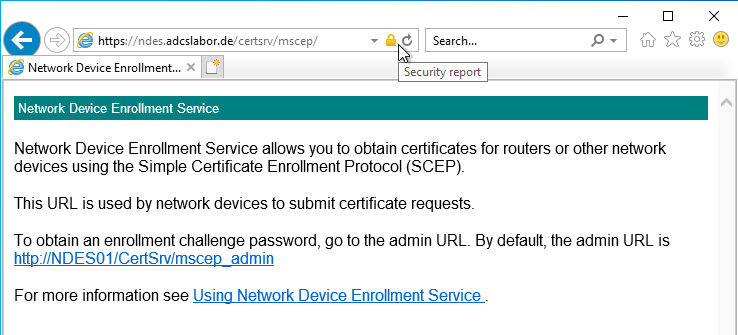
Details: Calling the application page of the network device registration service.
By calling up the request page (mscep), it is possible to check whether the service generally starts and is ready for use. The call is made via the following address:
https://{servername-or-alias}/certsrv/mscep
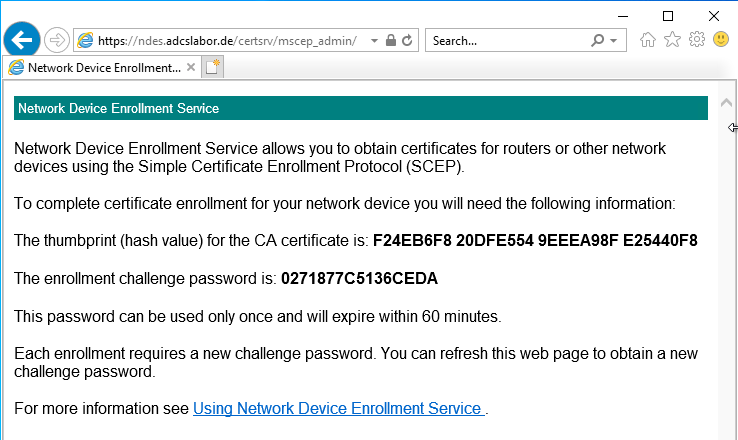
Details: Calling the administration page of the network device registration service.
By calling up the administration page (mscep), it is possible to check whether the user's logon works and the user receives a one-time password. To log in, an account must be used that has "Enroll" permissions on the configured certificate template. The call is made via the following address:
https://{servername-or-alias}/certsrv/mscep_admin
If you encounter problems with this step, the following articles may be helpful:
- When accessing the Network Device Enrollment Service (NDES) administration web page (certsrv/mscep_admin), you are always prompted to log in.
- The Network Device Enrollment Service (NDES) administration web page (certsrv/mscep_admin) reports "You do not have sufficient permission to enroll with SCEP. Please contact your system administrator."
- The Network Device Enrollment Service (NDES) Administration web page (certsrv/mscep_admin) reports "The password cache is full."
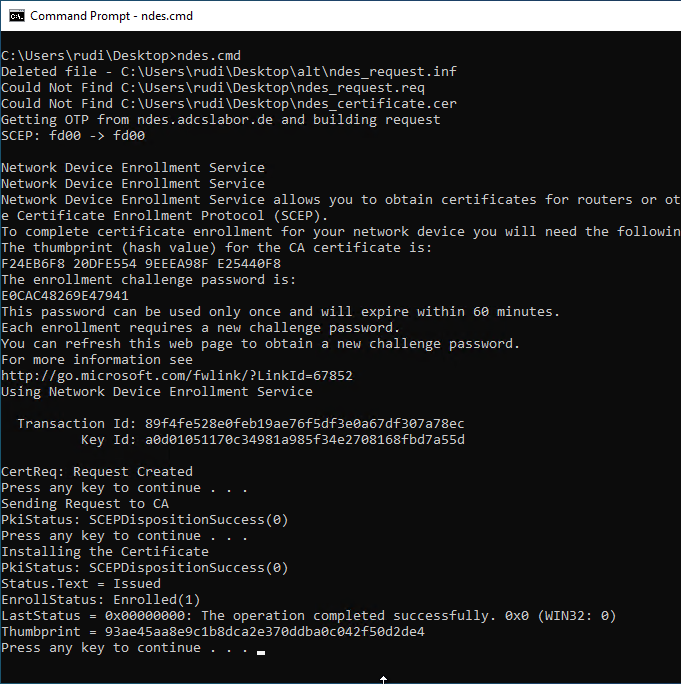
Details: Apply for a certificate via NDES
Requesting certificates via the registration service is associated with the PSCertificateEnrollment PowerShell module is also possible via Windows PowerShell. See article "Certificate Enrollment for Windows Systems via the Network Device Enrollment Service (NDES) with Windows PowerShell„.
Windows 10 includes a client for requesting certificates via the SCEP protocol, but only at the command line level. The following script can be used to request a certificate via NDES:
Requesting via the command line does not support Secure Sockets Layer (SSL). Accordingly, the NDES server must be configured to accept connections via HTTP. The credentials can be read over the network, since the connection is not Not encrypted is.
On GitHub there is a PowerShell and C# code for requesting a certificate via NDES, which also supports SSL: Sleepw4lker / NDESTest
@echo off set SERVER= :: enter server name or alias here set DOMAIN= :: enter domain name here set USER= :: enter username here set PASSWORD= :: enter password here set INFFILE=ndes_request.inf set REQFILE=ndes_request.req set CRTFILE=ndes_certificate.cer set SUBJECT=TestNDESCert set MACHINEKEYSET=false set KEYLENGTH=2048 del /s /q %INFFILE% del /s /q %REQFILE% del /s /q %CRTFILE% echo [NewRequest] > %INFFILE% echo Subject = "CN=%SUBJECT%" >> %INFFILE% echo RequestType = SCEP >> %INFFILE% echo KeyLength = %KEYLENGTH% >> %INFFILE% echo MachineKeySet = %MACHINEKEYSET% >> %INFFILE% echo Getting OTP from %SERVER% and building request certreq -v -config %SERVER% -username %DOMAIN%\%USER% -p %PASSWORD% -new %INFFILE% %REQFILE% pause echo Sending Request to CA certreq -v -config %SERVER% -submit %REQFILE% %CRTFILE% pause echo Installing the Certificate certreq -accept %CRTFILE% pause
The script will perform the necessary steps:
- Authenticate to the NDES administration page (mscep_admin) and retrieve a one-time password (OTP).
- Create a key pair and a certificate request.
- Sending the certificate request to the certification authority via NDES, using the previously requested OTP.
- Collect and install the issued certificate.
Related links:
- Configuring the Network Device Enrollment Service (NDES) for use with an alias.
- Installing the Network Device Enrollment Service (NDES) without Enterprise Administrator permissions
External sources
- Sleepw4lker / NDESTest (GitHub)
3 thoughts on “Funktionstest durchführen für den Registrierungsdienst für Netzwerkgeräte (NDES)”
Comments are closed.