The Network Device Enrollment Service (NDES) has the ability to authenticate with a previously issued certificate in order to reapply for a certificate with the same content. This is very convenient for renewal operations, as it eliminates the need to apply for a one-time password beforehand.
The Network Device Enrollment Service (NDES) provides a way for devices that do not have an identifier in Active Directory (for example, network devices such as routers, switches, printers, thin clients, or smartphones and tablets) to request certificates from a certification authority. For a more detailed description, see the article "Network Device Enrollment Service (NDES) Basics„.
Requesting and renewing certificates via NDES is also possible with the Windows PowerShell module PSCertificateEnrollment possible. See article "Authentication at the Network Device Enrollment Service (NDES) with an existing certificate (renewal mode)„.
Authentication with an existing certificate is described in the RFC for NDES.
If the client already has a certificate issued by the SCEP CA, and the CA supports renewal (see Section 2.5), that certificate SHOULD be used.
RFC 8894
Accordingly, the function is also implemented in the Microsoft implementation, the Network Device Enrollment Service (NDES).
The NDES supports certificate renewal where a device uses a previously issued certificate to validate the new certificate request.
Active Directory Certificate Services (AD CS): Network Device Enrollment Service (NDES) (Microsoft)
The renewal mode is already activated in the standard configuration of the NDES. If you want to be on the safe side, you can check the activated functions by calling the following address on the NDES server.
http://{server-name-or-alias}/certsrv/mscep/mscep.dll/pkiclient.exe?operation=GetCACaps
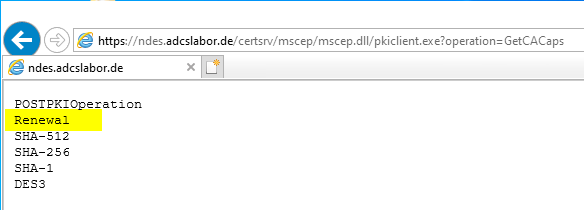
Renewal with on-board resources
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
To authenticate with an existing certificate, the SHA1 fingerprint of an existing certificate must be entered as the value "RenewalCert" in the request configuration file.
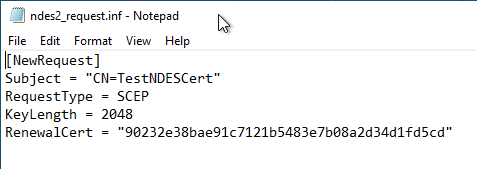
The certificate used must have the same identity and have been issued by the same certification authority as the new certificate request. A special Extended Key Usage as with the Key-based Renewal of the Certificate Enrollment Web Services (CEP, CES) is not required.
The SHA1 fingerprint can be found in the "Details" tab of a certificate's properties dialog.
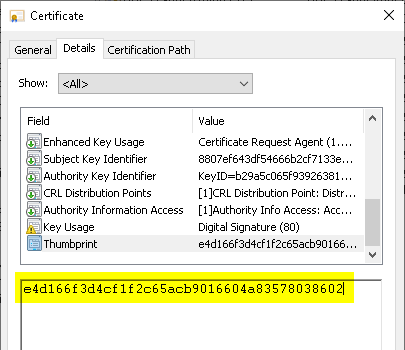
Then the certificate request can be generated with the following command line command:
certreq -config {server name or alias} -new {INF file} {CSR file}
You are presented with a selection dialog in which you can find the certificate previously identified by the fingerprint.
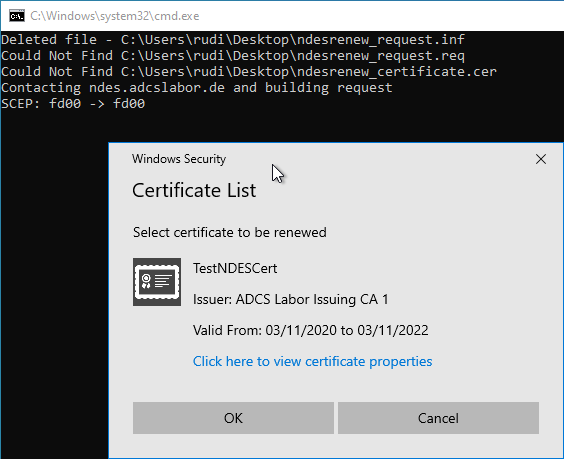
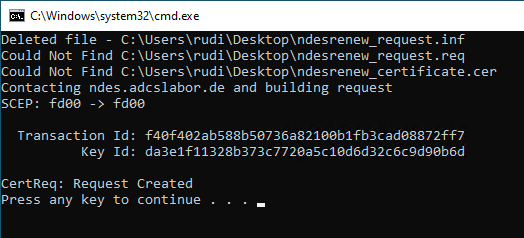
The following command line command can be used to send the request to the NDES server.
certreq -v -config {server name or alias} -submit {CSR file} {certificate file}
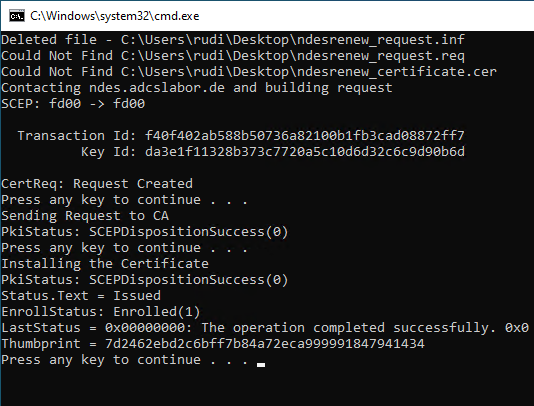
The issued certificate can then be installed on the system using the following command line command.
certreq -accept {certificate file}
The following script can also be used for the application:
@echo off set SERVER= :: enter server name or alias here set THUMBPRINT= :: enter here SHA1 fingerprint of the old certificate set INFFILE=ndesrenew_request.inf set REQFILE=ndesrenew_request.req set CRTFILE=ndesrenew_certificate.cer set SUBJECT=TestNDESCert set MACHINEKEYSET=false set KEYLENGTH=2048 del /s /q %INFFILE% del /s /q %REQFILE% del /s /q %CRTFILE% echo [NewRequest] > %INFFILE% echo Subject = "CN=%SUBJECT%" >> %INFFILE% echo RequestType = SCEP >> %INFFILE% echo KeyLength = %KEYLENGTH% >> %INFFILE% echo MachineKeySet = %MACHINEKEYSET% >> %INFFILE% echo RenewalCert = "%THUMBPRINT%" >> %INFFILE% echo Contacting %SERVER% and building request certreq -v -config %SERVER% -new %INFFILE% %REQFILE% pause echo Sending Request to CA certreq -v -config %SERVER% -submit %REQFILE% %CRTFILE% pause echo Installing the Certificate certreq -accept %CRTFILE% pause
Renew with Windows PowerShell
The renewal can also be done with the PSCertificateEnrollment PowerShell module. For this see article "Certificate Enrollment for Windows Systems via the Network Device Enrollment Service (NDES) with Windows PowerShell„.
Related links
External sources
- Active Directory Certificate Services (AD CS): Network Device Enrollment Service (NDES) | Certificate Renewal (Microsoft)
- certreq | Microsoft Docs (Microsoft)
- RFC 8894 - Simple Certificate Enrolment Protocol (Internet Engineering Task Force)
- draft-nourse-scep-23 - Simple Certificate Enrollment Protocol (Internet Engineering Task Force)
3 thoughts on “Authentifizierung am Registrierungsdienst für Netzwerkgeräte (NDES) mit einem existierenden Zertifikat (Renewal-Modus)”
Comments are closed.