By default, the Microsoft Certification Authority removes the serial numbers of expired certificates from the revocation lists it issues.
However, there are some exceptions to this.
Extended key usages for certificates that remain in the revocation list even after expiration
The configuration of the certification authority can be viewed with the following command:
certutil -v -getreg CA\EKUOIDsForPublishExpiredCertInCRL
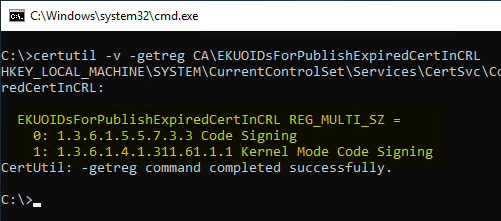
In the default settings the following Extended Key Usages are listed here:
| OID | Description |
|---|---|
| 1.3.6.1.5.5.7.3.3 | Code Signing |
| 1.3.6.1.4.1.311.61.1.1 | Kernel Mode Code Signing |
In the case of code signing certificates, revocation information can remain relevant even after the certificate has expired.
The reason for this is that code signatures have a time stamp (Time Stamp, RFC 3161), which confirms the time of a signature. Signed code is still recognized as valid beyond the validity period of the signature certificate, which is why any revocation information must also be available after the certificate expires in order to be able to determine the status of a signature.
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
Extend list
It only makes sense to include other certificate types if a time stamp is also used for their signatures. An example of this would be the document signature.
If it is required that further Extended Key Usages are handled accordingly, they can be added to the list.
certutil -setreg CA\EKUOIDsForPublishExpiredCertInCRL +{OID}
The certification authority service must then be restarted for the changes to take effect.
The Certification Authority will, if an invalid OID is entered, delete the Event no. 131 log and use the default settings.
For a list of commonly used extended key usages, see the article "Frequently Used Extended Key Usages and Issuance Policies„.
Always include expired certificates in the revocation list
The certification authority may also be instructed to continue to enter expired certificates in the revocation lists issued as a matter of principle.
However, this will have a negative impact on the blacklist size and is only recommended if there is an important reason to do so (e.g. a compliance requirement).
A rule of thumb for blacklist size: 100,000 blacklists equals approximately 5 Mbytes of blacklist size.
A significant factor influencing the size of a blacklist is also the Length of serial numbers of certificates.
Permanent storage of revoked certificates within issued revocation lists can be configured on the certification authority with the following command:
certutil -setreg CA\CRLFlags +CRLF_PUBLISH_EXPIRED_CERT_CRLS
The certification authority service must then be restarted for the changes to take effect.
Related links:
- Basics: Checking the revocation status of certificates
- How is the serial number of a certificate formed?
2 thoughts on “Behandlung abgelaufener Zertifikate bei der Ausstellung von Zertifikatsperrlisten”
Comments are closed.