The need for the use for cryptography can be summarized under the notion of ensuring secure communication in the presence of untrusted third parties. The goals of cryptography are:
- To prevent data from falling into unauthorized hands (To ensure the confidentiality of data).
- Find out if data has been modified during transport (Ensure the integrity of the data).
- To clearly identify the source of the data (To ensure the authenticity of the data).
- Additionally, users or computers can authenticate themselves using cryptography.
As early as ancient Egypt, the use of hieroglyphs ensured that messages could only be understood by a privileged few. The ancient Romans also resorted to a cryptographic process, known today as "Caesar encryption," to protect secret military messages from unauthorized access. During the Second World War, the "Enigma" cipher machine achieved dubious fame before it was defeated by the Allied forces.
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
Basics of modern cryptography
In modern cryptography, two methods are used to achieve the previously mentioned goals: Encryption and signing. Both are presented below.
Digital encryption
Digital encryption ensures the confidentiality of data. Here, a plaintext in combination with a mathematical key is entered into a cryptographic function to generate a ciphertext. Digital encryption uses two methods: symmetric and asymmetric.
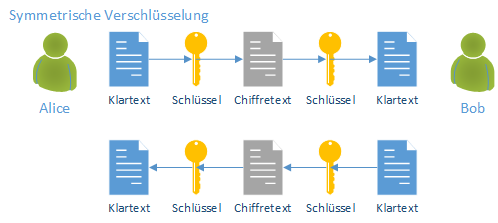
Symmetric encryption
Symmetric encryption uses the same key for encryption and decryption. As a result, the key must be made known to the communication partner in advance via a secure transmission path so that he can decrypt the encrypted data or send encrypted data.
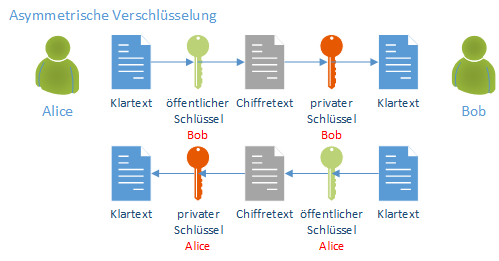
Asymmetric encryption
In asymmetric encryption, each communication partner has two keys (a key pair) that are used for encrypted communication. What has been encrypted with one of the two keys can only be decrypted again with the other key. A distinction is made here between the private and the public key: both keys are technically identical in structure, but the private key must be kept under lock and key by its owner. The public key is issued to the communication partners. They can then encrypt data with this key, which can only be decrypted again by the owner of the private key.
Hybrid encryption
The disadvantage of asymmetric encryption is that it requires considerably more computing capacity than symmetric encryption. Depending on the algorithm used, the difference in speed is between 1 and 5000 compared to symmetric encryption. For this reason, both methods are often used in combination in modern cryptography in order to combine their advantages. This is referred to as a hybrid encryption method. The encryption of the transported data is carried out with a symmetric procedure, an asymmetric procedure is used to encrypt the symmetric key or to make it known to the communication partners (key exchange).
Digital signing
Digital signing ensures the authenticity and integrity of data. This process takes place according to the following scheme:
- A mathematical one-time function (hash algorithm) is used, which generates a checksum of fixed length over the data, which would change if the data were modified, and does not allow any inference about the data (hence the name "one-time function").
- The checksum is encrypted with the signing entity's private key. Other participants can decrypt the signature again with its public key.
- The recipient of the data now creates a checksum of the data using the same hash procedure and compares it with the signed checksum enclosed with the data. If the content of the data was changed during transport, the two checksums differ. In this way, manipulation can be detected.
Since the owner of the private key should be its only owner, this also uniquely identifies the person who issued the signature. This prevents anyone from denying that they issued the signature (non-repudiation). A hash procedure generates a mathematical checksum (hash value, fingerprint, (message) digest) from a plaintext according to a chosen algorithm. It is technically possible, but extremely unlikely, for a hash procedure to arrive at the same checksum for two different plaintexts (collision). Some older hash procedures are now regarded as insecure because collisions can be deliberately induced.
Digital certificates
Digital keys have a decisive disadvantage: they do not contain any meta information (additional information about a piece of information) such as the owner or the intended use of the key. Digital certificates are corresponding data structures that solve this problem:
They represent the electronic representation of a person, computer, network device, or service, and thus link the corresponding key with the associated identity and other meta-information. They are usually generated by a Certification Authority (CA) signed.
Digital certificates are based on asymmetric cryptography and therefore contain a public key. Through the (encrypted with their private key) Signature of the certification authority, the certificate is protected against changes. If one were to change a detail of the certificate, the signature would change and ultimately the certificate itself would lose its trust status.
Before the certification authority signs a certificate, the identity of the applicant must be verified and confirmed, which can be done directly (personal audition of the applicant) or indirectly (e.g., entering a user ID including password), or delegated to a trusted third party (a Registration Authority, RA) can take place.
Such details differ from Certification Authority to Certification Authority and are ideally regulated in legally binding documents (Certificate Policy, CP, and Certificate Practice Statement, CPS) that can be viewed by users of the Certification Authorities.
4 thoughts on “Grundlagen Kryptographie”
Comments are closed.