The following is an overview of the tokens for the CDP and AIA configuration of a certification authority.
| Token | Name | Description |
|---|---|---|
| %1 | ServerDNSName | The fully qualified DNS name of the server on which the certificate authority is installed. |
| %2 | ServerShortName | The NETBIOS name of the server on which the certificate authority is installed. |
| %3 | CaName | The Common Name (CN) of the certification authority. |
| %4 | CertificateName | The certificate index ffor the name of the certification authority certificate. |
| %6 | ConfigurationContainer | The path to the Configuration Container of the Active Directory forest. |
| %7 | CATruncatedName | Name of the certification authority limited to 32 characters, with a checksum. |
| %8 | CRLNameSuffix | The key index for the name of the blacklists. |
| %9 | DeltaCRLAllowed | Replaced by a "+" for a delta CRL. |
| %10 | CDPObjectClass | Placeholder for the cRLDistributionPoint object class in the LDAP path of the CRL Distribution Point extension... |
| %11 | CAObjectClass | Placeholder for the certificationAuthority object class in the LDAP path of the Authority Information Access (AIA) extension. |
Sensible adjustments
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
Make LDAP revocation list paths agnostic from the hostname of the certificate authority server
By default, the following LDAP path is configured for revocation list publishing when a certificate authority is installed.
ldap:///CN=%7%8,CN=%2,CN=CDP,CN=Public Key Services,CN=Services,%6%10
The ServerShortName token (%2) ensures that the LDAP path contains the NETBIOS name of the certification authority server. This can cause problems with Migration of the certification authority to another server bring
A simple trick to get around this is to replace the token with CaName (%3), which describes the common name of the certificate authority.
ldap:///CN=%7%8,CN=%3,CN=CDP,CN=Public Key Services,CN=Services,%6%10
The setting is made in the following registry path:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\CertSvc\Configuration\{Name-der-Zertifizierungsstelle>\CRLPublicationURLs
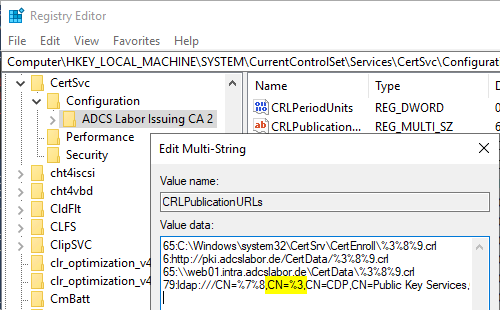
After this configuration adjustment has been made, the certification authority service must be restarted.
In addition, the LDAP path, which now differs from the default, must be created once by first creating a blacklist and then publishing it to Active Directory as Enterprise Administrator.
certutil -f -dspublish {Sperrliste>.crl
When creating the blacklist, the Event no. 74 logged, since the certificate authority directly tries to publish to LDAP and initially fails. However, after the revocation list has been manually uploaded once, the error no longer occurs.
See also article "Publish a certificate revocation list (CRL) to an Active Directory revocation list distribution point (CDP).„.
Related links:
- Configuring Certificate Revocation List (CDP) Distribution Points and Authority Information Access (AIA) Extension of a Certification Authority
- Description of the CRL Distribution Point (CDP) and Authority Information Access (AIA) Extensions
External sources
- How CA Certificates Work (Microsoft)
One thought on “Token für die CDP- und AIA- Konfiguration einer Zertifizierungsstelle”
Comments are closed.