Many companies pursue the strategy of (largely) disabling the NT LAN Manager (NTLM) authentication protocol in their networks.
This is also possible for the administration web page of the network device registration service (NDES). How exactly this is implemented and how this may change the application behavior is explained below.
The Network Device Enrollment Service (NDES) provides a way for devices that do not have an identifier in Active Directory (for example, network devices such as routers, switches, printers, thin clients, or smartphones and tablets) to request certificates from a certification authority. For a more detailed description, see the article "Network Device Enrollment Service (NDES) Basics„.
Requirements
First of all, it must be ensured that Kerberos can also be used on the NDES server. For this purpose, a service principal name must be registered for the web address used. This is always the case if the fully qualified computer name is used to connect to the NDES administration web page and the "SCEP" IIS application pool is running with the integrated virtual identity of the IIS application pool.
For the identity decision process for the IIS application pool, see the article "Selecting the identity for the IIS Network Device Enrollment Service (NDES) application pool.„.
If an alias is used instead, a service principal name must be registered for it (if a service account is used on it, if not on the NDES server computer object).
Checking which service principal names are registered on an account can be done with the following command:
setspn -L {account name}
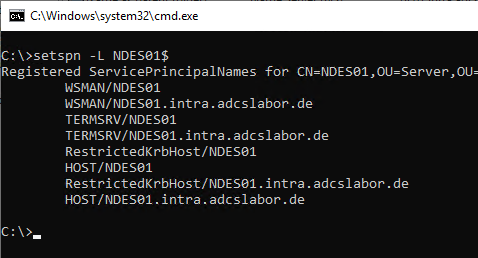
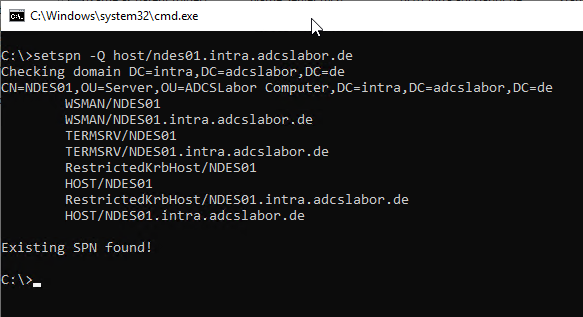
Checking to which account a particular service principal name is registered can be done with the following command:
setspn -Q HOST/{DNS-name-of-alias}
Enforce Kerberos
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem and is available under a free license. It can downloaded via GitHub and can be used free of charge.
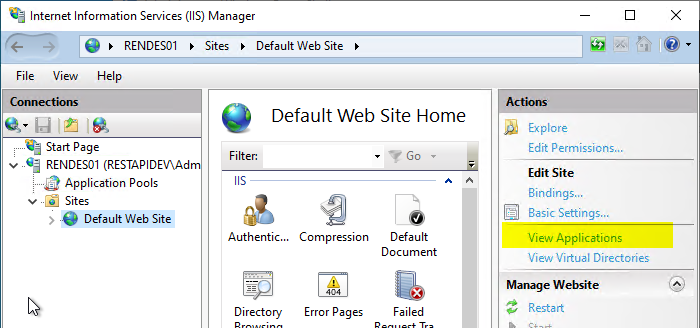
The IIS Manegement Console is started and the option "View Applications" is called in the Default Web Site on the right side.
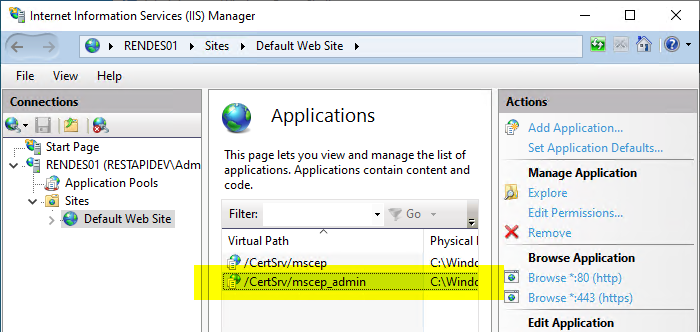
Double-click to open the settings for "/certsrv/mscep_admin".
Here you select the option "Authentication".
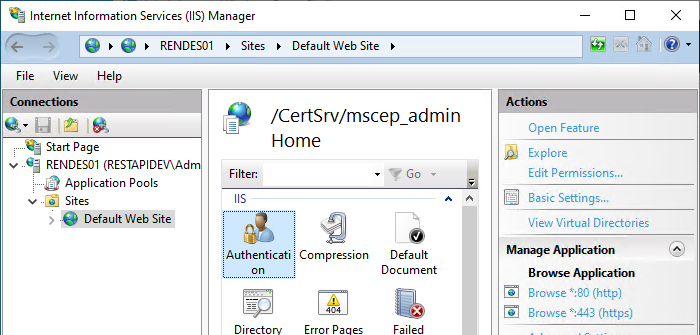
For the "Windows Authentication" option, click on the "Providers" option.
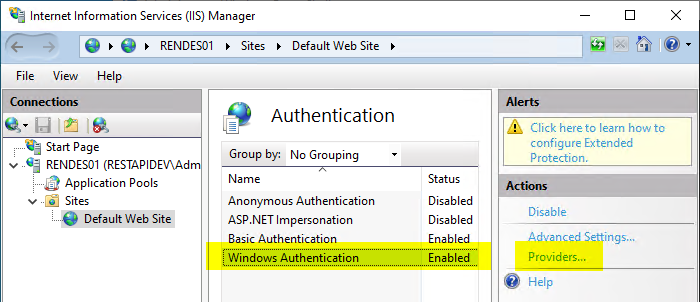
First, all listed providers are removed.
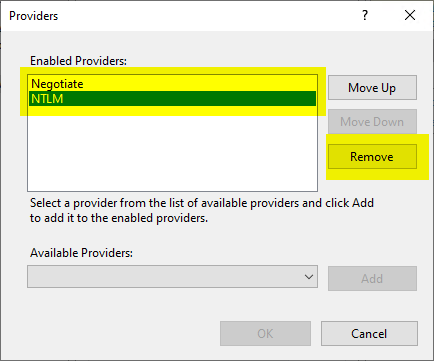
Then the "Negotiate:Kerberos" provider is added to the list.
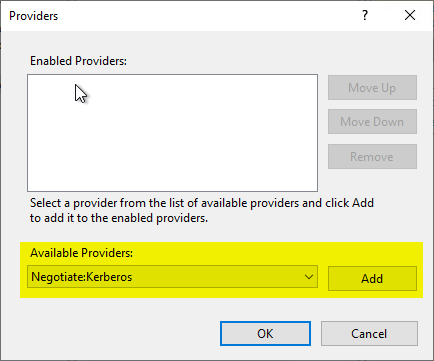
We are informed that now authentication in kernel mode is no longer usable.
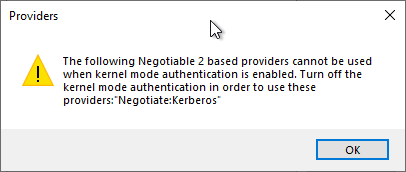
This means that "Advanced Settings..." must now be clicked for "Windows Authentication".
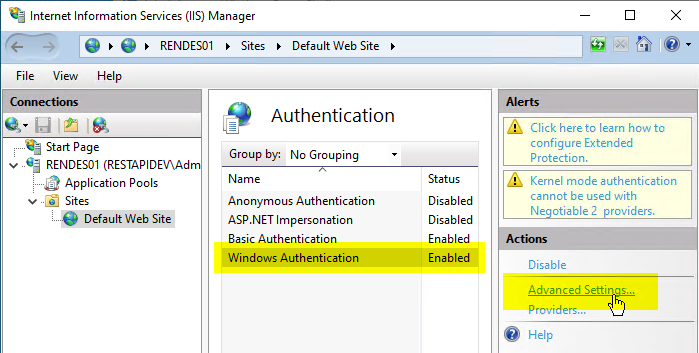
Afterwards, the checkmark at "Enable Kernel-mode authentication" can be removed.
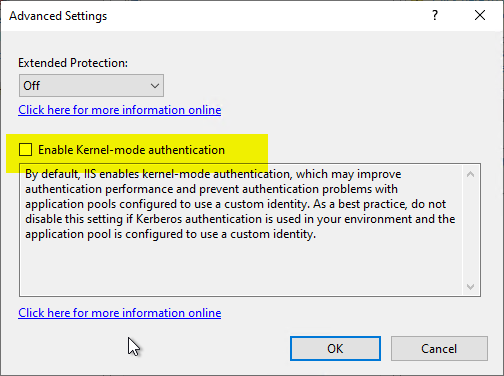
The "Extended Protection" option can and should be set to "Required".
Function test
If the function test is performed with a browser, the DNS name used for the NDES administration web page must now be included in the "Local Intranet" Internet zone.
Of course, such a client must reside in the same Active Directory domain as the NDES server and the certification authority, or at least a trust must exist.
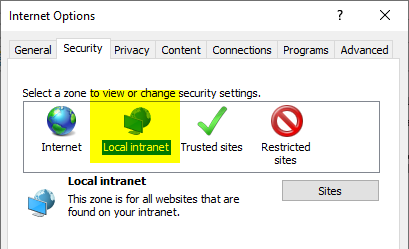
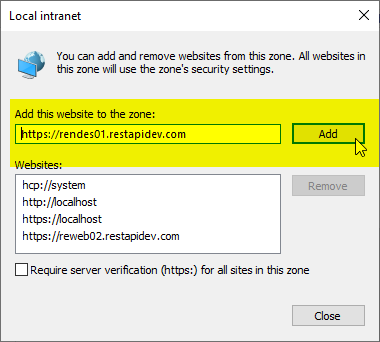
You should then be able to access the NDES administration web page without entering a username and password.
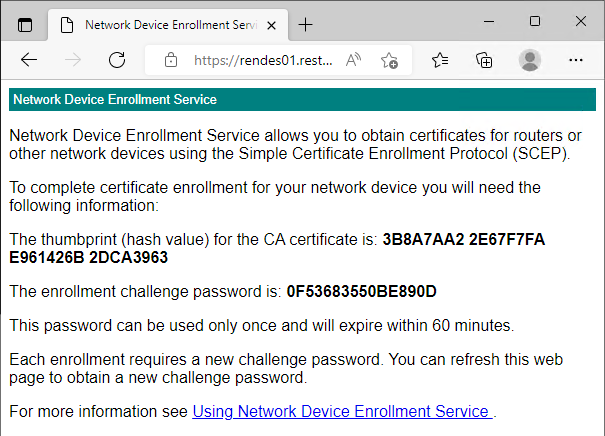
The same applies when using the PSCertificateEnrollment Module.
Import module PSCertificateEnrollment
Get-NDESOTP -ComputerName "{DNS-Name-NDES-Server}"
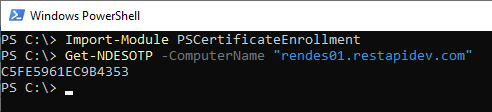
It will now no longer be possible to log in from machines that are not Active Directory domain members. The login dialog will come up endlessly.
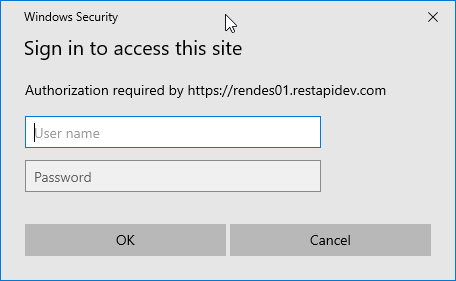
If you cancel it, the HTTP status code 401 Unauthenticated is returned.
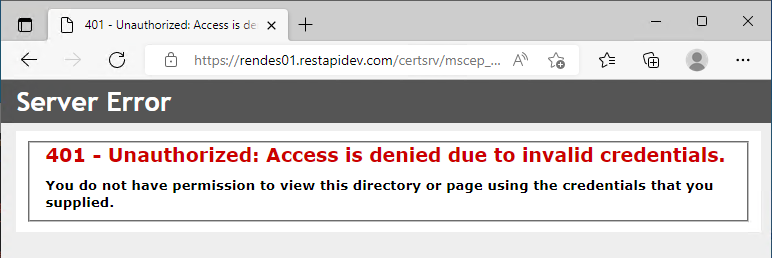
HTTP Basic Authentication upgrade
Enforcing Kerberos removes the ability to log in to the Network Device Registration Service administration page via username and password (as this would have been done with NTLM credentials). However, to provide an option here again, Basic Authentication can be retrofitted.
For this see article "Enabling Basic Authentication for the Network Device Enrollment Service (NDES)„.
2 thoughts on “Deaktivieren von NTLM und erzwingen von Kerberos an der Administrations-Webseite des Registrierungsdienstes für Netzwerkgeräte (NDES)”
Comments are closed.