For security reasons, it may make sense to operate the CES with a Group Managed Service Account (gMSA) instead of a normal domain account. This option offers the charming advantage that the password of the account is changed automatically, and thus this step does not have to be done manually, which is unfortunately forgotten far too often.
The Certificate Enrollment Web Services (Certificate Enrollment Policy Web Service, CEP, and Certificate Enrollment Web Service, CES) enable the automatic request and renewal of certificates from a certification authority via a Web-based interface. This eliminates the need to contact the certification authority directly via Remote Procedure Call (RPC). For a more detailed description, see the article "Certificate request basics via Certificate Enrollment Web Services (CEP, CES)„.
Was CES after the in the article "Installing a Certificate Enrollment Web Service (CES)" described instructions, the service runs with the identity of the application pool after installation.
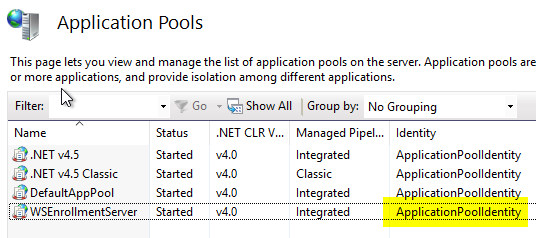
If CEP and CES are installed on the same server and a service account with delegation is used, the CEP and CES application pools must be run under the same account.
Requirements for the CES service account
The CES service account...
- must be a member of the IIS_IUSRS local group.
- requires a Service Principal Name (SPN), which must correspond to the fully qualified server name or the alias to be used, depending on the configuration.
- must be configured for delegated authentication to the certification authority.
Creating the gMSA for the Certificate Enrollment Web Service
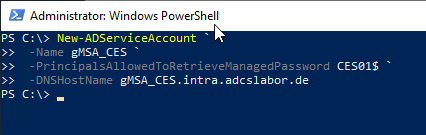
The gMSA for CES can be created with the following PowerShell command, provided that a KDS root key is created in the Active Directory forest was:
New-ADServiceAccount `
-Name gMSA_CES `
-PrincipalsAllowedToRetrieveManagedPassword CES01$ `
-DNSHostName gMSA_CES.intra.adcslabor.com
The arguments given here mean the following:
- The Name argument specifies the name of the gMSA.
- The PrincipalsAllowedToRetrieveManagedPassword specifies the server which is allowed to retrieve the service account password.
- The DNSHostName argument specifies the contents of the account's dNSHostName attribute, since a gMSA technically functions like a computer account.
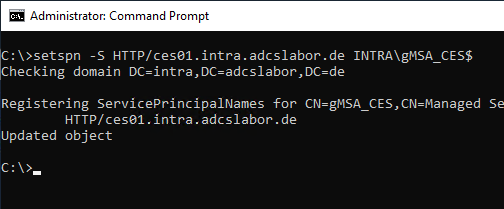
Configure the Service Principal Name (SPN) for the gMSA.
The following command creates the service principal name (SPN) for the gMSA.
setspn -S HTTP/ces01.intra.adcslabor.de INTRA\gMSA_CES$
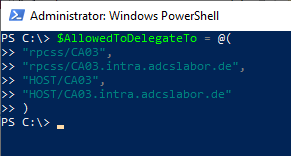
Configuring the delegation settings for the gMSA
Unfortunately, it is not possible to configure the delegation settings for group managed service accounts via a graphical user interface. The configuration must be done via Windows PowerShell.
The following settings are made:
- Limited delegation to the Certification Authority CA03.intra.adcslabor.com without protocol transition ("Use Kerberos only" option) for the "HOST" and "rpcss" protocols.
If authentication with a client certificate is used, delegation with protocol transition must be set up, which can increase the risk for an attack using Kerberoasting.
$AllowedToDelegateTo = @(
"rpcss/CA03",
"rpcss/CA03.intra.adcslabor.com",
"HOST/CA03",
"HOST/CA03.intra.adcslabor.com"
)
Then, the delegation goals are applied to the gMSA.
Get-ADServiceAccount -Identity gMSA_CES | Set-ADObject -Add @{"msDS-AllowedToDelegateTo"=$AllowedToDelegateTo}
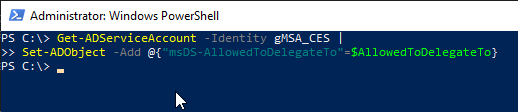
In addition, the option "Account is sensitive and cannot be delegated" must be deactivated.
Get-ADServiceAccount -Identity gMSA_CES | Set-ADServiceAccount -AccountNotDelegated $False
Installing the gMSA on the CES Server
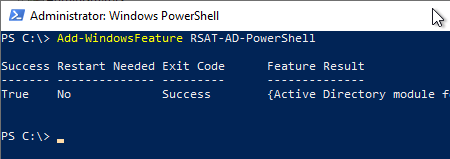
First, the Active Directory management tools for PowerShell must be installed on the CES server.
Add-WindowsFeature RSAT-AD-PowerShell
After that, the service account can be installed on the server with the following PowerShell command.
Install-ADServiceAccount gMSA_CES
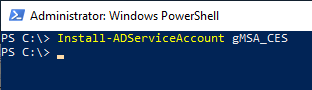
The command returns nothing if it was successful.
You can check if this is really the case with the following command line command.
Test-ADServiceAccount gMSA_CES
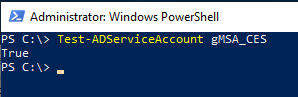
This command returns True back when the gMSA has been successfully installed.
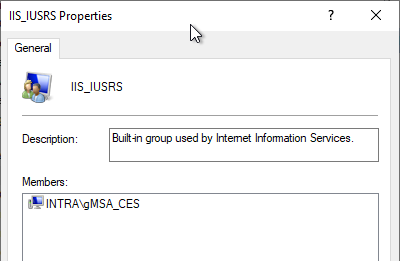
Add gMSA to the IIS_IUSRS group on the CES server.
The configured gMSA must now be added to the local security group IIS_IUSRS so that it can be used by CES. This can be done via the management console for local users (lusrmgr.msc).
Configuring the gMSA in the CES application pool
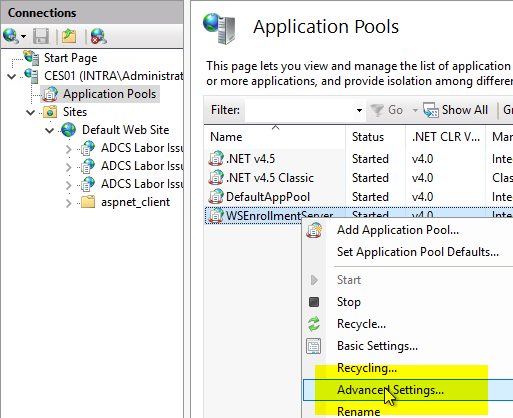
For the CES service to work with the installed gMSA, it must be installed in the WSEnrollmentServer-To do this, right-click on the WSEnrollmentPolicyServer application pool and select the "Advanced Settings..." option.
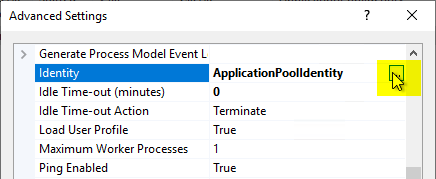
In the "Identity" option, click on the "..." button on the right side. button.
In the following dialog, select "Custom account" and click on "Set...".
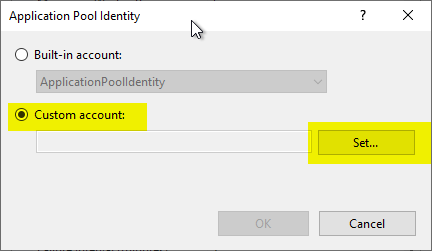
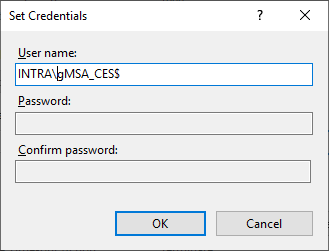
When specifying the identity in the following dialog, some special features have to be considered:
- It is mandatory to specify the domain name.
- Since a gMSA works similarly to a computer account, a dollar sign must be specified at the end of the account noun.
- With a gMSA, no password is specified, so the two fields must remain empty.
Restarting the Web Server service
The Web Server service is then restarted with the iisreset command.
One thought on “Den Certificate Enrollment Web Service (CES) für den Betrieb mit einem Group Managed Service Account (gMSA) konfigurieren”
Comments are closed.