Once a group policy with audit settings is active, the default auditing rules preconfigured with the operating system are turned off and only the explicitly configured audit settings are applied.
This is because the audit settings within the group policy are mapped as a CSV file. Thus, the audit.csv of the group policy at the lowest level overwrites that of all parent ones.
It is therefore recommended that the standard auditing rules be included in the group policy for the certification authority.
Tested operating system: Windows Server 2019. Results may differ for other operating systems.
| Setting Standard | Setting Microsoft Baseline | |
|---|---|---|
| System | ||
| Security System Extension | No Auditing | Success |
| System Integrity | Success, Failure | Success, Failure |
| IPsec Driver | No Auditing | Not configured |
| Other System Events | Success, Failure | Success, Failure |
| Security State Change | Success | Success |
| Logon/Logoff | ||
| Logon | Success, Failure | Success, Failure |
| Logoff | Success | Not configured |
| Account lockout | Success | Failure |
| IPsec Main Mode | No Auditing | Not configured |
| IPsec Quick Mode | No Auditing | Not configured |
| IPsec Extended Mode | No Auditing | Not configured |
| Special Logon | Success | Success |
| Other Logon/Logoff Events | No Auditing | Success, Failure |
| Network Policy Server | Success, Failure | Not configured |
| User / Device Claims | No Auditing | Not configured |
| Group Membership | No Auditing | Success |
| Object Access | ||
| File System | No Auditing | Not configured |
| Registry | No Auditing | Not configured |
| Kernel Object | No Auditing | Not configured |
| SAM | No Auditing | Not configured |
| Certification Services | No Auditing | Not configured |
| Application Generated | No Auditing | Not configured |
| Handle manipulation | No Auditing | Not configured |
| File Share | No Auditing | Success, Failure |
| Filtering Platform Packet Drop | No Auditing | Not configured |
| Filtering Platform Connection | No Auditing | Not configured |
| Other Object Access Events | No Auditing | Success, Failure |
| Detailed File Share | No Auditing | Failure |
| Removable Storage | No Auditing | Success, Failure |
| Central Policy Staging | No Auditing | Not configured |
| Privilege Use | ||
| Non Sensitive Privilege Use | No Auditing | Not configured |
| Other Privilege Use Events | No Auditing | Not configured |
| Sensitive Privilege Use | No Auditing | Success, Failure |
| Detailed Tracking | ||
| Process Creation | No Auditing | Success |
| Process Termination | No Auditing | Not configured |
| DPAPI Activity | No Auditing | Not configured |
| RPC Events | No Auditing | Not configured |
| Plug and Play Events | No Auditing | Success |
| Token Right Adjusted Events | No Auditing | Not configured |
| Policy Change | ||
| Audit Policy Change | Success | Success |
| Authentication Policy Change | Success | Success |
| Authorization Policy Change | No Auditing | Not configured |
| MPSSVC Rule-Level Policy Change | No Auditing | Success, Failure |
| Filtering Platform Policy Change | No Auditing | Not configured |
| Other Policy Change Events | No Auditing | Failure |
| Account Management | ||
| Computer Account Management | Success | Not configured |
| Security Group Management | Success | Success |
| Distribution Group Management | No Auditing | Not configured |
| Application Group Management | No Auditing | Not configured |
| Other Account Management Events | No Auditing | Not configured |
| User Account Management | Success | Success, Failure |
| DS Access | ||
| Directory Service Access | Success | Not configured |
| Directory Service Changes | No Auditing | Not configured |
| Directory Service Replication | No Auditing | Not configured |
| Detailed Directory Service Replication | No Auditing | Not configured |
| Account Logon | ||
| Kerberos Service Ticket Operations | Success | Not defined |
| Other Account Logon Events | No Auditing | Not defined |
| Kerberos Authentication Service | Success | Not defined |
| Credential Validation | Success | Success and Failure |
Check audit settings at operating system level
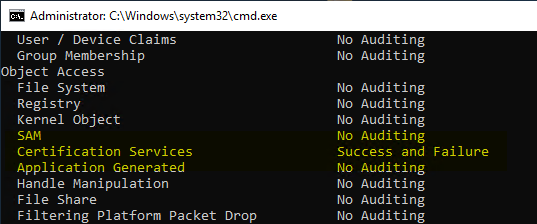
The audit settings on operating system level can be queried with the following command. In the "Object Access" area, there is a "Certification Services" category.
auditpol.exe /get /category:*
3 thoughts on “Standard-Auditierungsregeln für Windows Server Betriebssysteme”
Comments are closed.