| Event Source: | Microsoft Windows Kerberos Key Distribution Center |
| Event ID: | 39 (0x80000027) |
| Event log: | System |
| Event type: | Warning or error |
| Event text (English): | The Key Distribution Center (KDC) encountered a user certificate that was valid but could not be mapped to a user in a secure way (such as via explicit mapping, key trust mapping, or a SID). Such certificates should either be replaced or mapped directly to the user via explicit mapping. See https://go.microsoft.com/fwlink/?linkid=2189925 to learn more. User: %1 Certificate Subject: %2 Certificate Issuer: %3 Certificate Serial Number: %4 Certificate Thumbprint: %5 |
| Event text (German): | The Key Distribution Center (KDC) has found a valid user certificate, but it could not be mapped to a user in a secure way (for example, via an explicit mapping, a key trust mapping, or an SID). Such certificates should either be replaced or mapped directly to the user via an explicit mapping. For more information, see https://go.microsoft.com/fwlink/?linkid=2189925 User: %1 Certificate requester: %2 Certificate issuer: %3 Certificate serial number: %4 Certificate fingerprint: %5 |
Parameter
The parameters contained in the event text are filled with the following fields:
- %1: AccountName (win:UnicodeString)
- %2: Subject (win:UnicodeString)
- %3: Issuer (win:UnicodeString)
- %4: SerialNumber (win:UnicodeString)
- %5: Thumbprint (win:UnicodeString)
- %6: __binLength (win:UInt32)
- %7: binary (win:Binary)
Example events
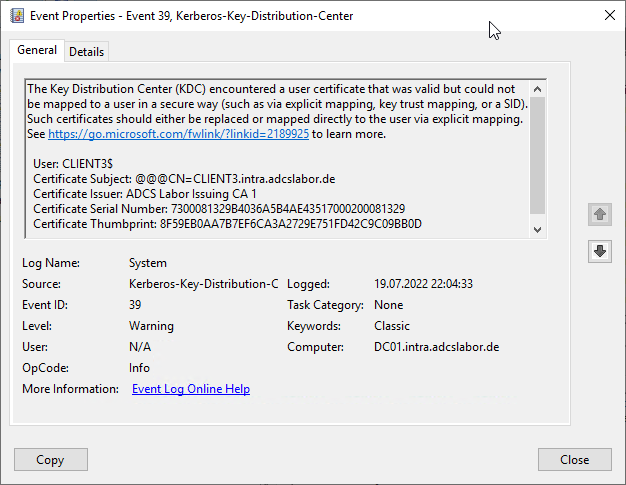
The Key Distribution Center (KDC) encountered a user certificate that was valid but could not be mapped to a user in a secure way (such as via explicit mapping, key trust mapping, or a SID). Such certificates should either be replaced or mapped directly to the user via explicit mapping. See https://go.microsoft.com/fwlink/?linkid=2189925 to learn more.
User: CLIENT3$
Certificate Subject: @@@CN=CLIENT3.intra.adcslabor.de
Certificate Issuer: ADCS Labor Issuing CA 1
Certificate Serial Number: 730008133096D311F7A6CAA281000200081330
Certificate Thumbprint: 41AE3BFFB376CCBA37183AAE606E5D84ACB4F432
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem and is available under a free license. It can downloaded via GitHub and can be used free of charge.
Description
This event occurs when a certificate logon is rejected because the certificate content is no longer considered secure. Typically, this happens in corporate networks when using the Network Policy Server (NPS), an IIS web server that processes certificate-based logins, or even smart card logins.
Microsoft has with the patch of May 10, 2022, a change to the processing of certificate-based logins against the Active Directory introduced.
This includes but is not limited to:
- The certification authority enters a new certificate extension in issued certificates, which contains the security identifier (objectSid) of the corresponding account.
- Domain controllers expect the new certificate extension in issued certificates, but are in a compatibility mode until May 09, 2023.
- The SChannel library now only applies certain methods classified as "secure" to map identities from certificates back to Active Directory identities.
Safety assessment
The security assessment is based on the three dimensions of confidentiality, integrity and availability.
An alert should definitely be triggered for this event, since certificates are not accepted in the event of logging. This can indicate an attack, but also a misconfiguration with an effect on availability.
Related links:
- Changes to Certificate Issuance and Certificate-Based Logon to Active Directory with the May 10, 2022 Patch for Windows Server (KB5014754)
- Overview of Active Directory events relevant for PKI
- Overview of Windows events generated by the certification authority
- Overview of audit events generated by the Certification Authority
External sources
- KB5014754-Certificate-based authentication changes on Windows domain controllers (Microsoft Corporation)
2 thoughts on “Details zum Ereignis mit ID 39 der Quelle Microsoft-Windows-Kerberos-Key-Distribution-Center”
Comments are closed.