Sometimes it is necessary to allow Relative Distinguished Names (RDNs) in issued certificates that are not defined and accordingly not included in the SubjectTemplate value of the certification authority registration could be configured.
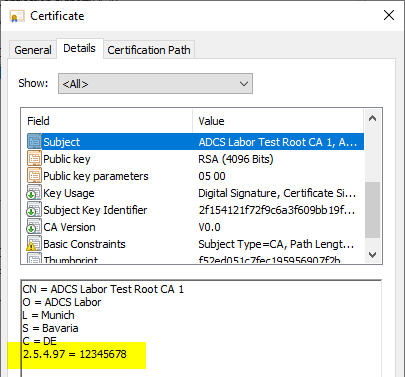
An example of this is the Organization Identifier with Object Identifier 2.5.4.97, which is required, for example, for certificates that are used for the eIDAS Regulation are compliant.
Configuration steps for root certification authority certificates
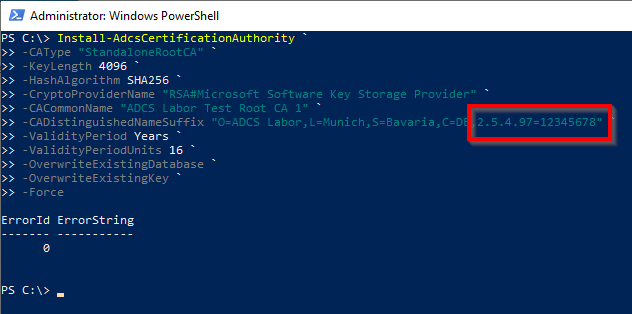
No special configuration steps are required for certificates from root certification authorities. Since their attributes are defined during the installation of the certification authority role, they can be easily configured using the -CADistinguishedNameSuffix parameters (for installation via graphical user interface there is a corresponding input field).
Install-AdcsCertificationAuthority ` -CAType "StandaloneRootCA" ` -KeyLength 4096 ` -HashAlgorithm SHA256 ` -CryptoProviderName "RSA#Microsoft Software Key Storage Provider" ` -CACommonName "ADCS Lab Test Root CA 1" ` -CADistinguishedNameSuffix "O=ADCS Lab,L=Munich,S=Bavaria,C=DE,2.5.4.97=12345678" ` -ValidityPeriod Years ` -ValidityPeriodUnits 16 ` -OverwriteExistingDatabase ` -OverwriteExistingKey ` -Force `
Configuration steps for all other types of certificates
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
Concerns the behavior of Certification Authorities when issuing certificates and thus all types of Certification Authorities:
- Master Certification Authorities
- Intermediate Certification Authorities
- Issuing Certification Authorities
In order to prevent certification authorities from recreating the subject based on the rules defined in the "SubjectTemplate" registry value when issuing the certificate, the following command line command can be issued:
certutil -setreg CA\CRLFlags +CRLF_REBUILD_MODIFIED_SUBJECT_ONLY
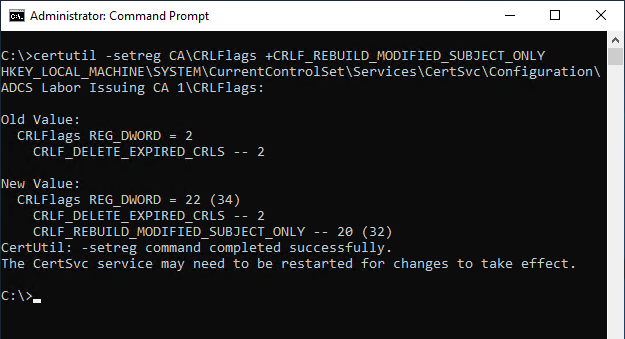
The Certification Authority service must then be restarted for the changes to be applied.
If this setting is active, the certification authority no longer checks the syntax and conformity to the relevant RFC. In any case, the certificate request must be checked manually by a certificate manager. Since the setting applies globally to the certification authority, a dedicated issuing certification authority should be used for these requests to avoid interactions.
The settings for the Character encoding within RDNs (ForceTeletex) are also overridden by setting this flag, i.e. the subject DN is taken over 1:1 from the certificate request, also with regard to the character encoding.
Certificate Enrollment
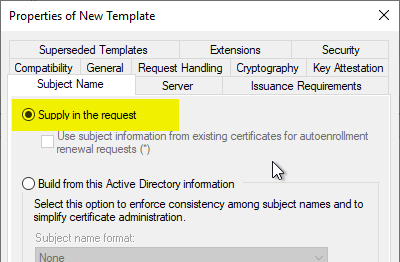
The setting has an effect only if the certificate template is configured to allow the requester to specify the subject in the certificate request.
Further information
- Change the order of the Relative Distinguished Names (RDNs) in the subject of issued certificates.
- Allowed Relative Distinguished Names (RDNs) in the Subject of Issued Certificates
- Character encoding in the Subject Distinguished Name of certificate requests and issued certificates
External sources
- eIDAS Regulation on electronic identification and trust services (German Federal Office for Information Security)
- How to generate eIDAS certificate using OpenSSL (enable:Banking)
6 thoughts on “Verwenden von nicht definierten Relative Distinguished Names (RDN) in ausgestellten Zertifikaten”
Comments are closed.