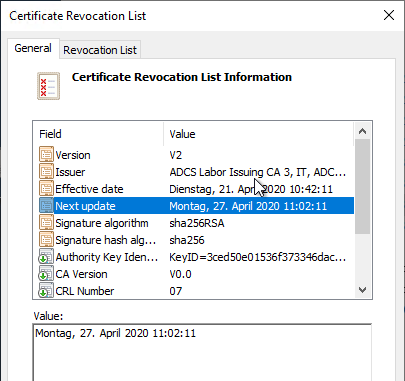
The most important component of a PKI in terms of availability is not the certification authority, as is often assumed, but the revocation list distribution points. If a certification authority is unavailable, initially no new certificates can be issued, but the certificates already issued can continue to be used without hindrance as long as their revocation status can be verified. In addition to the pure availability of the revocation list distribution points, the revocation information must of course also be valid in terms of its signature. Revocation lists have a defined expiration date after which they can no longer be used. If a certification authority has now failed, it can also no longer publish new revocation lists. The process of emergency signing of revocation lists is provided for this case.
Basics
The basic idea behind emergency signing is to re-sign an existing revocation list directly with the private key, bypassing the certification authority, and to enter a new, extended expiration date in the revocation list in the process. So if the failure of the certification authority lasts longer than the validity of the revocation list, it can be extended as long as access to the private key of the certification authority is possible by means of the emergency revocation list.
The first step to be taken after a certification authority failure should therefore not be to analyze the error or even to restore the certification authority from the backup, but first to generate an emergency blacklist.
There is also nothing to be said against proactively carrying out this process as long as the certification authority is still working properly. In this way, provisions have already been made for the event of a failure of the Certification Authority. Also for the Migration of a certification authority to another server or in case of upcoming maintenance work, a prior emergency signing can be very helpful.
Implementation of the emergency signature
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
If the certification authority is no longer available, the private key of the certification authority must first be restored on another system. See the following articles:
- Restoration of a certification authority certificate with software key
- Restoration of a Certification Authority Certificate with Hardware Security Module (HSM)
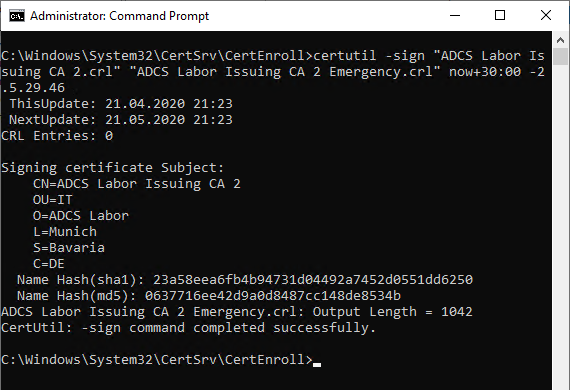
The emergency invalidation of the blacklist is executed with the following command line command:
certutil -sign {blocklist-old}.crl {blocklist-new}.crl now+{days}:{hours} -2.5.29.46
The argument -2.5.29.46 removes the "Freshest CRL" extension from the generated emergency revocation list. This extension normally refers to a delta revocation list, which would naturally expire in the same way as the base revocation list. For this reason, the reference to the delta revocation list is removed.
For example, if you want to create a lock file with the filename crl.crl into an emergency blacklist called emergency.crl and a validity of 30 days would be written, one would execute the following command.
certutil -sign crl.crl emergency.crl now+30:00 -2.5.29.46
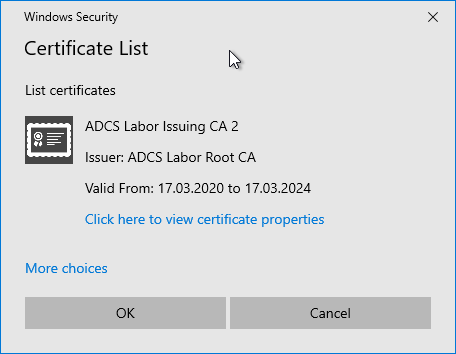
During the signature process, you are prompted to select a certificate for signing the revocation lists. Here, exactly the certificate authority certificate matching the revocation list must be selected. Particularly if the certification authority has multiple certification authority certificates and keys, attention must be paid to this fact, otherwise the revocation list will not have a valid signature.
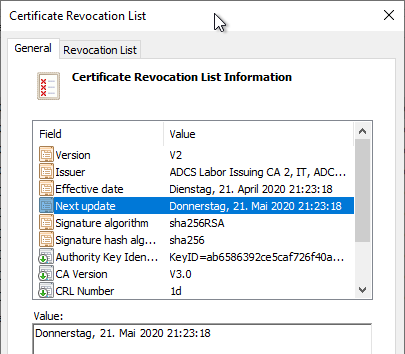
The emergency blacklist now generated should have an expiration date of 30 days from the time of the emergency signature.
Publication of the emergency blacklists to the revocation list distribution points.
The emergency blacklist can now either be kept for emergency use or published directly to the revocation list distribution points.
6 thoughts on “Durchführen der Notfallsignierung von Zertifikatsperrlisten”
Comments are closed.