| Event Source: | Microsoft-Windows-CertificationAuthority |
| Event ID: | 130 (0x82) |
| Event log: | Application |
| Event type: | Error |
| Symbolic Name: | MSG_E_CRL_CREATION |
| Event text (English): | Active Directory Certificate Services could not create a certificate revocation list. %1. This may cause applications that need to check the revocation status of certificates issued by this CA to fail. You can recreate the certificate revocation list manually by running the following command: "certutil -CRL". If the problem persists, restart Certificate Services. |
| Event text (German): | No certificate revocation list could be created by Active Directory Certificate Services. %1. This may cause an error to occur in applications that require checking the revocation status of certificates issued by this certificate authority. The certificate revocation list can be manually recreated by running the following command: "certutil -CRL". If the problem persists, restart Certificate Services. |
Parameter
The parameters contained in the event text are filled with the following fields:
- %1: ErrorMessageText (win:UnicodeString)
Example events
Active Directory Certificate Services could not create a certificate revocation list. Bad Data. 0x80090005 (-2146893819 NTE_BAD_DATA). This may cause applications that need to check the revocation status of certificates issued by this CA to fail. You can recreate the certificate revocation list manually by running the following command: "certutil -CRL". If the problem persists, restart Certificate Services.
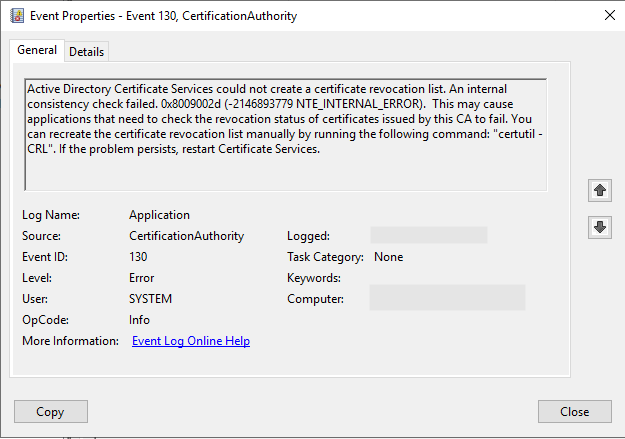
Active Directory Certificate Services could not create a certificate revocation list. An internal consistency check failed. 0x8009002d (-2146893779 NTE_INTERNAL_ERROR). This may cause applications that need to check the revocation status of certificates issued by this CA to fail. You can recreate the certificate revocation list manually by running the following command: "certutil -CRL". If the problem persists, restart Certificate Services.
Active Directory Certificate Services could not create a certificate revocation list. An attempt was made to open a Certification Authority database session, but there are already too many active sessions. The server may need to be configured to allow additional sessions 0x8009400f (-2146877425). This may cause applications that need to check the revocation status of certificates issued by this CA to fail. You can recreate the certificate revocation list manually by running the following command: "certutil -CRL". If the problem persists, restart Certificate Services.
Description
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
This event occurs when the certificate authority attempts to generate a certificate revocation list but is unable to do so.
Error code NTE_BAD_DATA
If a SafeNet Hardware Security Module (HSM) is used, this error can occur if the network connection to the HSM is lost and the certification authority can no longer access the private key.
See article "Certificate request fails with error message "Bad Data. 0x80090005 (-2146893819 NTE_BAD_DATA)."„.
In the same context, events no. 86 and 88 occur.
Error code NTE_INTERNAL_ERROR
In many cases, the cause is that the private key cannot be accessed. If a hardware security module (HSM) is used, this indicates a problem with it, for example:
- Problem with the network connection between the certification authority and the HSM.
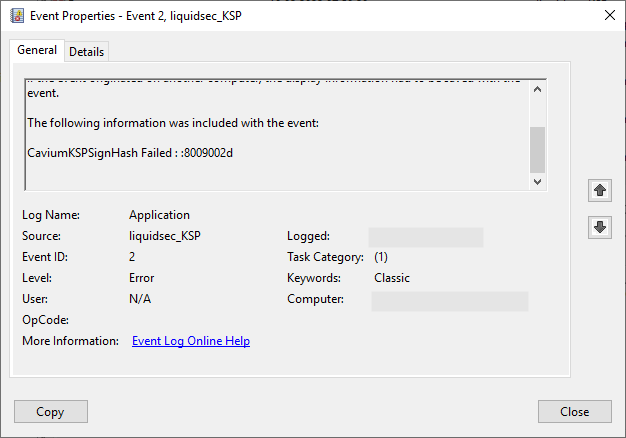
- Problem with the installed on the certification authority Key Storage Provider (KSP) of the HSM (especially if the Cavium Key Storage Provider of the AWS CloudHSM is used).
- Problem with authentication at the HSM.
- Failure of the HSM.
Error code CERTSRV_E_NO_DB_SESSIONS
See article "Certificate or revocation list issuance fails with error code CERTSRV_E_NO_DB_SESSIONS„.
Safety assessment
The security assessment is based on the three dimensions of confidentiality, integrity and availability.
If the certification authority is not able to generate or publish a revocation list, it is highly likely that it will expire on the distribution points in a short time. In this case, there is a threat of failure of the IT services that depend on the PKI. Therefore, this event must be rated as "critical" in terms of availability.
Furthermore, it is imperative that a process for the Emergency signing of blacklists be established in order to be able to take appropriate emergency measures in the event of a failure.
Microsoft rating
Microsoft evaluates this event in the Securing Public Key Infrastructure (PKI) Whitepaper with a severity score of "Low".
Related links:
- Overview of Windows events generated by the certification authority
- Overview of audit events generated by the Certification Authority
4 thoughts on “Details zum Ereignis mit ID 130 der Quelle Microsoft-Windows-CertificationAuthority”
Comments are closed.