If private key archiving has been enabled, it may be necessary to export these keys from the certificate authority database and convert them to another format (PKCS#12, PFX), for example for long-term archiving.
Below is a description of the procedure for exporting individual or all archived keys and obtaining the necessary meta-information.
Basics
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
The executing user needs the "Manage CA" and "Issue and manage Certificates" permissions on the certificate authority for this step.
An archived key can be exported from the certification authority database using the following command.
certutil -getkey {serial number}
Please note that the command line output differs depending on the state. If the Key Recovery Agent (KRA) certificate required for the exported key is present in the user profile of the user performing the export, the meta information is not output. For this reason, it may be useful to run the command without the KRA certificates to obtain complete information.
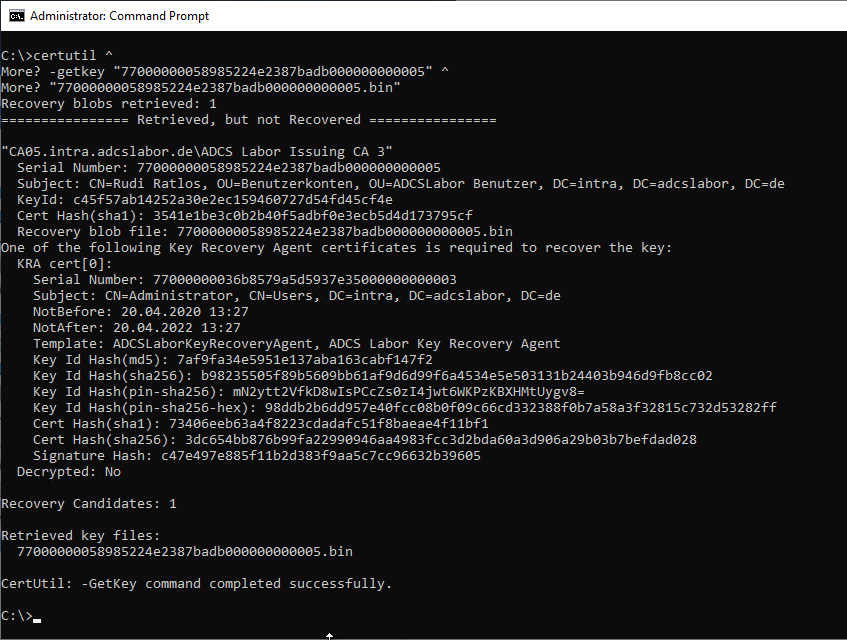
However, the rest of the article describes a way to read the same information from the certification authority database and save it in a list before exporting it.
Determine all keys for export from the certification authority database
Note: The executing user needs the "Manage CA" and "Issue and manage Certificates" permissions on the certificate authority for this step.
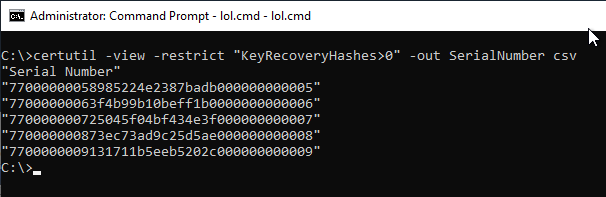
Not all certificates stored in the certification authority database also have an archived private key. A list of which certificates these are can be output with the following command. The output is in CSV format, which is perfect for further processing.
certutil -view -restrict "KeyRecoveryHashes>0" -out SerialNumber csv
For long-term archiving, it may be useful to include additional attributes in the list. For example, the following attributes are suitable:
- The RequestId Attribute describes the unique identifier of the certificate in the certificate authority database.
- The RequesterName Attribute describes the certificate requester.
- The SerialNumber attribute describes the unique serial number of the certificate.
- The NotBefore Attribute describes the beginning of the validity of the certificate.
- The NotAfter Attribute describes the end of validity of the certificate.
- The KeyRecoveryHashes Attribute describes with which Key Recovery Agent certificates the private key was archived. If the key is archived with multiple KRA certificates, they are separated by a "+" sign. For recovery, the private key of one of the KRA certificates must be present.
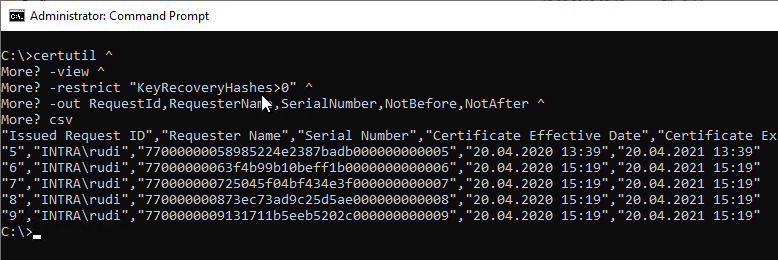
The adapted command would look accordingly as follows:
certutil -view -restrict "KeyRecoveryHashes>0" -out RequestId,RequesterName,SerialNumber,NotBefore,NotAfter,KeyRecoveryHashes csv
To save the results to a file, the following command can be used.
certutil -view -restrict "KeyRecoveryHashes}0" -out RequestId,RequesterName,SerialNumber,NotBefore,NotAfter,KeyRecoveryHashes csv } C:\LabFiles\SerialNumber.txt
This data set can now be used, for example, in Excel can be imported for further evaluation, or processed further with the Windows PowerShell.
Import-Csv -Path C:\LabFiles\SerialNumber.txt
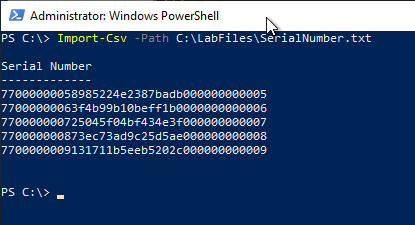
Exporting the keys from the certification authority database
The previously created list of serial numbers is now read in via Windows PowerShell and used to export the individual keys.
Import-Csv -Path SerialNumber.txt | ForEach-Object -Process { certutil -getkey $_. "Serial Number" "$($_. "Serial Number").bin" }
The command line arguments used for the certutil command here mean the following:
- The -getkey argument specifies that the key should be exported from the certification authority database to a file.
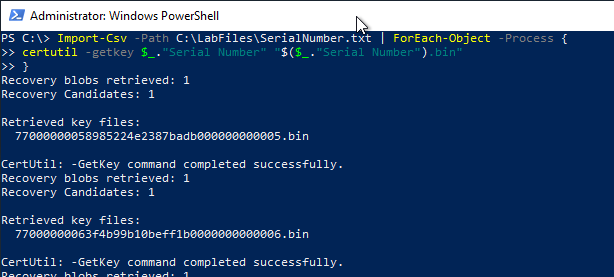
This step only exported the keys from the database, but they are still encrypted. This form of storage would be suitable for long-term archiving, for example, provided that the Key Recovery Agent (KRA) certificates are still accessible.
Decrypting the archived keys - conversion to a PFX file
The previous command exported the keys from the database in encrypted form. Typically, this should already be sufficient for secure archiving if, for example, the certification authority is to be decommissioned. However, under certain circumstances it may be desired to convert the keys to PKCS#12 format (.pfx).
For this step it is necessary that all used Key Recovery Agent certificates including private keys are installed on the system or are available.
In the following example, the same password is used for all exported keys - thus the security of all keys is bound to the knowledge of this one password. This approach is therefore not recommended in practice. Strong, randomly generated passwords and, above all, passwords that are unique for each key should be used, which could be realized with correspondingly more complex program logic.
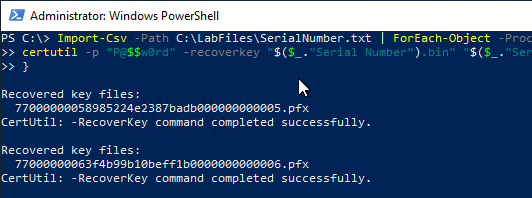
To export the archived keys, the following command can be used.
Import-Csv -Path SerialNumber.txt | ForEach-Object -Process { certutil -p "P@$$w0rd" -recoverkey "$($_. "Serial Number").bin" "$($_. "Serial Number").pfx" }
The command line arguments used for the certutil command here mean the following:
- The -p argument specifies the password for the PFX file to be created.
- The -recoverkey Argument indicates that the key should be decrypted by the key recovery agent.
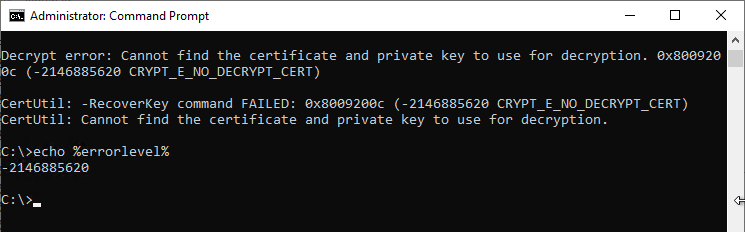
If the process fails, for example because the matching Key Recovery Agent certificate is not available, this result is output accordingly and stored in the %ERRORLEVEL% variable for further processing.
Decrypt error: Cannot find the certificate and private key to use for decryption. 0x8009200c (-2146885620 CRYPT_E_NO_DECRYPT_CERT)
CertUtil: -RecoverKey command FAILED: 0x8009200c (-2146885620 CRYPT_E_NO_DECRYPT_CERT)
CertUtil: Cannot find the certificate and private key to use for decryption.
Related links:
External sources
- Performing the Upgrade or Migration (Microsoft)