Authentication Mechanism Assurance (AMA) provides the ability to tie membership in a security group to enrollment with a smart card certificate containing a specific Object Identifier (OID).
If the user does not log in with the smartcard certificate, but with user name and password, he is also not a member of the security group.
The following describes how to establish the connection between the certificate and the security group.
Requirements
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
Before the configuration is made, the following steps are necessary:
- Configure a certificate template for Authentication Mechanism Assurance. In the course of this, the required Object Identifier (OID) is created.
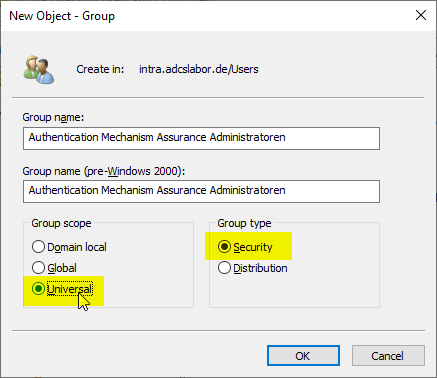
- Create or edit a universal security group
Configuring a Certificate Template for Authentication Mechanism Assurance
The configuration of a certificate template for Authentication Mechanism Assurance is described in the article "Configuring a Certificate Template for Authentication Mechanism Assurance (AMA)“ described.
Create or edit the universal security group
Authentication Mechanism Assurance works only with universal security groups. This must be thought of when creating the security group, or the existing group must be converted to a universal group.
Establishing the connection between the object identifier and the security group
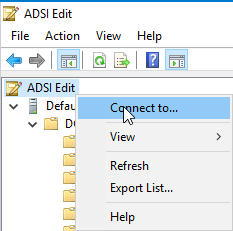
Then the ADSI Editor (adsiedit.msc) must be called to establish the connection. In the top node, right-click and select "Connect to...".
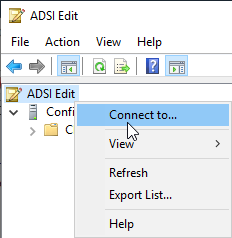
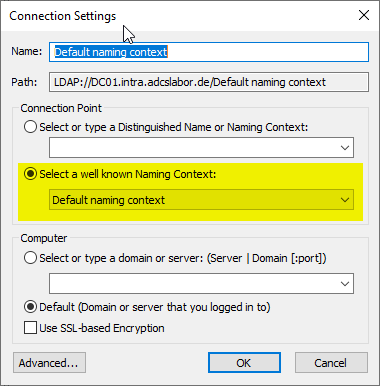
A connection is established with the Default Naming Context manufactured.
Now navigate to the location of the universal group and select the group. It is right-clicked and "Properties" is selected.
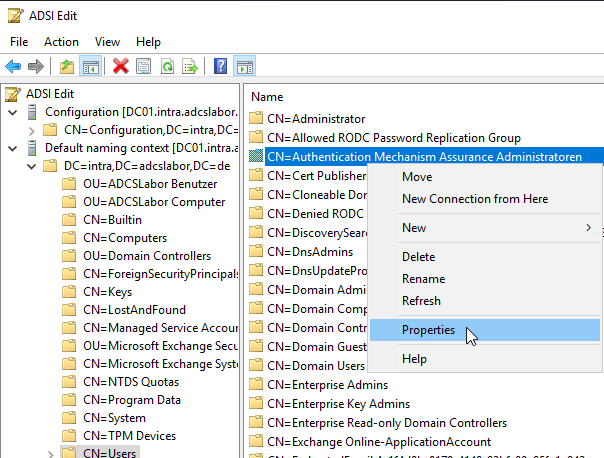
We need the distinguishedName Attribute.
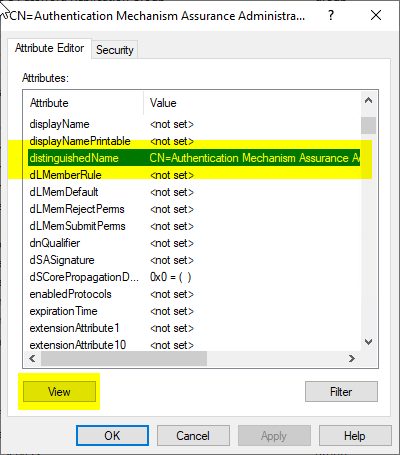
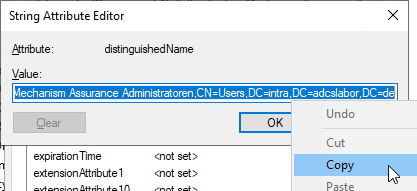
Its content is copied and cached.
Now right-click again in the top node and select "Connect to...".
This time with the Configuration Context connected.
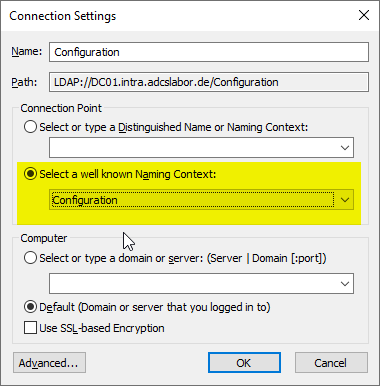
Now navigate to the following substructure.
CN=OID,CN=Public Key Services,CN=Services,CN=Configuration
Now you have to search for the object that contains the desired object identifier. This is defined in the attribute msPKI-Cert-Template-OID Saved.
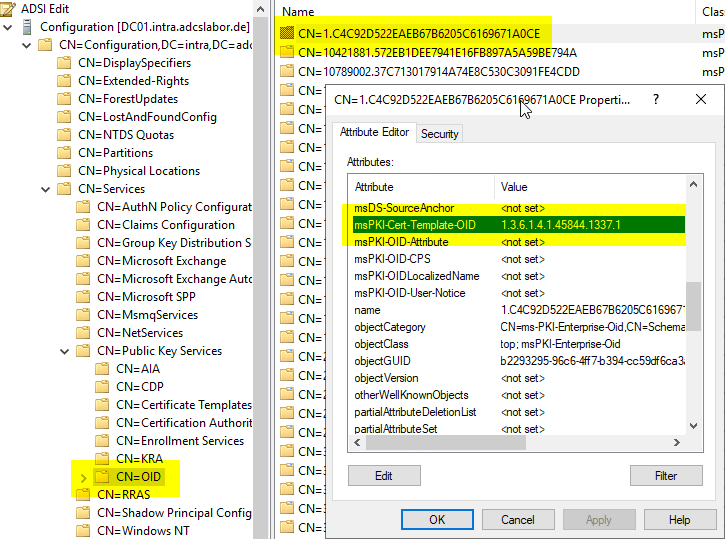
In the found object the attribute msDS-OIDToGroupLink Edited.
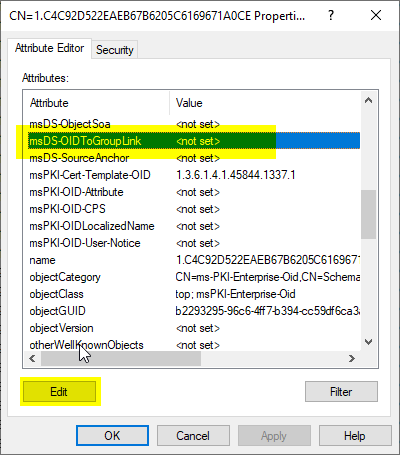
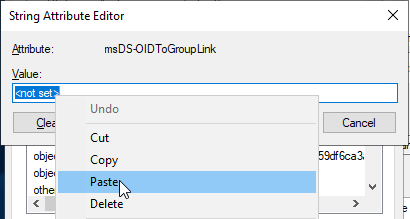
Here the previously copied value from the distinguishedName Attribute of the universal safety group entered.
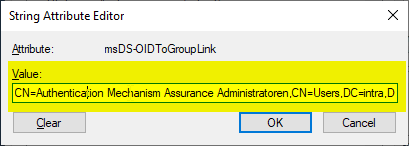
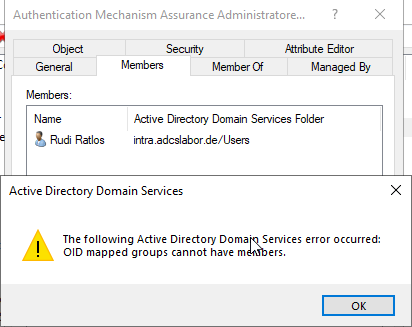
The connection is now established. This can be checked, for example, by now trying to assign a member to the universal security group. Since the group membership is assigned dynamically, this should fail with the following error:
The following Active Directory Domain Services error occurred: OID mapped groups cannot have members.
2 thoughts on “Eine universelle Sicherheitsgruppe mit einem Object Identifier (OID) im Active Directory Verzeichnisdienst verbinden (Authentication Mechanism Assurance)”
Comments are closed.