Authentication Mechanism Assurance (AMA) provides the ability to tie membership in a security group to enrollment with a smart card certificate containing a specific Object Identifier (OID).
If the user does not log in with the smartcard certificate, but with user name and password, he is also not a member of the security group.
The following describes how to generate a certificate template for use with Authentication Mechanism Assurance.
Requirements
Before the certificate template can be created, an Object Identifier (OID) must be defined for the issuing policy. This should be within a namespace that one owns. The (IANA) offers the possibility, register a Private Enterprise Number (PEN) below their OID tree for freewhich can be used for this purpose
Creating the certificate template
The certificate template is created using the certificate template management console (certtmpl.msc).
The resulting certificate is basically a smartcard logon certificate. For this reason, the certificate template of the same name is also used as the starting point. It is right-clicked and "Duplicate Template" is selected.
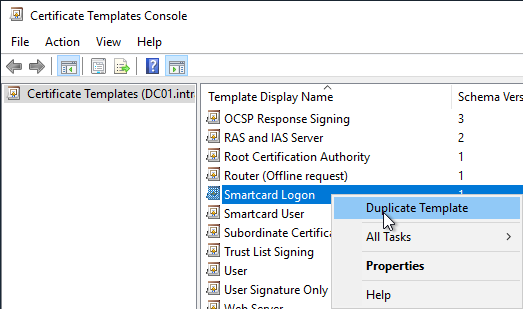
Instead of the Microsoft Base Smart Card Crypto Provider, should the more modern Microsoft Smart Card Key Storage Provider should be used, compatibility at least on Windows Server 2008 / Windows Vista (version 3 certificate template) should be selected in the "Compatibility" tab.
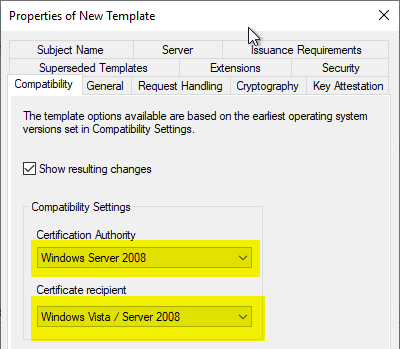
A meaningful name is assigned in the "General" tab.
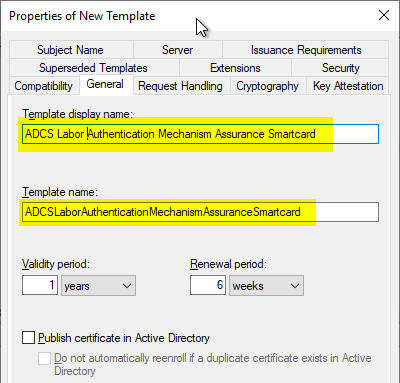
In the "Cryptography" tab, the Provider Category is changed to "Key Storage Provider". Then select the option "Requests must use one of the following providers" and only use the Microsoft Smart Card Key Storage Provider selected.
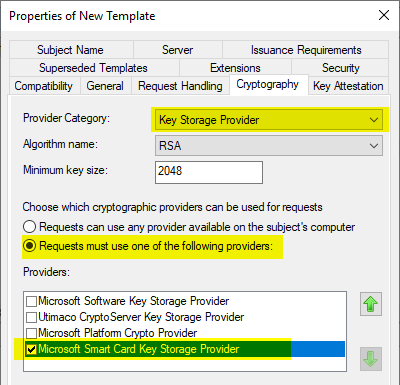
In the "Extensions" tab, the "Issuance Policies" section is edited by clicking on "Edit...".
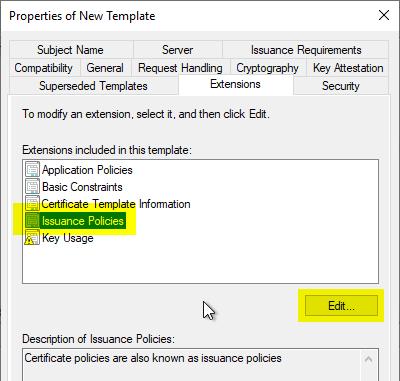
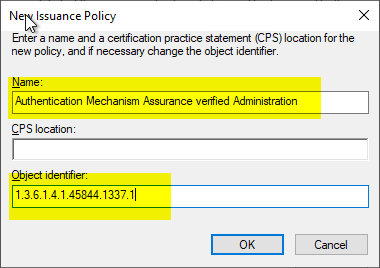
With "Add..." an issuance policy is added.
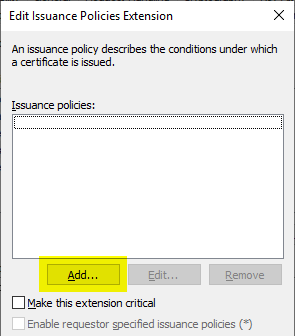
In the following dialog, a new exhibition policy is created by clicking on "New...".
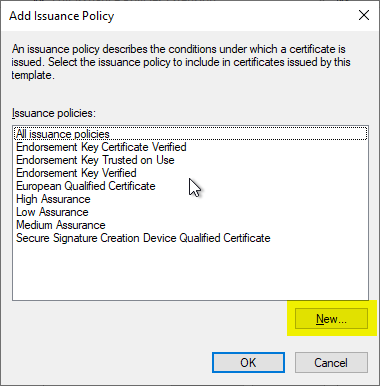
An Object Identifier is automatically created, but should be removed as it is within Microsoft's OID structure.
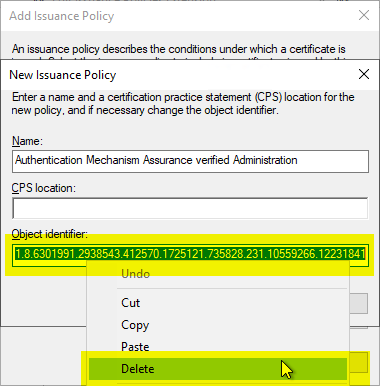
Instead, a separate object identifier should be specified. The exhibition guideline is then assigned a meaningful name.
The name assigned here is stored in the directory service and replicated to all computers within the forest. If a user later views a certificate from this template, the name entered here is displayed in the certificate dialog.
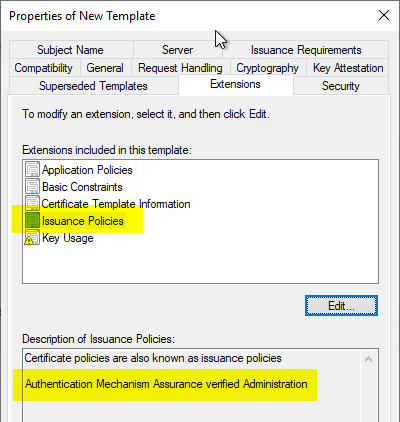
The dialogs can now be closed with "OK". Back in the "Extensions" tab, the name assigned should now be displayed in the "Issuance Policies" section.
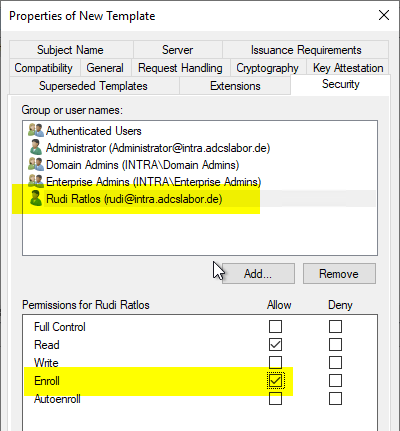
In the "Security" tab, the authorized users get the "Enroll" right
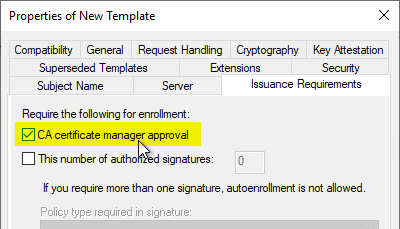
The following step is not necessary but recommended: In the "Issuance Requirements" tab, the check mark for "CA certificate manager approval" should be activated so that a certificate request is not answered directly by the certification authority, but must first be cross-checked by a certificate manager.
Publish the certificate template
The certificate template is now ready for issuance and can be published on the certification authority.
Before Authentication Mechanism Assurance can be used, all other requirements must be met. See the article "Use Authentication Mechanism Assurance (AMA) to secure administrative account logins.„.
One thought on “Konfigurieren einer Zertifikatvorlage für Authentication Mechanism Assurance (AMA)”
Comments are closed.