Assuming one implements Microsoft's Active Directory Administrative Tiering Model, or applies similar hardening measures to one's servers, this will have an impact on NDES components.
The Network Device Enrollment Service (NDES) provides a way for devices that do not have an identifier in Active Directory (for example, network devices such as routers, switches, printers, thin clients, or smartphones and tablets) to request certificates from a certification authority. For a more detailed description, see the article "Network Device Enrollment Service (NDES) Basics„.
Required permissions
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
The service account under which the NDES service is operated (The identity of the IIS application pool) requires the following rights for proper functioning:
On the Certification Authority...
- Access this Computer over the Network (SeNetworkLogonRight) on the certification authority.
On the NDES server...
- Impersonate a Client after Authentication (SeImpersonatePrivilege).
- Log on as a Batch Job (SeBatchLogonRight, in German "Anmelden als Stapenverarbeitungsauftrag"), if it is a domain account or...
- Log on as a Service (SeServiceLogonRight), if it is a Group Managed Service Account (gMSA).
Details: SeNetworkLogonRight
The NDES service account requires the seNetworkLogonRight on the certification authority computer. By default, this is ensured via the "Everyone" entry.
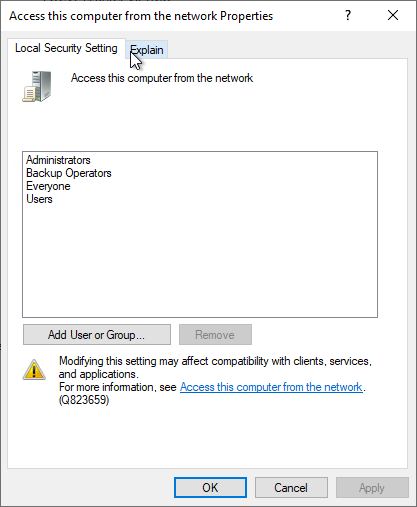
If the seNetworkLogonRight is not assigned, the NDES server will behave as described in the article "The Network Device Enrollment Service (NDES) logs the error message "The Network Device Enrollment Service cannot be started (0x80004005). Unspecified error"" described behave.
Details: SeImpersonatePrivilege
The seImpersonatePrivilege must be set either for the NDES service account, or for the IIS_IUSRS group on the NDES server. By default, this is ensured via the "IIS_IUSRS" entry.
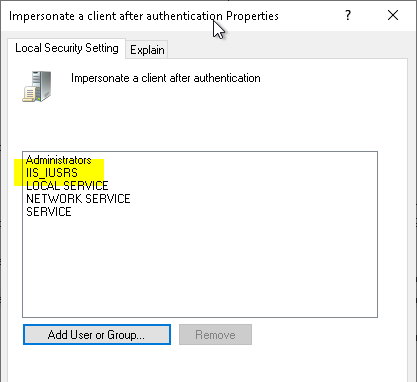
If the SeImpersonatePrivilege is not granted, the NDES server will behave as described in the article "Requesting certificates via Network Device Enrollment Service (NDES) fails with HTTP error code 500" described behave.
Related links:
- Installing the Network Device Enrollment Service (NDES) without Enterprise Administrator permissions
- Configuring the Network Device Enrollment Service (NDES) to work with a Group Managed Service Account (gMSA).
External sources
- Active Directory administrative tier model (Microsoft)
4 thoughts on “Benötigte Windows-Sicherheitsberechtigungen für den Registrierungsdienst für Netzwerkgeräte (NDES)”
Comments are closed.