During penetration tests and also for attackers searching the network for potential targets, insights into the configuration of the certification authority are highly interesting.
In addition to possible misconfigurations, attackers can obtain information about the policy module used on the certification authority.
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
We can find out which certification authorities exist in the network by entering certutil without specifying any arguments:
certutil
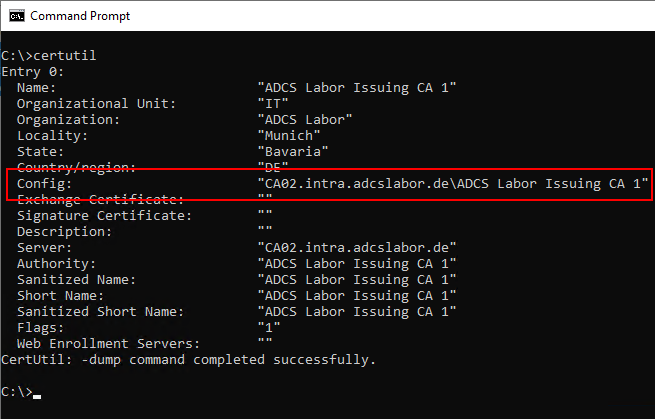
With this information, we can use another certutil command to display the settings of the certification authority:
certutil -v -config "{DNS-Name-CA}\{Common-Name-CA}" -getreg CA
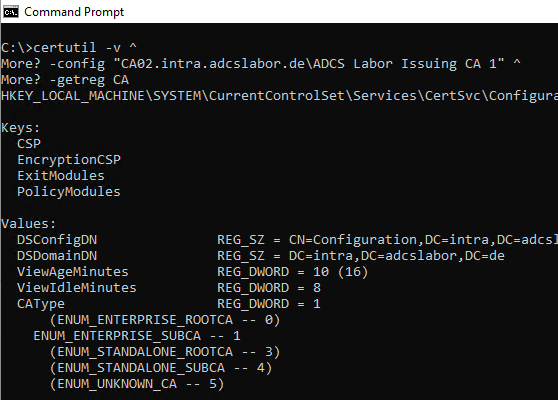
To change the settings of the active Policy Modules this command can be used:
certutil -v -config "{DNS-Name-CA}\{Common-Name-CA}" -getreg Policy
Among other things, it is possible to read out which policy module is being used and whether the highly dangerous flag EDITF_ATTRIBUTESUBJECTALTNAME2 is set.
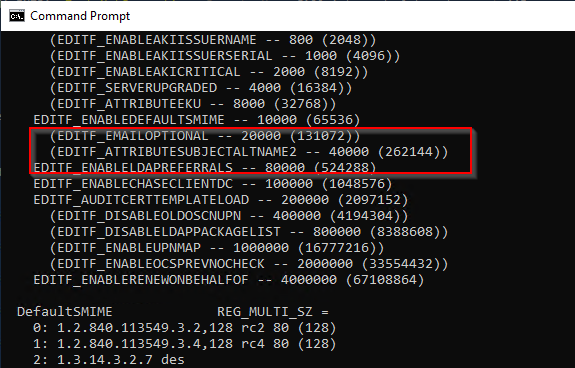
By default, this information can be read by any authenticated user in the network.
A simple method to prevent the reading of the certificate authority configuration
In addition to the certutil integrated in Windows, alternative tools such as the penetration testing tool certipy the ICertAdmin Interfaceto access this information.
As we know, the ICertAdmin interface of the certification authority is not required for daily certification authority operation. It is required for remote administration of the certification authority and for some special cases such as the installation of an NDES server.
Already in the article "Firewall rules required for Active Directory Certificate Services", I therefore recommended preventing access to this port via a firewall. As this port is also used for the SMB file server protocol in addition to RPC named pipes, it also closes other attack vectors (who remembers WannaCry?).
The Windows firewall has a predefined rule for this, which is activated by default. However, as TCP port 445 can also be used by other services (which usually have no business on a certification authority), it can be activated by other firewall rules.
Typically, these are the following firewall rules:
- Certification Authority Enrollment and Management Protocol (CERTSVC-RPC-NP-IN)
- Remote Service Management (NP-In)
- Netlogon Service (NP-In)
- File and Printer Sharing (SMB-In)
- Remote Event Log Management (NP-In)
- File Server Remote Management (SMB-In)
- File and Printer Sharing (SMB-In)
With a simple PowerShell command, we can find and disable all local firewall rules that open TCP port 445.
Get-NetFirewallPortFilter | Where-Object {$_.LocalPort -like "445"} | Disable-NetFirewallRule
Of course, it would be even better to place a network firewall in front of the certification authority. For the local firewall configuration of a certification authority, a group policy should be configured that basically allows everything except the absolutely necessary ports (see here) is blocked.
If we call out our command again, we will run into nothing.
CertUtil: -getreg command FAILED: 0x80070035 (WIN32: 53 ERROR_BAD_NETPATH)
CertUtil: The network path was not found.
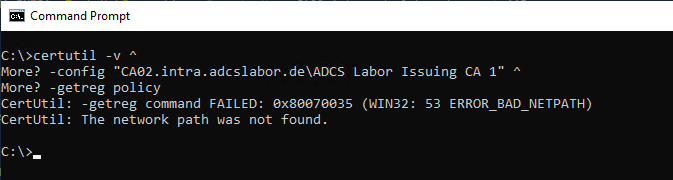
Another option for reading out: Remote registration
Another way to read out the settings of the certification authority is remote registration, which is activated by default on every Windows server.
A remote query against the settings on the certification authority can be carried out as follows:
reg query "\\{DNS-Name-CA}\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\CertSvc\Configuration\{Common-Name-CA}"
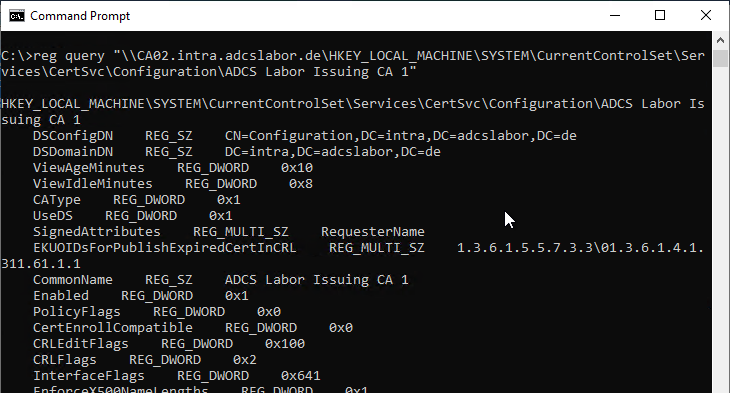
This can be prevented by deactivating and terminating the "Remote registration" service on the certification authority, among other things.
Get-Service -Name RemoteRegistry | Set-Service -StartupType Disabled
Get-Service -Name RemoteRegistry | Stop-Service
Restrictions
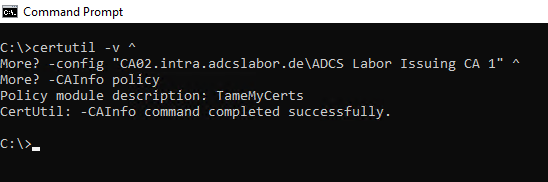
Even if there is no longer access to the ICertAdmin interface and remote registration, some information - such as the active policy module - can still be read out:
certutil -v -config "{DNS-Name-CA}\{Common-Name-CA}" -CAInfo Policy
Complete isolation of the certification authority
One way to further restrict the reading of the certificate authority configuration would be to completely isolate it from the network using only one instance of the Certificate request web services accessible. However, this results in a significantly more complex infrastructure and other challenges such as Kerberos delegation.
Related links:
- Firewall rules required for Active Directory Certificate Services
- Active Directory forest compromised by EDITF_ATTRIBUTESUBJECTALTNAME2 flag
- Role configuration for Network Device Enrollment Service (NDES) fails with error message "The RPC server is unavailable. 0x800706ba (WIN32: 1722 RPC_S_SERVER_UNAVAILABLE)".
- Basics of certificate request via Certificate Enrollment Web Services (CEP, CES) with the MS-XCEP and MS-WSTEP protocols
External sources
- ICertAdmin (certadm.h) - Win32 apps | Microsoft Learn
- ly4k/Certipy: Tool for Active Directory Certificate Services enumeration and abuse
- The red teamer's guide to deception (Lecture at the Troopers 24)
- Certiception: The ADCS honeypot we always wanted (Security Research Labs GmbH)
- srlabs/Certiception: An ADCS honeypot to catch attackers in your internal network.
- ADCS Exploitation Part 3: Living Off The Land | by Giulio Pierantoni | Jun, 2025 | Medium