If you want to use the Trusted Platform Module (TPM) key attestation, you have the option of attesting the TPM via the endorsement certificate (EkCert), among other things. The following describes how to obtain this information.
Check requirements
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
First, check whether an endorsement certificate is stored in the Trusted Platform module at all.
Some TPMs support a hybrid mode, i.e. they can be operated in specification 1.2 as well as in 2.0. The switch is usually made in the BIOS. On Intel-based systems the option is very often called "Intel Platform Trust Technology (Intel PTT)", on AMD-based systems "Firmware TPM" or "fTPM".
The following PowerShell command is used to check if an Endorsement certificate is present in the TPM. The command must be executed with elevated privileges (Run as Administrator).
Get-TpmEndorsementKeyInfo
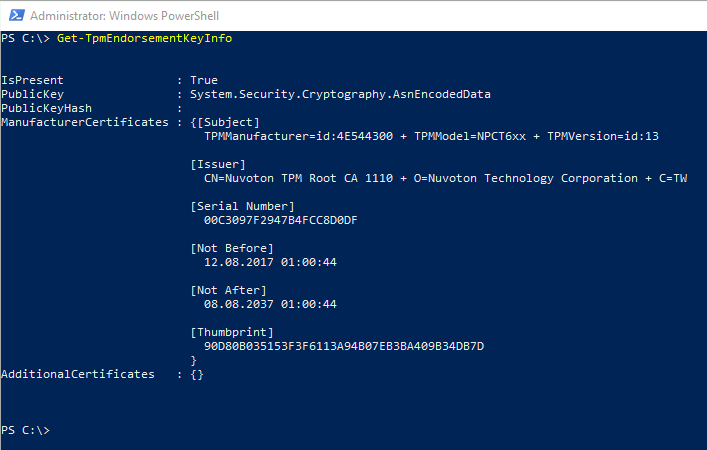
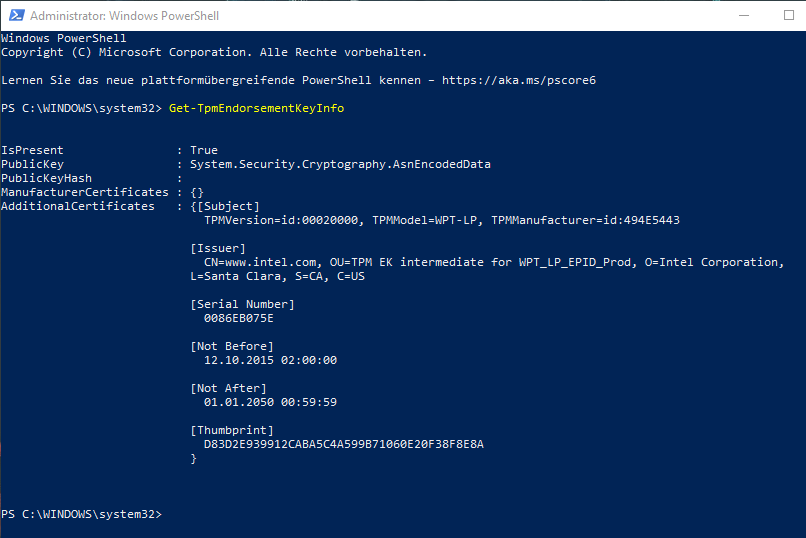
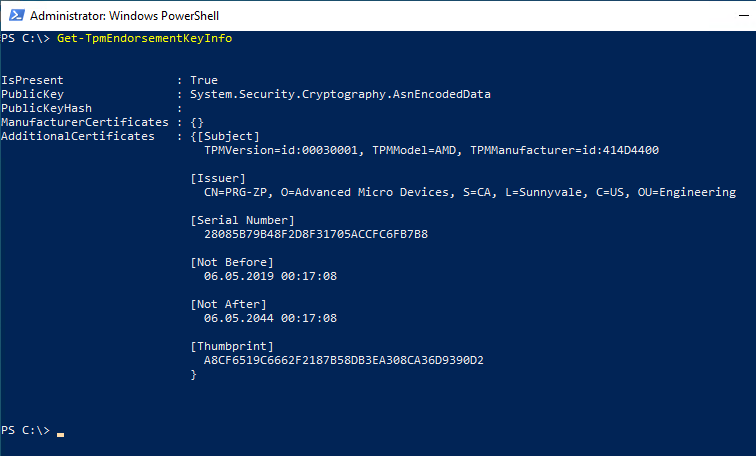
The certificate would show up either under "ManufacturerCertificates" (for a discrete TPM) or under "AdditionalCertificates" (for a TPM integrated into the CPU).
If no endorsement certificate is available, you should check again whether the operating mode can be changed in the BIOS. Unfortunately, not all TPMs have an endorsement certificate, so only the endorsement key can be used in this case (see article "Determine the checksum (hash) of a Trusted Platform (TPM) Endorsement Key„).
Export of the endorsement certificate
The following command for Windows PowerShell exports the endorsement certificate to a file. The command must be executed with elevated privileges (Run as Administrator).
For the ManufacturerCertificates attribute, this command can be used.
(Get-TpmEndorsementKeyInfo).ManufacturerCertificates | Foreach-Object -Process { Set-Content -Value $_.RawData -Encoding Byte -Path "$($_.Thumbprint).crt" -Force }
For the AdditionalCertificates attribute, this command can be used.
(Get-TpmEndorsementKeyInfo).AdditionalCertificates | Foreach-Object -Process { Set-Content -Value $_.RawData -Encoding Byte -Path "$($_.Thumbprint).crt" -Force }
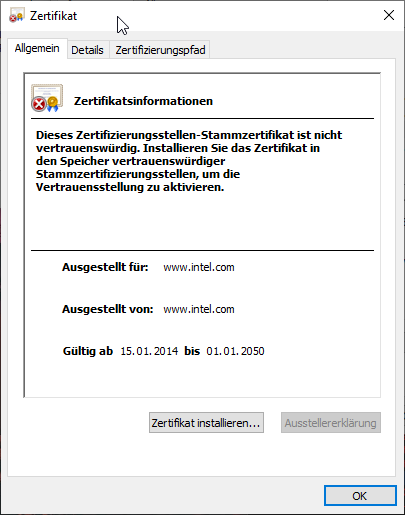
The resulting file can now be opened and inspected by double-clicking on it.
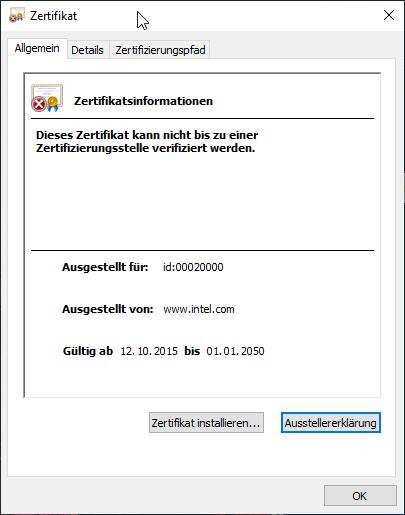
Completing the certificate chain
Since the issuing certification authority is not known, it is indicated that the certificate cannot be traced back to a root certification authority. However, one can manually complete the certificate chain (see article "Basics: Finding certificates and validating the certification path„).
This process can only be successful if the certificates contain a corresponding AIA extension and the address contained in it also works. This can differ depending on the TPM manufacturer. If you are unable to download the certificates in this way, the only option is to contact the manufacturer of the computer or the TPM and ask for the certificates to be sent to you.
To do this, search for the Authority Information Access (AIA) extension in the "Details" tab. There you should find a URL from which you can obtain the certificate authority certificate of the issuing certificate authority.
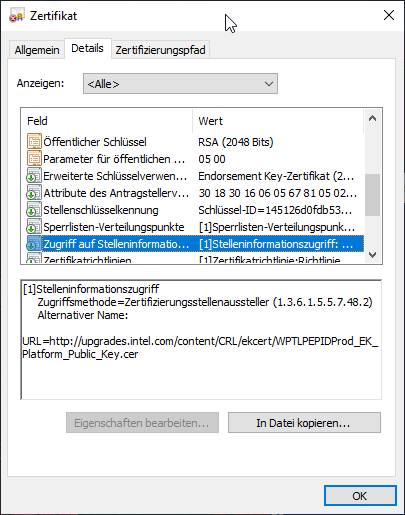
After this is downloaded, you are faced with the same challenge again.
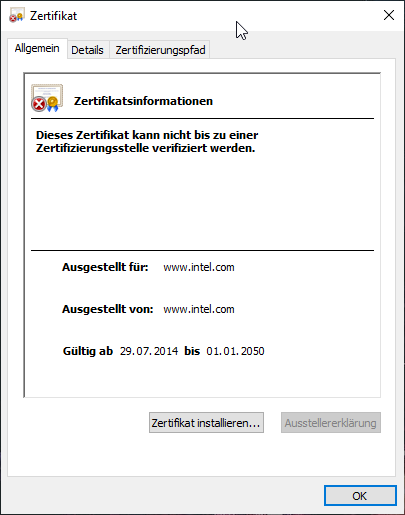
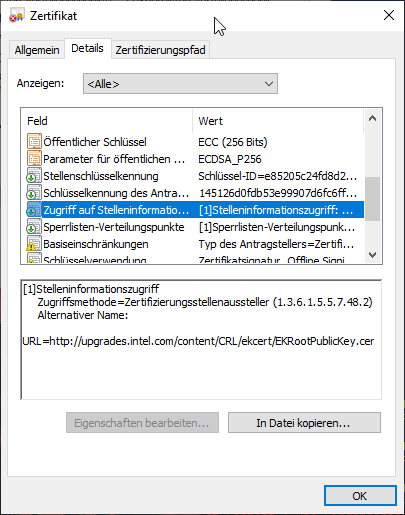
That is why the process is repeated until you end up at the root CA.
Related links:
External sources
- Get-TpmEndorsementKeyInfo (Microsoft)
3 thoughts on “Ermitteln und Exportieren eines Trusted Platform Module (TPM) Endorsement Zertifikats”
Comments are closed.