OCSP responses from a Microsoft OCSP resonder are valid for exactly as long as the underlying revocation list. In some scenarios, you may want to reduce OCSP validity times by using delta CRLs. At the same time, however, no delta CRL should be used for the revocation lists entered in the CDP paths in order to enable a fallback to a CRL with a longer validity.
The Online Responder (Online Certificate Status Protocol, OCSP) is an alternative way of providing revocation status information for certificates. Entities that want to check the revocation status of a certificate do not have to download the complete list of all revoked certificates thanks to OCSP, but can make a specific request for the certificate in question to the online responder. For a more detailed description, see the article "Basics Online Responder (Online Certificate Status Protocol, OCSP)„.
The configuration described here works in practice, but has not been tested by the manufacturer (Microsoft) and is therefore not officially supported.
Certification Authority Configuration: Registration
Delta blacklists must be enabled on the CA.

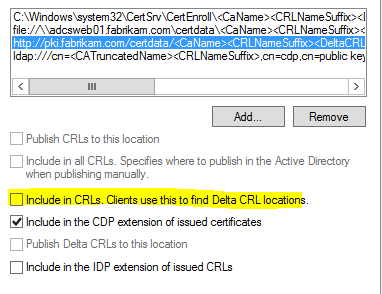
Certification Authority Configuration: Extensions
The option "Include in CRLs. Clients use this to find Delta CRL locations." must be disabled for each published (LDAP or HTTP) CDP path so that the CRL does not contain a "Freshest CRL" extension.
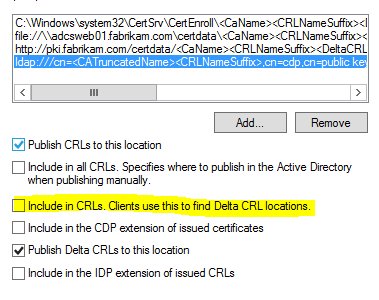
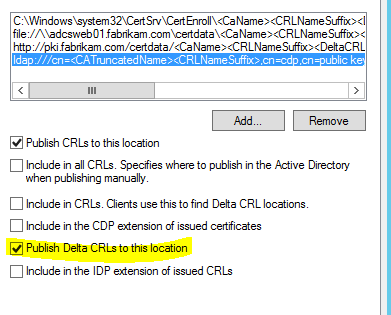
However, at the same time you enable the "Publish Delta CRLs to this location" function on the locations for CDP (LDAP or File).
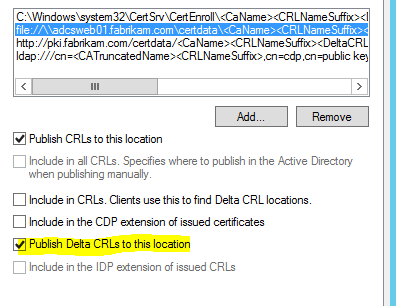
The CA service must be restarted once after the change. A delta CRL must then be generated by publishing a new CRL.
The Base CRL should not include a "Freshest CRL" extension.
Configuration OCSP Responder
The revocation providers must now be filled manually on the OCSP responder, since the base revocation lists deliberately contain no reference to the delta CRL.
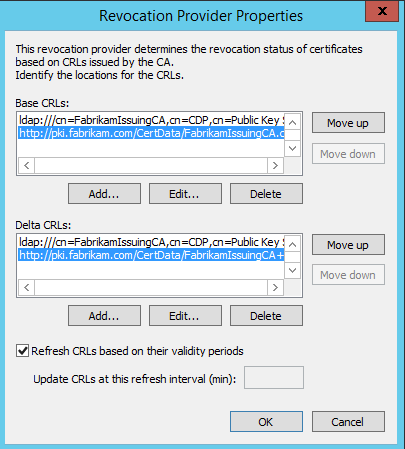
Example
Basic revocation list
- ldap:///cn=FabrikamIssuingCA,cn=CDP,cn=Public Key Services,CN=services,CN=Configuration,DC=Fabrikam,DC=com?certificateRevocationList?base?objectClass=cRLDistributionPoint
- http://pki.fabrikam.com/CertData/FabrikamIssuingCA.crl
Delta revocation list
- ldap:///cn=FabrikamIssuingCA,cn=CDP,cn=Public Key Services,CN=services,CN=Configuration,DC=Fabrikam,DC=com?deltaRevocationList?base?objectClass=cRLDistributionPoint
- http://pki.fabrikam.com/CertData/FabrikamIssuingCA+.crl
If the Delta CRL should expire, CAPI2 will fall back to the Base CRL.
---------------- Certificate AIA ----------------
Verified "Certificate (0)" Time: 0
[0.0] http://pki.fabrikam.com/certdata/FabrikamIssuingCA.crt
Verified "Certificate (0)" Time: 0
[1.0] ldap:///cn=FabrikamIssuingCA,cn=aia,cn=publickeyservices,cn=services,CN=Configuration,DC=Fabrikam,DC=com?cACertificate?base?objectClass=certificationAuthority
---------------- Certificate CDP ----------------
Verified "Base CRL (1c)". Time: 0
[0.0] http://pki.fabrikam.com/certdata/FabrikamIssuingCA.crl
Verified "Base CRL (1c)". Time: 0
[1.0] ldap:///cn=FabrikamIssuingCA,cn=cdp,cn=publickeyservices,cn=services,CN=Configuration,DC=Fabrikam,DC=com?certificateRevocationList?base?objectClass=cRLDistributionPoint
---------------- Base CRL CDP ----------------
No URLs "None" Time: 0
---------------- Certificate OCSP ----------------
Expired "OCSP" Time: 0
[0.0] http://ocsp.fabrikam.com/ocsp
[...]
Verified Issuance Policies: All
Verified Application Policies:
1.3.6.1.4.1.311.21.5 Private Key Archival
Leaf certificate revocation check passed
CertUtil: -verify command completed successfully
One thought on “Kombination Onlineresponder (OCSP) mit Delta CRL und Sperrlistenverteilpunkt (CDP) ohne Deltasperrliste für gesteigerte Resilienz”
Comments are closed.