Assume the following scenario:
- An Active Directory integrated certificate authority (Enterprise CA) is integrated in the network.
- The certification authority was migrated to a new server (see also article "Migration of an Active Directory integrated certification authority (Enterprise Certification Authority) to another server„).
- When publishing the certificate templates, one notices that only the Standard certificate templates to be selected for publication. Own certificate templates are not displayed.
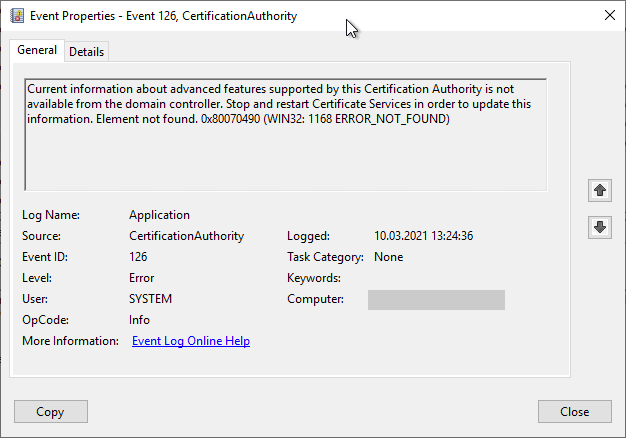
The Certification Authority will use the Event no. 126 log.
Current information about advanced features supported by this Certification Authority is not available from the domain controller. Stop and restart Certificate Services in order to update this information. Element not found. 0x80070490 (WIN32: 1168 ERROR_NOT_FOUND)
Cause
Up to Windows Server 2008 R2 there was a distinction whether one had installed the "Standard Edition" or the "Enterprise Edition" (for Windows 2000: Advanced Server) of the operating system. Only if the certificate authority was installed on the "Enterprise Edition" of the operating system could you use your own certificate templates.
Do not confuse the terms "Enterprise Edition" and "Enterprise Certification Authority". In the first case the variant of the operating system is meant, in the second case the installation type of the certification authority.
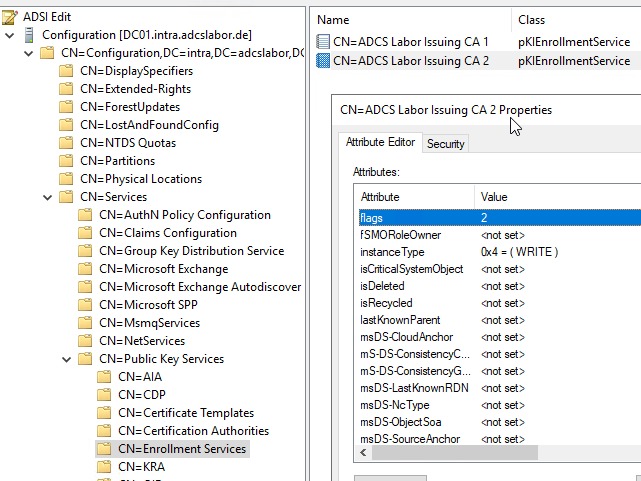
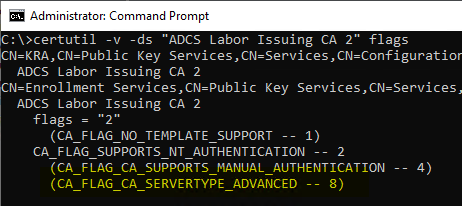
The distinction whether "Standard Edition" or "Enterprise Edition" is realized by a flag on the pKIEnrollmentService object. An Active Directory Enterprise CA should have the following flags set:
- CA_FLAG_SUPPORTS_NT_AUTHENTICATION (0x2)
- CA_FLAG_CA_SERVERTYPE_ADVANCED (0x8)
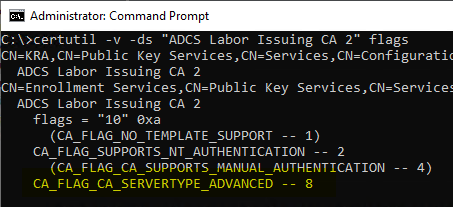
So the resulting value in the "flags" attribute on the pKIEnrollmentService object of the certification authority should be "10". For example, if the value is set to "2", the CA_FLAG_CA_SERVERTYPE_ADVANCED Flag not set.
There is also the possibility to have the values resolved with the following command line command:
certutil -v -ds "{common-name-of-the-CA}" flags
Also, when migrating the certification authority (which involves reinstalling the certification authority role on the new server), the CA_FLAG_CA_SERVERTYPE_ADVANCED flag may no longer be set.
You can change the value directly in the ADSI editor or with the following command line command on the certification authority, which updates the "flags" attribute at the next start of the certification authority service:
certutil -setreg CA\SetupStatus +SETUP_UPDATE_CAOBJECT_SVRTYPE
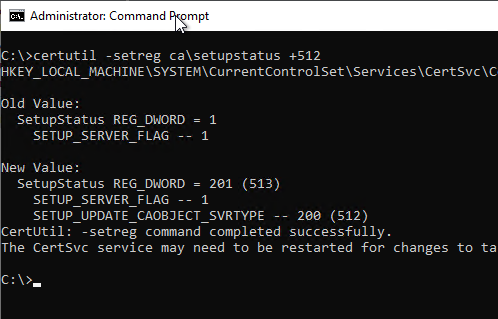
In both cases, the certification authority service must be restarted so that the changed settings are read in.
Now the flag should be resolved correctly and the custom certificate templates should be selectable for publishing.
Related links:
- Migration of an Active Directory integrated certification authority (Enterprise Certification Authority) to another server
- Requesting a certificate fails with the error message "A valid certification authority (CA) configured to issue certificates based on this template cannot be located, or the CA does not support this operation, or the CA is not trusted."
- (Re-)Installing the Microsoft Standard Certificate Templates
- Description of certificate template generations
- Certificate Enrollment Policy Service does not display certificate templates configured for compatibility with Windows Server 2016 or Windows 10
External sources
- How to troubleshoot Certificate Enrollment in the MMC Certificate Snap-in (Microsoft)
- You cannot add V2 or V3 templates after an inplace upgrade was performed using Windows Server 2008 enterprise CA (Microsoft, archive.org)
- You cannot add V2 or V3 templates after an inplace upgrade was performed on a Windows Server 2008 enterprise CA (Microsoft, archive.org)
4 thoughts on “Nach Installation oder Migration einer Zertifizierungsstelle auf einen neuen Server können keine eigenen Zertifikatvorlagen mehr veröffentlicht werden”
Comments are closed.